A cybersecurity researcher has demonstrated a technique to bypass BitLocker encryption on Home windows 11 (model 24H2) by extracting full quantity encryption keys (FVEK) from reminiscence.
Utilizing a custom-built instrument named Reminiscence-Dump-UEFI, the researcher was capable of retrieve delicate cryptographic keys to decrypt a BitLocker-protected partition.
BitLocker, Microsoft’s full-disk encryption system, is designed to guard information by encrypting the whole quantity of a tool.
It’s particularly essential for safeguarding delicate data in enterprise environments. Nonetheless, its safety depends closely on stopping unauthorized entry to the encryption keys.
The strategy used within the demonstration exploits a standard weak spot: the residual information saved in RAM.
When a tool is abruptly restarted, its RAM contents might stay intact for a brief interval. By leveraging this time window, an attacker can extract delicate information saved in reminiscence, together with encryption keys.
The demonstration highlights a number of superior strategies to mitigate reminiscence degradation, together with strategies like bodily cooling RAM modules or sustaining energy to stop information decay.
Bypassing BitLocker: Demonstration of the Assault
The researcher fastidiously outlined the steps to bypass BitLocker encryption. Right here’s the summarized course of:
- Getting ready a Bootable USB Software
A USB storage gadget bigger than the system’s RAM was ready utilizing a script supplied by the analysis instrument. - Restarting the Goal System
By shorting the reset pins on the motherboard, the researcher pressured an abrupt restart of the system whereas preserving energy to the RAM. This ensured minimal information degradation. - Dumping Reminiscence Knowledge
The system was booted utilizing the USB gadget, launching the Reminiscence-Dump-UEFI instrument. This program dumped the contents of the RAM into information for additional evaluation. - Analyzing Reminiscence Dumps
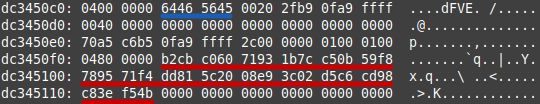
Utilizing instruments comparable to concatDumps and xxd, the researcher analyzed the reminiscence dumps. Key cryptographic information, together with FVEK, was positioned by figuring out particular reminiscence pool tags comparable to dFVE (allotted by dumpfve.sys).

The FVEK keys have been traced to particular reminiscence swimming pools, with one constant restoration location marked by the dFVE pool tag.

The keys have been extracted in hexadecimal format and prepped for decryption by appending metadata concerning the encryption algorithm, comparable to XTS-AES-128. Utilizing instruments like Dislocker, the researcher efficiently unlocked the encrypted quantity.
In accordance with the NoInitRD, this analysis underscores a essential vulnerability in methods the place attackers can achieve bodily entry.
Whereas Microsoft has integrated measures to overwrite delicate information, some keys persist in reminiscence and will be extracted beneath the precise circumstances.
- Allow Gadget Lockdown: Guarantee units are secured in tamper-proof environments to stop unauthorized bodily entry.
- Configure BitLocker with TPM: A Trusted Platform Module (TPM) provides a layer of hardware-based safety, lowering the chance of key theft.
- Fast Shutdown Protocols: Emphasize full power-off mechanisms to clear RAM.
- Educate Customers: Organizations ought to prepare workers on greatest safety practices, particularly concerning bodily gadget safety.
This revelation serves as a reminder that even subtle encryption methods like BitLocker will be susceptible beneath particular assault situations. Microsoft is predicted to analyze these findings and enhance BitLocker’s resilience.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free


