
Over twelve thousand GFI KerioControl firewall cases are uncovered to a vital distant code execution vulnerability tracked as CVE-2024-52875.
KerioControl is a community safety suite that small and medium-sized companies use for VPNs, bandwidth administration, reporting and monitoring, site visitors filtering, AV safety, and intrusion prevention.
The flaw in query was found in mid-December by safety researcher Egidio Romano (EgiX), who demonstrated the potential for harmful 1-click RCE assaults.
GFI Software program launched a safety replace for the issue with model 9.4.5 Patch 1 on December 19, 2024, but three weeks later, based on Censys, over 23,800 cases remained weak.
Early final month, Greynoise revealed it had detected lively exploitation makes an attempt leveraging Romano’s proof-of-concept (PoC) exploit, aimed toward stealing admin CSRF tokens.
Regardless of the warning about lively exploitation, risk monitoring service The Shadowserver Basis now experiences seeing 12,229 KerioControl firewalls uncovered to assaults leveraging CVE-2024-52875.
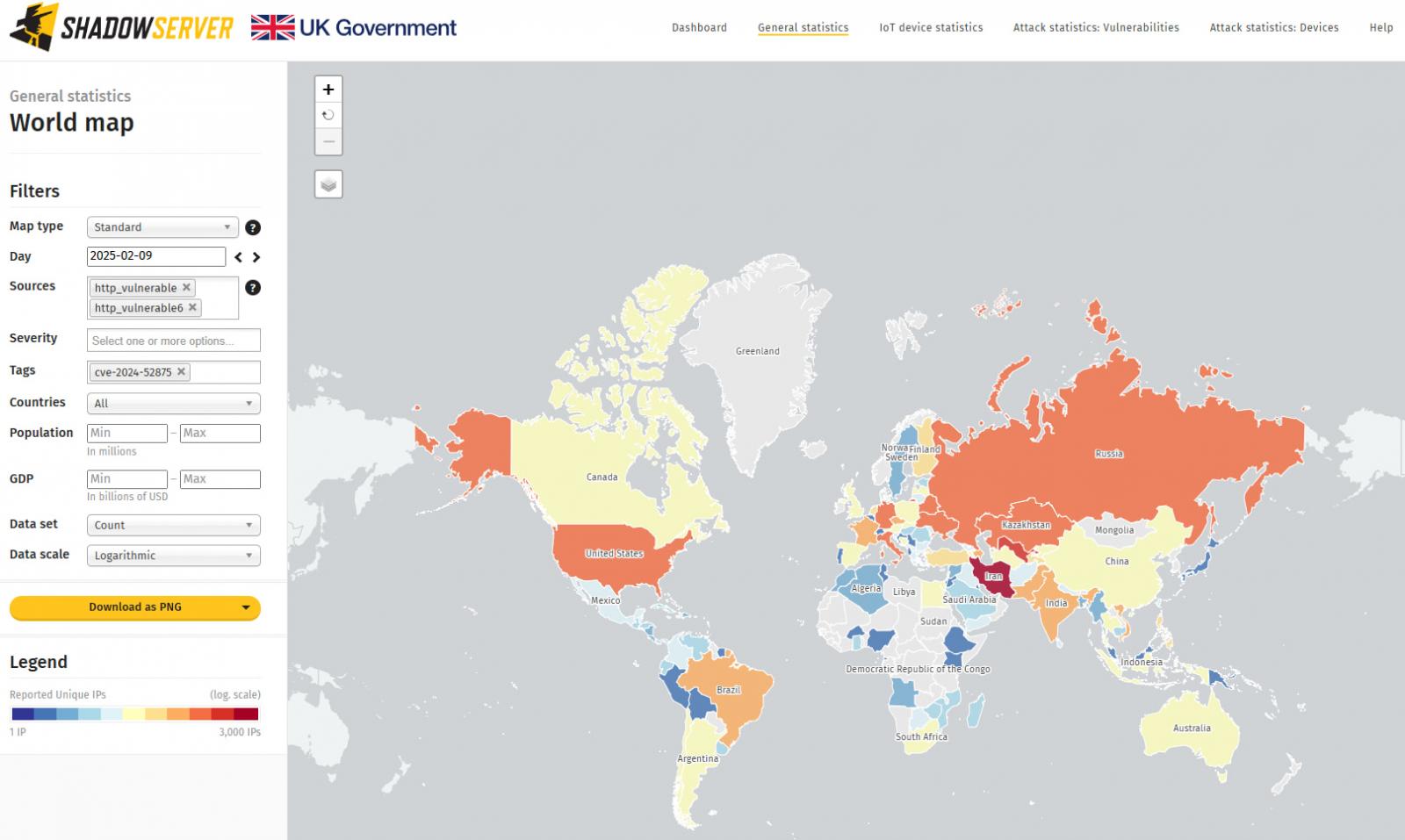
Supply: The Shadowserver Basis
Most of those cases are positioned in Iran, the USA, Italy, Germany, Russia, Kazakhstan, Uzbekistan, France, Brazil, and India.
With the existence of a public PoC for CVE-2024-52875, the necessities for exploitation are low, permitting even unskilled hackers to hitch the malicious exercise.
“Consumer enter handed to those pages through the “dest” GET parameter shouldn’t be correctly sanitized earlier than getting used to generate a “Location” HTTP header in a 302 HTTP response,” explains Egidio Romano.
“Particularly, the appliance doesn’t accurately filter/take away linefeed (LF) characters. This may be exploited to carry out HTTP Response Splitting assaults, which in flip may enable to hold out Mirrored Cross-Web site Scripting (XSS) and presumably different assaults.”
“NOTE: the Mirrored XSS vector is likely to be abused to carry out 1-click Distant Code Execution (RCE) assaults.”
If you have not utilized the safety replace but, it’s strongly suggested that you just set up KerioControl model 9.4.5 Patch 2, launched on January 31, 2025, which accommodates extra safety enhancements.

