
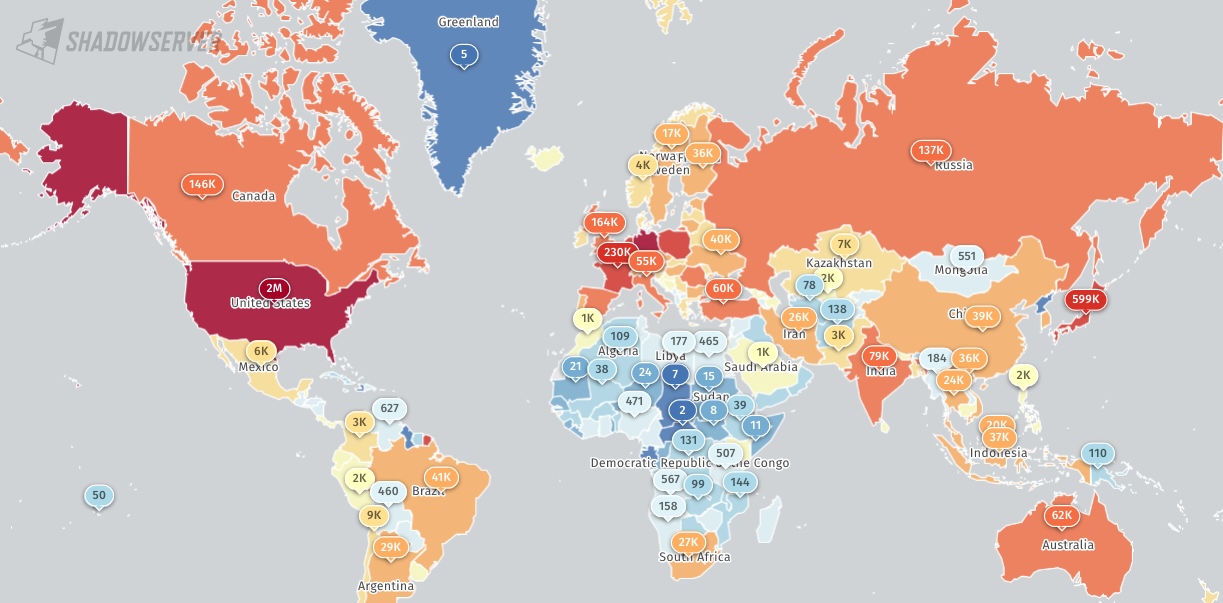
Over three million POP3 and IMAP mail servers with out TLS encryption are presently uncovered on the Web and weak to community sniffing assaults.
IMAP and POP3 are two strategies for accessing e mail on mail servers. IMAP is really useful for checking emails from a number of gadgets, resembling telephones and laptops as a result of it retains your messages on the server and synchronizes them between gadgets. POP3, however, downloads emails from the server, making them accessible solely from the machine the place they had been downloaded.
The TLS safe communication protocol helps safe customers’ data whereas exchanging and accessing their emails over the Web by way of consumer/server purposes. Nevertheless, when TLS encryption will not be enabled, their messages’ contents and credentials are despatched in clear textual content, exposing them to eavesdropping community sniffing assaults.
As scans from the ShadowServer safety menace monitoring platform Shadowserver present, round 3.3 million hosts are operating POP3/IMAP companies with out TLS encryption enabled and expose usernames and passwords in plain textual content when transmitted over the Web.
ShadowServer is now notifying mail server operators that their POP3/IMAP servers should not have TLS enabled, exposing customers’ unencrypted usernames and passwords to sniffing assaults.
“Which means that passwords used for mail entry could also be intercepted by a community sniffer. Moreover, service publicity might allow password guessing assaults in opposition to the server,” Shadowserver mentioned.
“For those who obtain this report from us, please allow TLS assist for IMAP in addition to think about whether or not the service must be enabled in any respect or moved behind a VPN.”
The unique TLS 1.0 specification and its successor, TLS 1.1, have been used for practically 20 years, with TLS 1.0 being launched in 1999 and TLS 1.1 in 2006. After intensive discussions and the event of 28 protocol drafts, the Web Engineering Process Power (IETF) permitted TLS 1.3, the following main model of the TLS protocol, in March 2018.
In a coordinated announcement in October 2018, Microsoft, Google, Apple, and Mozilla mentioned they’d retire the insecure TLS 1.0 and TLS 1.1 protocols within the first half of 2020. Microsoft started enabling TLS 1.3 by default within the newest Home windows 10 Insider builds beginning in August 2020.
In January 2021, the NSA additionally supplied steering on figuring out and changing outdated TLS protocol variations and configurations with fashionable, safe options.
“Out of date configurations present adversaries entry to delicate operational visitors utilizing a wide range of strategies, resembling passive decryption and modification of visitors by way of man-in-the-middle assaults,” the NSA mentioned.
“Attackers can exploit outdated transport layer safety (TLS) protocol configurations to achieve entry to delicate information with only a few expertise required.”
