As a devoted bug bounty hunter with an enviable monitor report on BugCrowd, Abdullah Nawaf, Full full-time bug Bounty Hunter, thrives on the fun of discovery and the problem of discovering high-impact vulnerabilities.
Just lately, alongside his colleague Orwa Atyat, they achieved a notable success: turning a restricted path traversal vulnerability right into a fully-fledged distant code execution (RCE) exploit, incomes a beneficiant bounty of $40,000. Right here’s an in depth account of their journey.
Our journey started with commonplace reconnaissance on a goal subdomain, particularly http://admin.goal.com:8443. Initially met with a 404 response, many hunters would have moved on.
Nevertheless, his instincts advised me to dig deeper. Using fuzzing methods on the URL, they found an endpoint at /admin/Obtain, which returned a 200 OK standing however an empty response, as per the report by Medium. This hinted at a doubtlessly exploitable characteristic.
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Risk Intelligence Lookup - Attempt for Free
Discovering Vulnerabilities
Delving deeper into the admin path, he started testing for Native File Inclusion (LFI) and path traversal vulnerabilities. His exams revealed that the /obtain endpoint accepted a parameter known as filename.
When he accessed http://admin.goal.com:8443/admin/obtain?filename=/js/principal.js, it displayed the contents of the JavaScript file.
Nevertheless, the limitation was clear: the perform solely allowed entry to information inside the /admin/ listing.
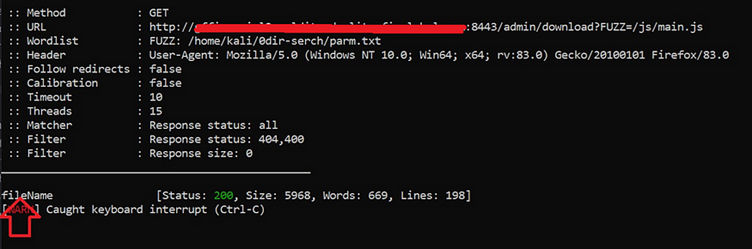

Undeterred, he tried to entry /WEB-INF/net.xml, a file recognized to include very important info. This strategic exploration proved fruitful, as he unearthed three URLs, together with one for an /incident-report.
Upon visiting this endpoint, he triggered the obtain of a reside log file—an surprising twist that will lead us down a path of great discovery.

Escalating the Influence
Contained in the log file, he stumbled upon delicate information: admin credentials, together with an MD5-hashed password.
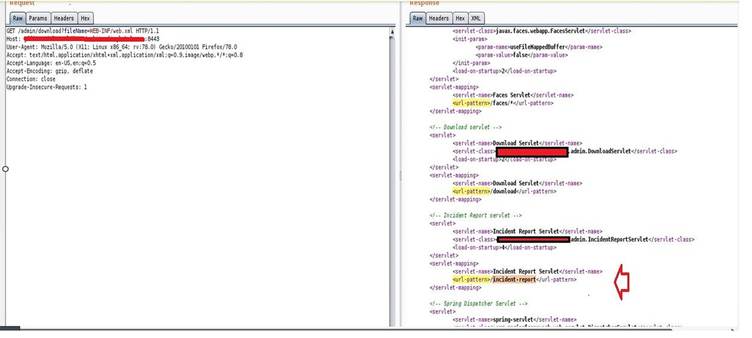
After some makes an attempt, he efficiently logged into the admin panel utilizing the credentials he discovered. This victory led him to an intriguing perform known as export_step2.xhtml, which housed a Groovy console—an interface for executing Groovy scripts.
Accessing the Groovy console opened the door to potential RCE, however executing instructions yielded no seen output. This raised an necessary query: the place was the command output hiding?
Upon reflection, he recalled that our log file may function a portal for uncovering the RCE output. By operating instructions via the Groovy console, he may leverage the log file to retrieve output.
Every time he visited http://admin.goal.com:8443/admin/incident-report, a brand new log file was generated capturing the command execution outcomes.
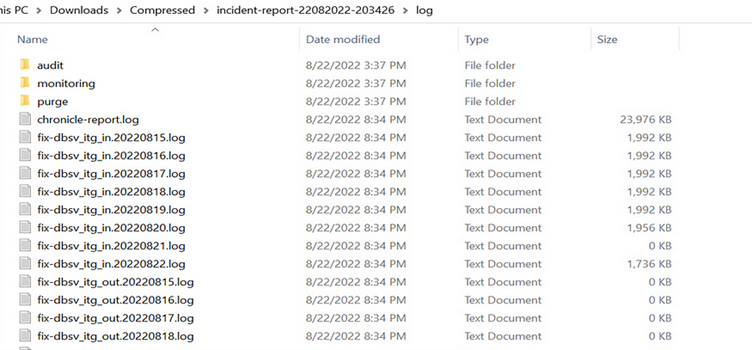

The cycle was easy:
- Log in with the found credentials.
- Navigate to the Groovy console.
- Execute a command like print “sudo cat /and so forth/passwd”.execute().textual content.
- Go to the logs at http://admin.goal.com:8443/admin/incident-report to obtain the newest log and acquire the command output.
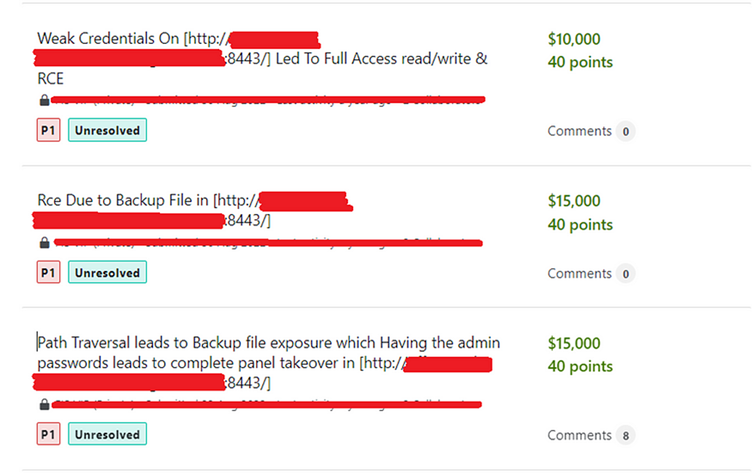

This intricate chaining of vulnerabilities not solely met the standards for RCE but in addition showcased the significance of thorough exploration. He submitted stories on each the RCE and the credentials discovery, culminating in a complete payout of $40,000 from this system.
This expertise highlights the importance of persistence and inventive problem-solving within the subject of cybersecurity. Every bug bounty hunt holds the potential for monumental discoveries—if one is keen to dig deeper.
Integrating Software Safety into Your CI/CD Workflows Utilizing Jenkins & Jira -> Free Webinar
