
A brand new malware known as FinalDraft has been utilizing Outlook e mail drafts for command-and-control communication in assaults towards a ministry in a South American nation.
The assaults have been found by Elastic Safety Labs and depend on an entire toolset that features a customized malware loader named PathLoader, the FinalDraft backdoor, and a number of post-exploitation utilities.
The abuse of Outlook, on this case, goals to attain covert communications, permitting the attackers to carry out knowledge exfiltration, proxying, course of injection, and lateral motion whereas leaving minimal doable traces.
Assault chain
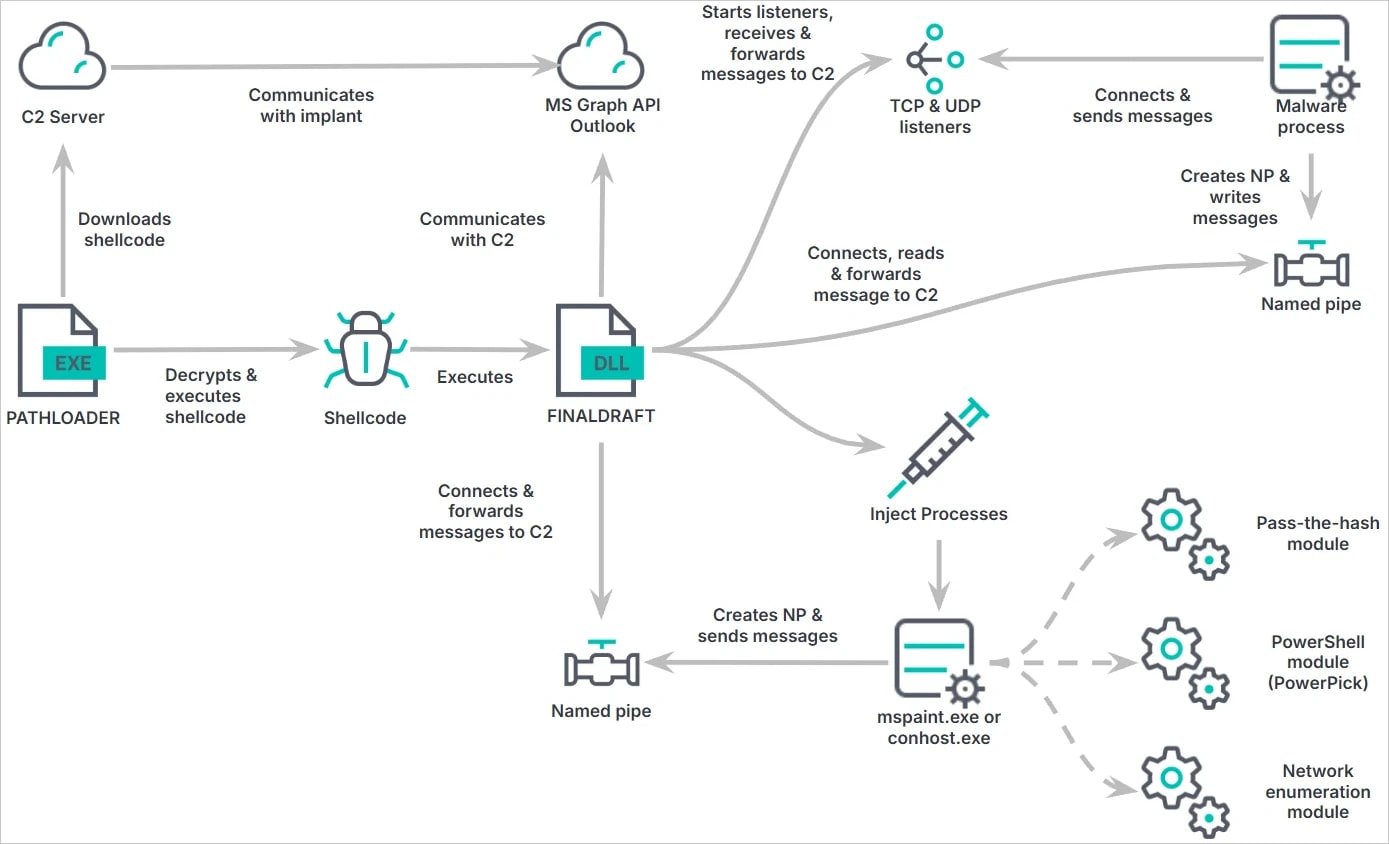
The assault begins with the risk actor compromising the targer’s system with PathLoader, a small executable file that executes shellcode, together with the FinalDraft malware, retrieved from the attacker’s infrastructure.
PathLoader incorporates protections towards static evaluation by performing API hashing and utilizing string encryption.
FinalDraft is used for knowledge exfiltration and course of injection. After loading the configuration and producing a session ID, the malware establishes communication via Microsoft Graph API, by sending and receiving instructions via Outlook e mail drafts.
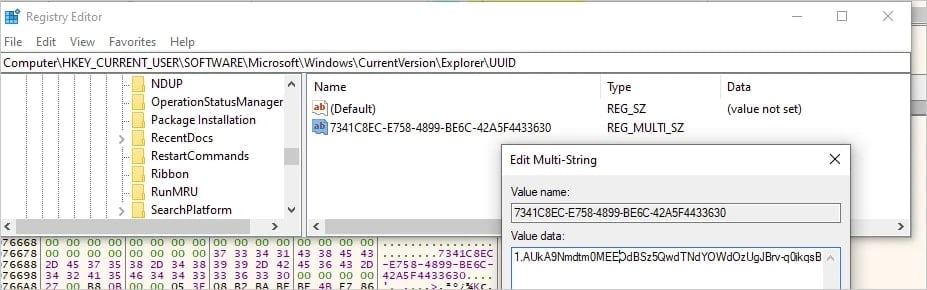
FinalDraft retrieves an OAuth token from Microsoft utilizing a refresh token embedded in its configuration, and shops it within the Home windows Registry for persistent entry.
Supply: Elastic Safety
Through the use of Outlook drafts as an alternative of sending emails, it avoids detection and blends into regular Microsoft 365 site visitors.
Instructions from the attacker are hidden in drafts (r_
FinalDraft helps a complete of 37 instructions, crucial of them being:
- Information exfiltration (recordsdata, credentials, system data)
- Course of injection (operating payloads in authentic processes like mspaint.exe)
- Go-the-Hash assaults (stealing authentication credentials for lateral motion)
- Community proxying (creating covert community tunnels)
- File operations (copying, deleting, or overwriting recordsdata)
- PowerShell execution (with out launching powershell.exe)
Elastic Safety Labs additionally noticed a Linux variant of FinalDraft, which might nonetheless use Outlook through REST API and Graph API, in addition to HTTP/HTTPS, reverse UDP & ICMP, bind/reverse TCP, and DNS-based C2 alternate.
Supply: Elastic Safety
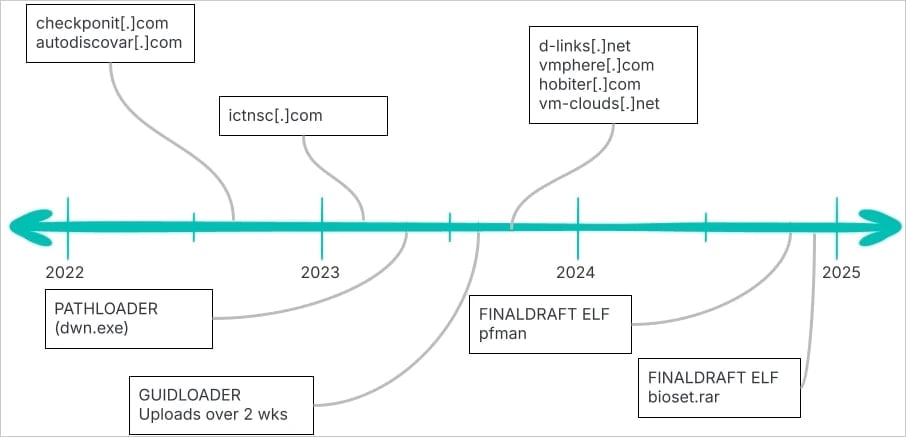
The researchers current the assault marketing campaign, dubbed REF7707, in a separate report that describes a number of opsec errors which can be in distinction with the superior intrusion set used, and which led to the attacker’s publicity.
REF7707 is a cyber-espionage marketing campaign targeted on a South American international ministry, however evaluation of the infrastructure revealed hyperlinks to Southeast Asian victims, suggesting a broader operation.
The investigation additionally uncovered one other beforehand undocumented malware loader used within the assaults, named GuidLoader, succesful to decrypt and execute payloads in reminiscence
Supply: Elastic Safety
Additional evaluation confirmed the attacker’s repeated concentrating on of high-value establishments through compromised endpoints in telecommunications and web infrastructure suppliers in Southeast Asia.
Moreover, a Southeast Asian college’s public-facing storage system was used to host malware payloads, suggesting prior compromise or a provide chain foothold.
YARA guidelines to assist defenders detect Guidloader, PathLoader, and FinalDraft, can be found on the backside of Elastic’s stories [1, 2].
