CrowdStrike, a pacesetter in cybersecurity, uncovered a classy phishing marketing campaign that leverages its recruitment branding to propagate malware disguised as an “worker CRM software.”
This alarming assault vector begins with a fraudulent e-mail impersonating CrowdStrike’s hiring crew, coaxing recipients into visiting a malicious web site.
As soon as there, victims are unwittingly prompted to obtain and execute a dangerous software that operates as a downloader for the cryptominer XMRig.
How the Rip-off Works
The phishing rip-off kicks off with an attractive e-mail that claims to be a part of a recruitment course of. The preliminary communication typically options skilled branding and a direct hyperlink to a fabricated web site designed to imitate CrowdStrike’s reliable recruitment portal.
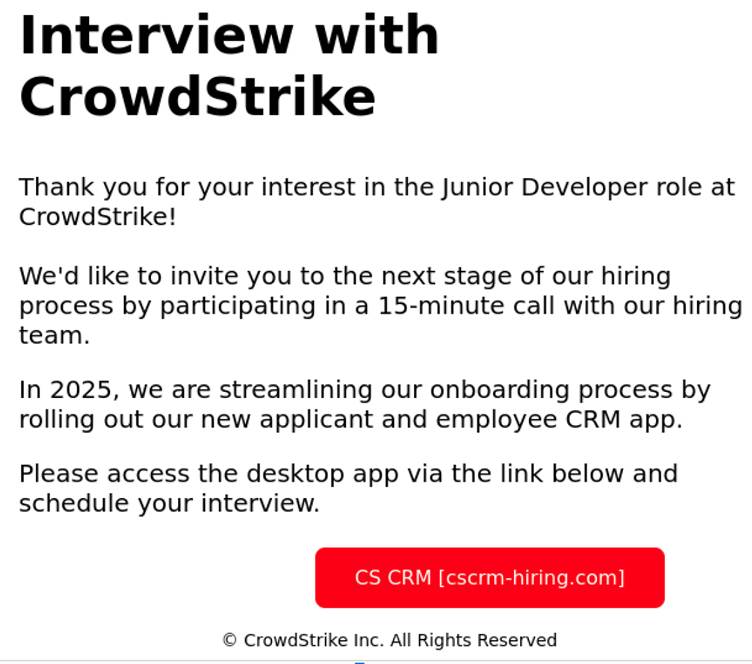

Upon clicking the hyperlink, victims land on a malicious website that presents obtain choices for each Home windows and macOS.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free
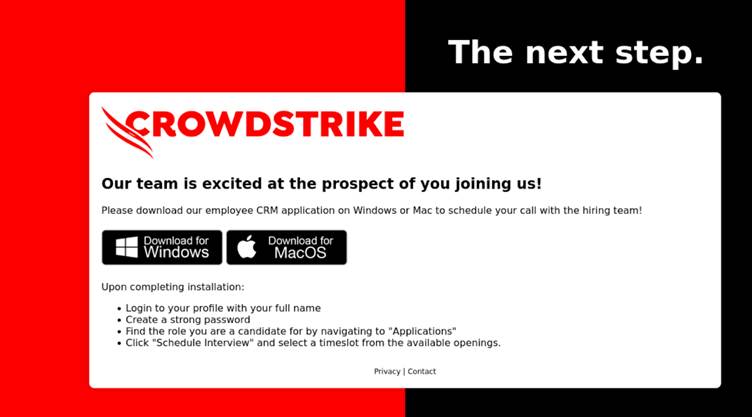

Nevertheless, whatever the choice made, the downloaded file is a Home windows executable, ingeniously crafted in Rust, designed to evade detection whereas functioning as a downloader for the XMRig cryptominer.
Based on the Crowdstrike report, the executable employs a number of superior methods to evade safety mechanisms and evaluation. Notably, it performs the next atmosphere checks:
- Debugger Detection: It makes use of the IsDebuggerPresent Home windows API to find out whether it is being monitored by a debugger.
- Course of Depend Verification: The software program checks {that a} minimal variety of energetic processes are working, which may point out a safe or monitored atmosphere.
- CPU Core Test: The malware ensures that the CPU has at the least two cores, focusing on extra succesful programs for its operations.
- Course of Scanning: It scans the energetic processes for recognized malware evaluation instruments and virtualization software program, avoiding execution in sandboxed environments.
If these checks are efficiently handed, this system shows a faux error message to keep away from suspicion earlier than continuing with its malicious actions.
Payload Supply
Following the faux pop-up, the malicious executable downloads a configuration textual content file from a specified URL. This textual content file accommodates important command-line arguments for XMRig, that are then used to execute the mining operation effectively.


The executable then retrieves XMRig from its GitHub repository and extracts the ZIP file to the %TEMPpercentSystem listing. As soon as unpacked, the first XMRig miner is launched utilizing the configuration parameters retrieved earlier.
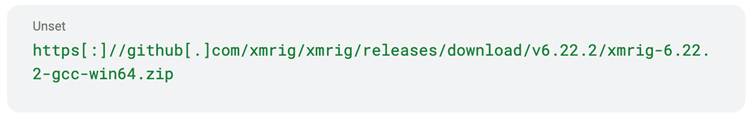



To ascertain persistence, the downloader creates a Home windows batch script within the Begin Menu Startup listing.
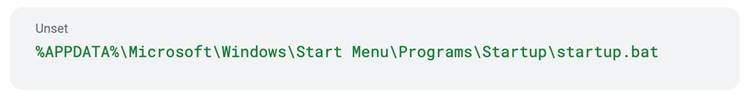

This script executes the downloaded miner every time the system boots up. Moreover, it modifies the Home windows Registry to make sure that the malicious downloader operates upon each logon, thus sustaining a steady mining operation with out the consumer’s information.
This incident underscores the essential want for vigilance in opposition to phishing scams, significantly for job seekers.
Candidates concerned within the recruitment course of are urged to confirm the legitimacy of any communication claiming to be from CrowdStrike. Downloading unsolicited recordsdata from unknown sources poses vital dangers.
Organizations can mitigate these threats by educating workers on figuring out phishing makes an attempt, monitoring community visitors for uncommon exercise, and implementing sturdy endpoint safety options.
CrowdStrike additionally needs to remind the group about different prevalent scams that misrepresent employment gives.
Fraudulent interviews and gives typically use faux web sites, e-mail addresses, and even group chat platforms. CrowdStrike confirms that it doesn’t conduct interviews through on the spot messaging or require any monetary transactions as a part of the hiring course of.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Prompt Updates!
