The LightSpy surveillance framework has considerably developed its operational capabilities, now supporting over 100 instructions to infiltrate Android, iOS, Home windows, macOS, and Linux techniques, and routers, based on new infrastructure evaluation.
First documented in 2020, this modular malware has shifted from concentrating on messaging functions to specializing in social media database extraction and cross-platform surveillance, marking a harmful escalation in its cyberespionage capabilities.
From Messaging Apps to Social Media Databases
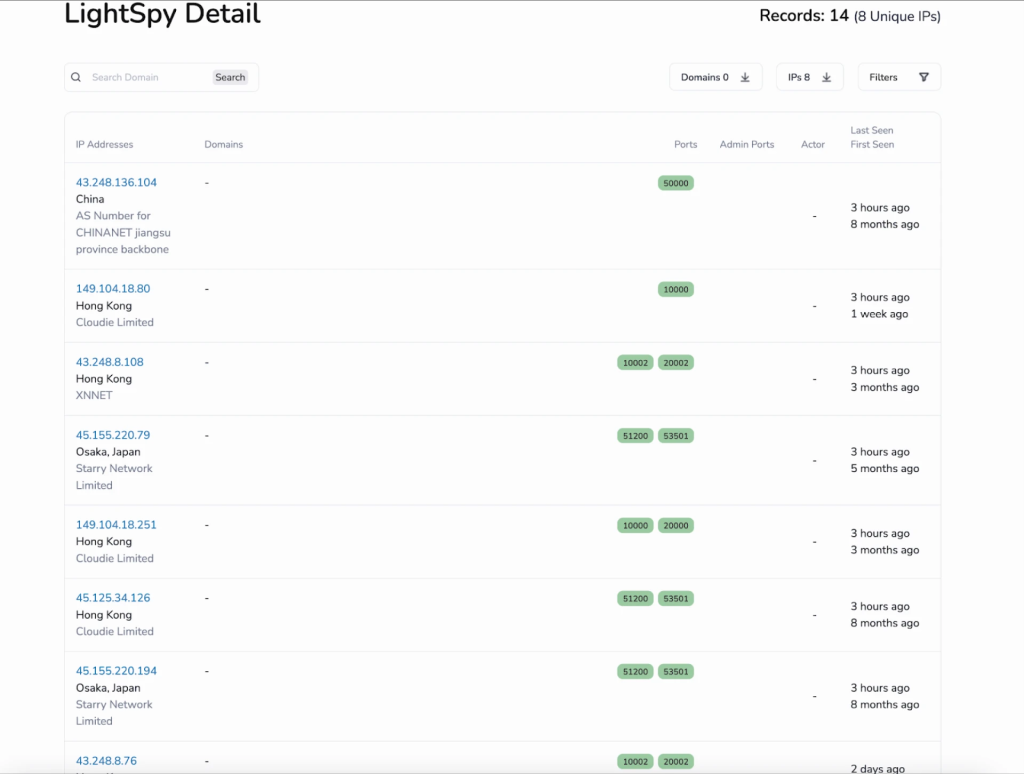
LightSpy’s operators have expanded their command repertoire from 55 to greater than 100 directives, with newly noticed infrastructure at 149.104.18[.]80:10000 revealing tactical shifts.

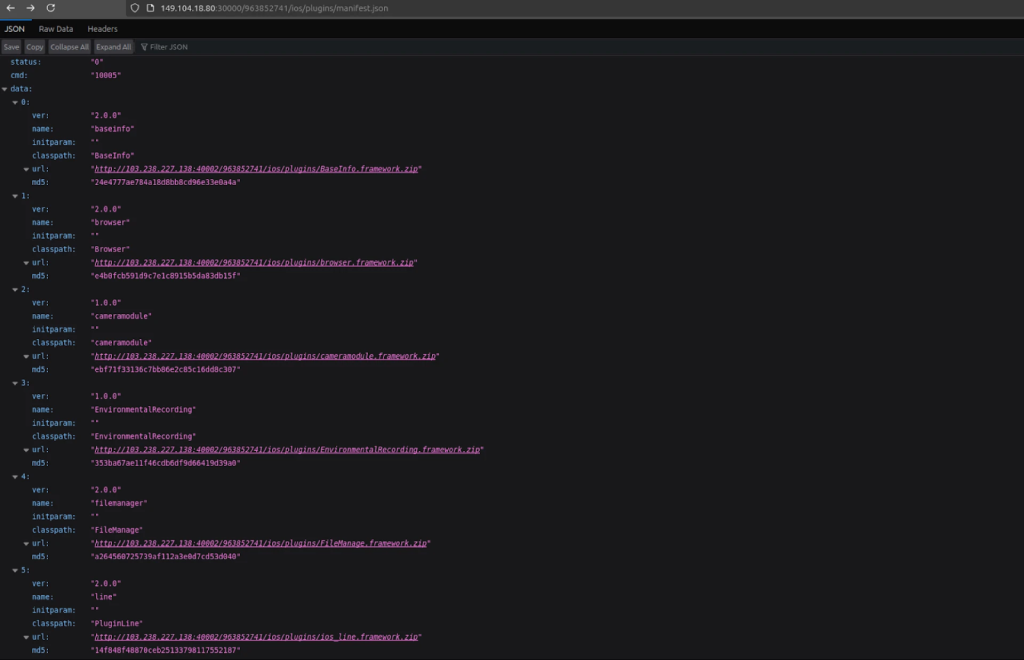
The place earlier campaigns centered on extracting knowledge from Telegram, WeChat, and WhatsApp, the framework now explicitly targets Fb and Instagram database information by way of instructions 83001 and 830021.
This allows attackers to exfiltrate non-public messages, contact lists, and account metadata—a strategic transfer that capitalizes on the pervasive use of those platforms for each private {and professional} communications.
The command checklist modifications replicate an operational emphasis on granular knowledge management, together with “传输控制” (transmission administration) and “上传插件版本详细信息” (importing plugin model particulars), suggesting improved coordination between compromised gadgets and command servers.

Analysts be aware this shift permits menace actors to prioritize high-value targets whereas sustaining persistent entry throughout diversified environments.
Cross-Platform Surveillance Capabilities
LightSpy’s newest iteration demonstrates alarming versatility, with plugins and instructions tailor-made for Home windows, macOS, Linux, and embedded techniques.
Home windows-specific DLL information uncovered in current scans reveal capabilities spanning audio recording (“audiox64m.dll”), keystroke logging (“KeyLogLib64m.dll”), USB gadget monitoring (“usbx64m.dll”), and display seize (“Capx64m.dll”).

These plugins comply with a developmental sample seen of their PDB paths (W:ykBigfootbin*.pdb), indicating an organized codebase maintained for long-term deployment1.
For macOS and Linux targets, whereas express plugins weren’t recognized within the newest server snapshots, the expanded command checklist contains directives for router exploitation—a typical pivot level to bridge into enterprise networks.
This multi-OS concentrating on technique complicates protection efforts, as safety groups should account for each endpoint and community infrastructure vulnerabilities.

Lively LightSpy command-and-control (C2) servers proceed to leverage Hong Kong-based internet hosting supplier Cloudie Restricted, with 149.104.18[.]80 working on ports 80, 443, 10000, 30000, and 40002.
![Screenshot of login panel at 149.104.18[.]80.](https://gbhackers.com/wp-content/uploads/2025/02/image-72-1024x484.png)
![Screenshot of login panel at 149.104.18[.]80.](https://gbhackers.com/wp-content/uploads/2025/02/image-72-1024x484.png)
The usage of non-standard ports (e.g., 30000 for iOS plugin model checks) and recurring endpoint patterns like /963852741 suggests automated deployment scripts designed to bypass easy port-based detection guidelines.
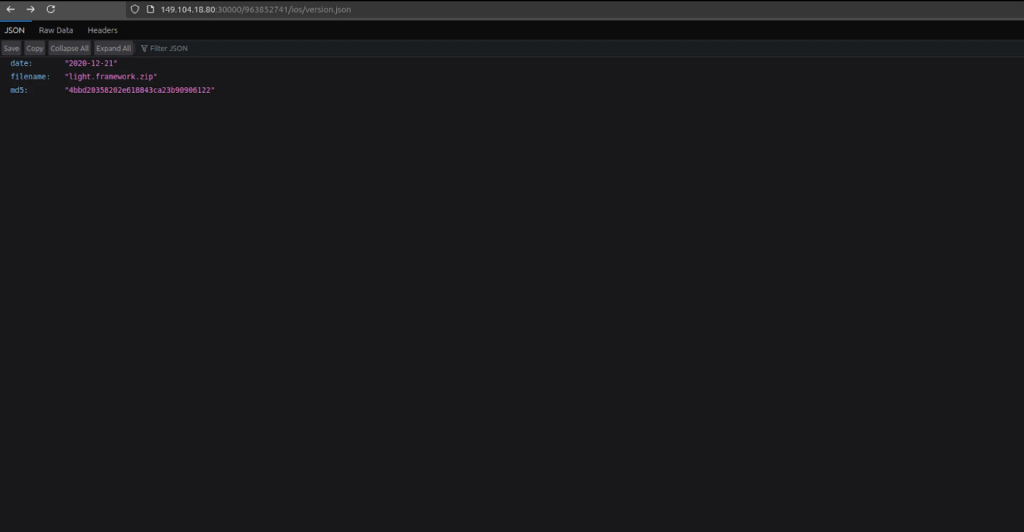
Researchers recognized temporal discrepancies in core module deployment dates throughout ports, with model.json information on port 30000 referencing a 2020-12-21 construct date, whereas port 40002 indicated a beforehand undocumented 2021-12-31 model (MD5:81d2bd4781e3753b508ff6d966dbf160).
These inconsistencies level to both model fragmentation throughout campaigns or deliberate makes an attempt to mislead forensic investigators.
Administrative Panel Publicity
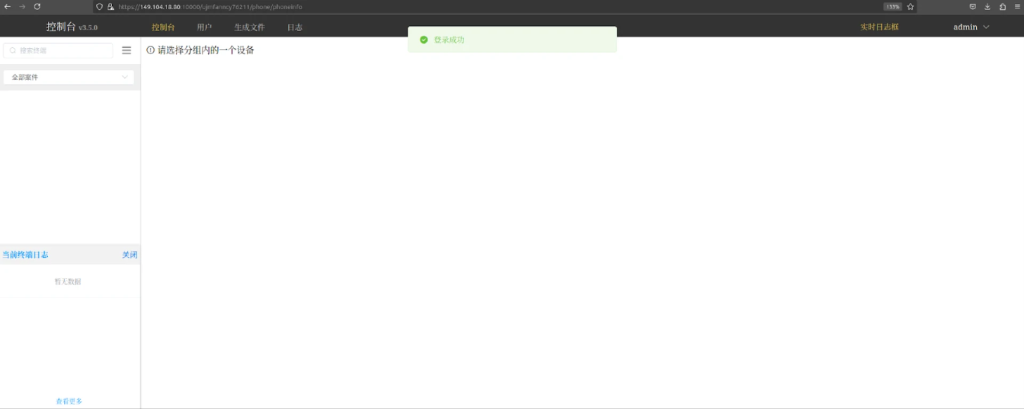
A misconfigured admin panel at /third_login/:username briefly uncovered LightSpy’s operational dashboard, branded as “Console v3.5.0”1. The interface supplies real-time gadget administration, file technology controls, and entry to terminal logs—capabilities aligned with state-sponsored surveillance toolkits.
Authentication endpoints like /thd/login and /remote_csm reveal layered entry controls, doubtlessly permitting completely different operator roles to handle compromised gadgets.

Notably, the panel’s “Generate Recordsdata” operate could correlate with LightSpy’s plugin distribution system, which hosts malicious DLLs and framework elements on auxiliary servers like 103.238.227[.]1381.
This server, linked to the area hk.cdn[.]cat, underscores the attackers’ reliance on benign-looking infrastructure to obscure malicious payload deliveries.
Mitigation Methods and Defensive Countermeasures
Forensic Detection and Historic Evaluation
Organizations are suggested to audit historic system logs for indicators equivalent to:
- MD5 hashes 81d2bd4781e3753b508ff6d966dbf160 (2021-12-31 core model)
- Filesystem entries referencing W:ykBigfootbin growth paths
- Unauthorized entry to Fb/Instagram SQLite databases
Community visitors patterns displaying repeated GET requests to /ujmfanncy76211/front_api or POSTs to /third_login warrant instant incident response escalation.
LightSpy’s transformation right into a cross-platform espionage toolkit highlights the rising sophistication of cyberespionage campaigns.
By concentrating on social media databases and refining its plugin structure, the framework poses important dangers to each particular person privateness and organizational safety.
Defenders should undertake proactive searching methods centered on behavioral indicators relatively than static IOCs, as LightSpy’s operators proceed to adapt their infrastructure and concentrating on methodologies.
With its expanded command set and multi-OS attain, this malware household represents a persistent menace that calls for coordinated detection efforts throughout all main platforms.
Free Webinar: Higher SOC with Interactive Malware Sandbox for Incident Response, and Risk Searching - Register Right here
