The Mirai botnet unleashed a record-breaking Distributed Denial of Service (DDoS) assault on October 29, 2024, peaking at an astonishing 5.6 terabits per second (Tbps).
This mega surge of malicious site visitors focused a Cloudflare buyer, an Web Service Supplier (ISP) based mostly in Jap Asia, marking the biggest DDoS assault ever recorded.

Understanding DDoS Assaults
DDoS assaults goal to overwhelm a goal’s on-line providers, rendering them inoperable by flooding them with extreme site visitors.
The Mirai botnet, notorious for exploiting Web of Issues (IoT) gadgets, is especially infamous for its skill to assemble huge armies of compromised gadgets to execute such assaults.
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Menace Intelligence Lookup - Strive for Free
On this occasion, the assault originated from over 13,000 IoT gadgets, showcasing the botnet’s relentless capabilities.
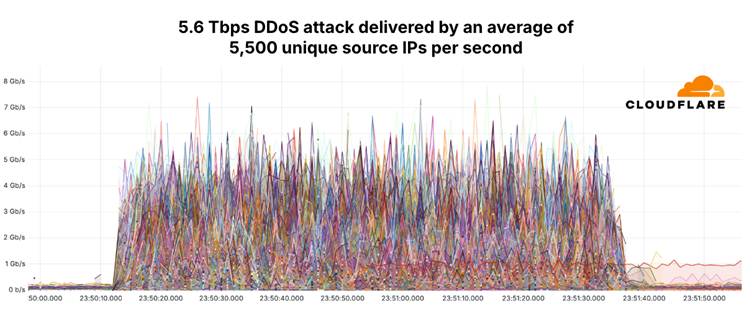

The historic assault lasted a mere 80 seconds, but it demonstrated the sheer quantity of site visitors that fashionable DDoS assaults can generate.
Cloudflare’s infrastructure dealt with the assault autonomously, requiring no human intervention. The assault’s effectivity was astonishing, with every of the distinctive supply IP addresses contributing lower than 8 Gbps to the flood, averaging round 1 Gbps per second.
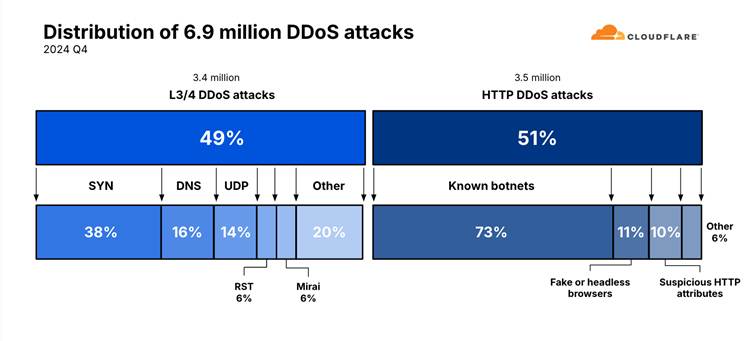
In accordance with Cloudflare’s evaluation, 49% of the DDoS assaults within the fourth quarter of 2024 had been Layer 3/Layer 4 assaults, whereas 51% had been HTTP-based assaults.
The Mirai botnet’s skill to launch such a robust assault factors to an alarming pattern in DDoS methodologies, notably as botnets develop and evolve in response to safety measures.
The current quarter witnessed a stark improve in hyper-volumetric assaults, with incidents exceeding 1 Tbps rising by an unprecedented 1,885% in comparison with the earlier quarter.
This shift towards larger bandwidth assaults signifies an escalation within the scale and class of DDoS threats, which poses important challenges for community safety suppliers and companies alike.
The October 29 incident has underscored the significance of strong and proactive DDoS mitigation methods.
With the scale of potential DDoS assaults growing dramatically, standard safety mechanisms have gotten much less efficient, necessitating the deployment of superior options able to managing large site visitors volumes.
The Function of IoT Gadgets
The Mirai botnet’s involvement on this report assault highlights a persistent vulnerability within the panorama of cybersecurity.
Many IoT gadgets—together with good TVs and residential home equipment—typically lack ample safety measures, making them prime targets for hijacking.
This incident serves as a name to motion for producers and shoppers alike to prioritize safety within the design and use of IoT gadgets, thereby lowering the danger of them being co-opted into botnets.
Within the aftermath of the 5.6 Tbps assault, specialists emphasize the need for organizations to implement complete DDoS safety methods earlier than experiencing an assault.
Cloudflare reported a notable improve in Ransom DDoS incidents, notably through the peak on-line buying season of late 2024, as these assaults can severely disrupt companies and trigger substantial monetary losses.
Cloudflare’s defenses proved efficient through the assault, showcasing the capabilities of automated, real-time responses to DDoS threats.

Their autonomous techniques managed to mitigate the assault seamlessly, reflecting the necessity for organizations to put money into strong cybersecurity infrastructures that may adapt to and counter rising threats.

The record-breaking 5.6 Tbps DDoS assault dropped at gentle the escalating challenges in cyber protection, notably relating to the vulnerabilities posed by unsecured IoT gadgets.
This incident serves as a vital reminder of the need for complete, automated DDoS safety options to safeguard towards the rising menace panorama.
The way forward for cybersecurity hinges on our skill to adapt, innovate, and reply swiftly to those more and more subtle assaults.
Integrating Software Safety into Your CI/CD Workflows Utilizing Jenkins & Jira -> Free Webinar

