
2024 was an enormous 12 months for cybersecurity, with important cyberattacks, information breaches, new risk teams rising, and, in fact, zero-day vulnerabilities.
Some tales, although, have been extra impactful or common with our 31 million readers than others.
Beneath are fourteen of what BleepingComputer believes are probably the most impactful cybersecurity tales of 2024, with a abstract of every. These tales are in no explicit order.
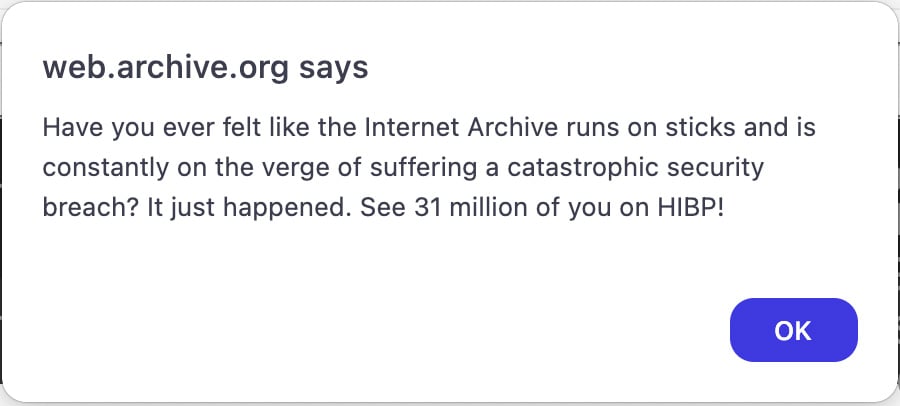
14. Web Archive hacked
On October 9, the Web Archive was hit by two completely different assaults directly—a knowledge breach the place the location’s consumer information for 33 million customers was stolen and a DDoS assault by an alleged pro-Palestinian group named SN_BlackMeta.
Whereas each assaults occurred over the identical interval, they have been carried out by completely different risk actors.
Supply: BleepingComputer
The risk actors who breached Web Archive instructed BleepingComputer that they may accomplish that by means of an uncovered GitLab configuration file containing an authentication token, permitting them to obtain the Web Archive supply code.
This supply code contained further credentials and authentication tokens, together with the credentials to Web Archive’s database administration system. This allowed the risk actor to obtain the group’s consumer database, additional supply code, and modify the location.
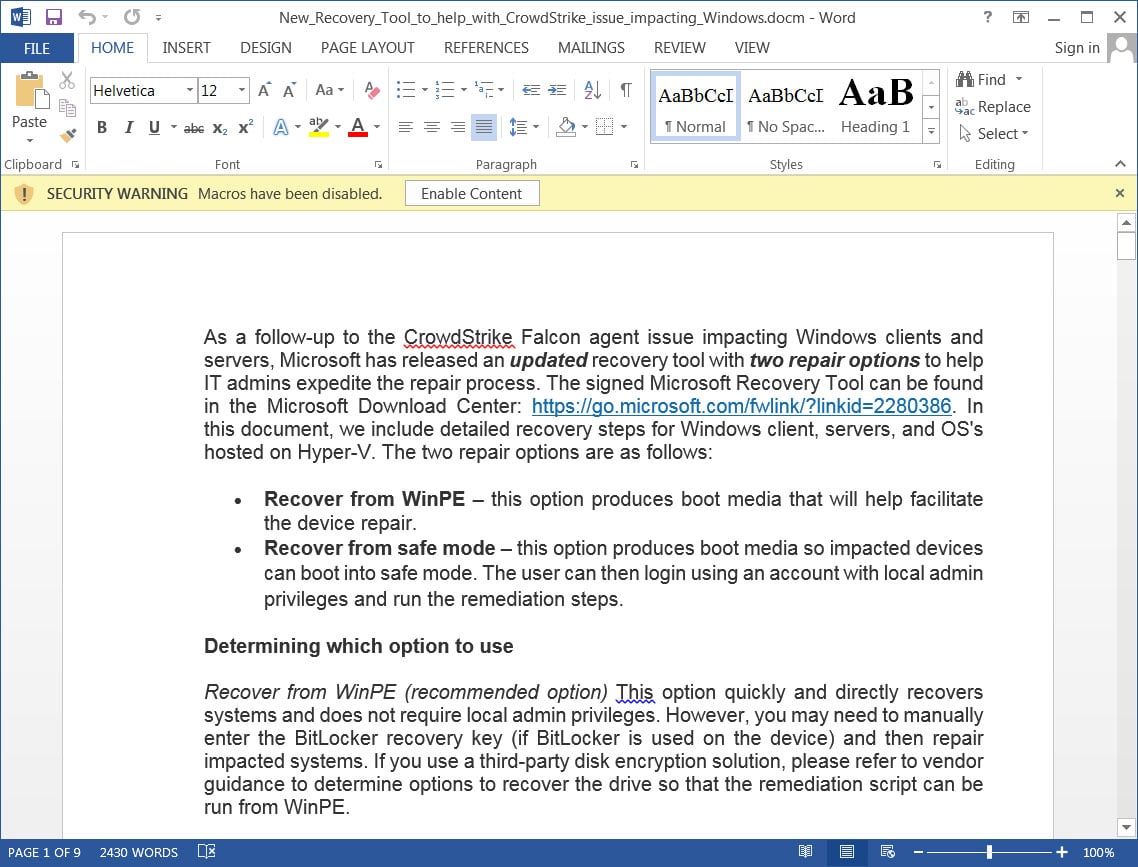
13. Dangerous CrowdStrike updates crashed 8.5 million Wndows gadgets
On July nineteenth, 2024, a defective CrowdStrike Falcon replace was pushed out to Home windows PCs within the early morning, inflicting the cybersecurity software program’s kernel driver to crash the working system.
This bug prompted important world disruptions, impacting roughly 8.5 million Home windows methods, who now discovered that their gadgets had crashed with no simple method again into the working system to take away the defective replace aside from booting into secure mode.
The bug stemmed from a flaw in CrowdStrike’s content material validation course of, which didn’t detect a faulty replace. This defective replace triggered a collection of system crashes, together with limitless reboot loops that affected each Home windows gadgets and Home windows 365 Cloud PCs.
As CrowdStrike is utilized by many organizations, it shortly prompted widespread disruption, impacting monetary corporations, airways, and hospitals worldwide who abruptly discovered their Home windows gadgets and functions have been unavailable.
Microsoft launched a Home windows restore instrument to assist take away the problematic CrowdStrike driver and restore affected methods. Regardless of this instrument, many organizations confronted a prolonged restoration course of as every machine would should be manually mounted.
Issues acquired worse when the risk actors began entering into the sport.
Cybercriminals distributed pretend CrowdStrike restore instruments and manuals that pushed malware, together with the new Daolpu infostealer. These phishing campaigns focused orgs making an attempt to recuperate from the outage, additional delaying outages.
Supply: BleepingComputer
Traders quickly filed a lawsuit in opposition to CrowdStrike, accusing it of negligence in its high quality assurance processes and failing to stop the discharge of the faulty replace.
Microsoft additionally introduced that they might be trying into altering their kernel driver dealing with insurance policies in response to the incident and inspired antivirus distributors to restrict their use of Kernel drivers to stop all these crashes.
12. Kaspersky banned within the US—software program robotically changed with UltraAV
In June, the Biden administration introduced an upcoming ban of Kaspersky antivirus software program, giving prospects till September 29, 2024, to search out different safety software program.
The ban not solely concerned the sale of Kaspersky software program within the US, but additionally prevented the corporate from delivering antivirus and safety updates to prospects.
A month later, Kaspersky started shutting down its operations within the US, telling BleepingComputer that the Biden administration’s selections have made operations “now not viable.”
Kaspersky determined to promote its US buyer base to Pango and emailed prospects in early September that they might obtain a free improve to the UltraAV software program.
Nonetheless, the corporate did not make it clear to prospects that it might uninstall its software program, and on September 19, Kaspersky customers abruptly discovered their Kaspersky merchandise eliminated and UltraAV force-installed on their computer systems whether or not they needed it or not.
This made many Kaspersky prospects livid that software program was put in on their gadgets with out permission or clear notification that it might occur.
11. Russian state-sponsored hackers breached Microsoft’s company e mail
In January, Microsoft disclosed that Russian state-sponsored risk actors breached their company e mail servers in November 2023 to steal e mail from their management, cybersecurity, and authorized groups.
A few of these emails contained details about the hacking group itself, permitting the risk actors to be taught what Microsoft knew about them.
The hacking group, generally known as Midnight Blizzard (aka Nobelium, or APT29) is believed to be a state-backed cyberespionage group tied to the Russian Overseas Intelligence Service (SVR).
Microsoft later disclosed that the risk actors carried out a password-spray assault that allowed entry to a legacy non-production take a look at tenant account.
This take a look at tenant account additionally had entry to an OAuth software with elevated privileges in Microsoft’s company setting, permitting the hackers to steal information from company mailboxes.
The hackers breached Microsoft once more in March 2024 utilizing data discovered within the stolen emails, permitting them to steal supply code repositories.
It saved getting worse, with CISA confirming in April that emails between US federal businesses and Microsoft have been additionally stolen within the assault. These emails contained data that allow the hackers acquire entry to some buyer’s methods.
10. Nationwide Public information breach uncovered your Social Safety Quantity
In August, virtually 2.7 billion data of private data for folks in america have been leaked on a hacking discussion board, exposing names, social safety numbers, all recognized bodily addresses, and potential aliases.
The information was stolen from Nationwide Public Information, an organization that collects and sells entry to non-public information to be used in background checks, to acquire felony data, and for personal investigators.
Have I Been Pwned’s Troy Hunt analyzed the breach and decided it contained 134 million distinctive e mail addresses, making this a monstrous information breach.
The risk actors behind the breach tried to promote it for $3.5 million, but it surely was finally leaked totally free on a hacking discussion board.
9. Assaults on edge networking gadgets run rampant
This 12 months, we continued to see assaults concentrating on edge networking gadgets from numerous producers, together with Fortinet, TP-Hyperlink, Ivanti, and Cisco.
A lot of these gadgets are precious targets as they’re meant to be uncovered to the Web, and as soon as breached, permit risk actors to pivot into the inner community.
There are too many tales to summarize, so listed here are an inventory of the fascinating ones:
It has gotten so unhealthy that the US is contemplating banning China-made TP-Hyperlink routers over cybersecurity considerations.
8. CDK World ransomware assaults takes down the automobile dealership business
Automobile dealership software-as-a-service supplier CDK World suffered a Black Go well with ransomware assault, inflicting the corporate to close down its methods and leaving purchasers unable to function their enterprise usually.
CDK World supplies purchasers within the auto business with a SaaS platform that handles all points of a automobile dealership’s operation, together with CRM, financing, payroll, assist and repair, stock, and back-office operations.
As lots of the automobile dealerships within the US make the most of the platform, the outage led to widespread disruption, stopping sellers from monitoring and ordering automobile elements, conducting new gross sales, and providing financing.
7. The SnowFlake information theft assaults
In Might, risk actors started promoting information that they claimed was stolen from prospects of the Snowflake cloud information platform.
After the assaults have been investigated, it was decided that the risk actors did not breach Snowflake however relatively used compromised credentials to log in to buyer’s SnowFlake accounts.
These credentials are believed to have been stolen by means of information-stealing malware.
As soon as they logged into the account, they have been capable of export the databases and use them to extort corporations into paying a ransom for the info to not be publicly launched.
AT&T disclosed in July that decision logs of 109 million prospects have been uncovered in the course of the incident and that the info was accessed from a web based database on the corporate’s Snowflake account.
TicketMaster was additionally impacted, with the risk actors claiming to steal the info of 560 million prospects.
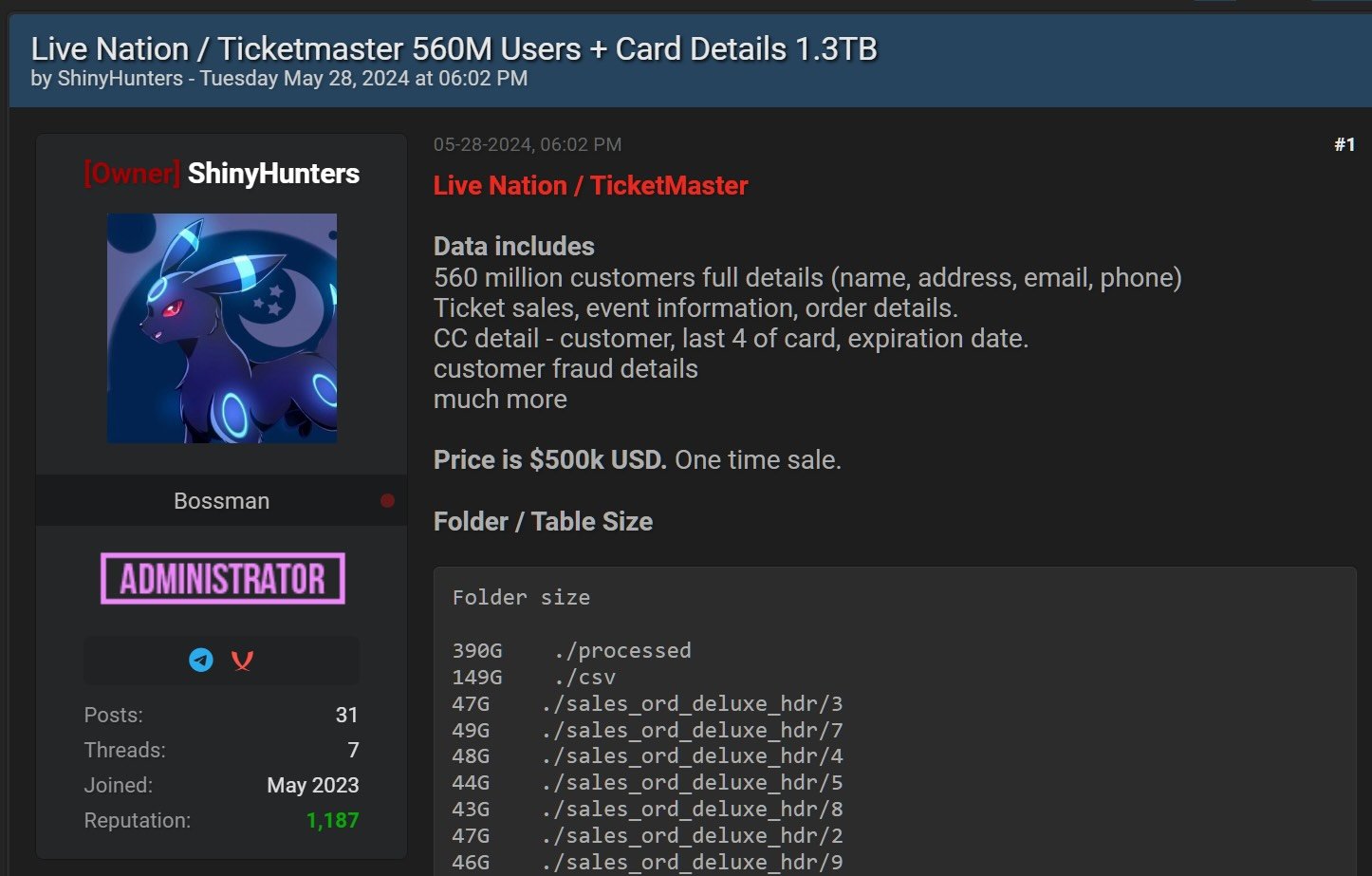
Information breaches linked to those assaults, which began in April 2024, have affected a whole bunch of hundreds of thousands of people utilizing the providers of AT&T, Ticketmaster, Santander, Pure Storage, Advance Auto Components, Los Angeles Unified, QuoteWizard/LendingTree, and Neiman Marcus.
In November, the US Division of Justice unsealed an indictment in opposition to two folks, Connor Riley Moucka and John Erin Binns, who’re accused of being behind the assaults.
The risk actors allegedly extorted $2.5 million as a part of these assaults, with Wired reporting that AT&T paid $370,000 for the hackers to delete stolen name data.
6. The North Korean IT Employee scheme
This 12 months, we noticed an uptick in North Korean IT employees making an attempt to get jobs within the US and different international locations to carry out cyberespionage and generate income for his or her nation’s operations.
In Might, the Division of Justice charged 5 people, a US Citizen girl, a Ukrainian man, and three international nationals, for his or her involvement in serving to North Korean IT works infiltrate US job markets to generate income for North Korea’s nuclear weapons program.
In July, e mail safety agency KnowBe4 mistakenly employed a North Korean hacker as their Principal Software program Engineer, who tried to put in information-stealing malware on the community.
In August, the Justice Division arrested a Nashville man charged with serving to North Korean IT employees acquire distant work at corporations throughout america and working a laptop computer farm they used to pose as U.S.-based people.
Each Mandiant and SecureWorks later launched reviews on the North Korean IT Employee risk, sharing their techniques and the way corporations can defend themselves.
5. The UnitedHealth Change HealthCare ransomware assault
In February, UnitedHealth subsidiary Change Healthcare suffered an enormous ransomware assault that prompted huge disruption to the US healthcare business.
The outages prevented docs and pharmacies from submitting claims and prevented pharmacies from accepting low cost prescription playing cards, inflicting sufferers to pay full value for medicines.
The assault was in the end linked to the BlackCat ransomware gang, aka ALPHV, who used stolen credentials to breach the corporate’s Citrix distant entry service, which didn’t have multi-factor authentication enabled.
In the course of the assault, the risk actors stole 6 TB of information and in the end encrypted computer systems on the community, inflicting the corporate to close down IT methods to stop the unfold of the assault.
The UnitedHealth Group admitted to paying a ransom demand to obtain a decryptor and for the risk actors to delete the stolen information. The ransom fee was allegedly $22 million, in line with the BlackCat ransomware affiliate who carried out the assault.
The BlackCat ransomware operation was underneath immense strain from legislation enforcement after the Change Healthcare assaults, inflicting them to close down.
After UnitedHealth paid an alleged $20 million ransom, the ransomware operation carried out an exit rip-off, stealing all the cash and never sharing any with the affiliate who carried out the assault.
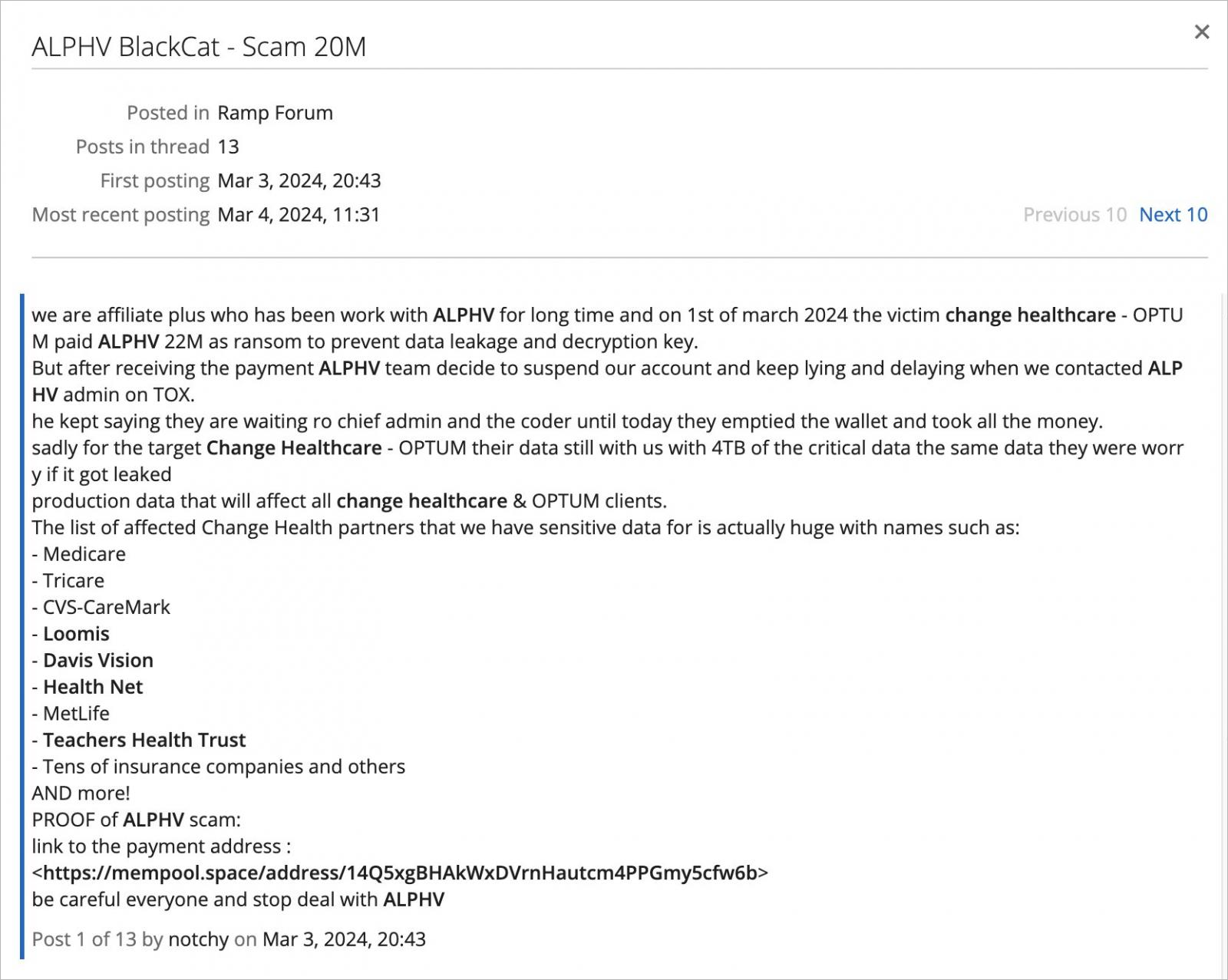
Sadly, the affiliate claimed to nonetheless have Change Healthcare’s information, which they used to extort the healthcare firm once more, this time utilizing RansomHub’s extortion website.
Finally, the info disappeared from the extortion, doubtless indicating that one other ransom was paid.
In October, UnitedHealth confirmed that over 100 million folks had their private and healthcare information stolen, marking this as the biggest healthcare information breach in recent times.
4. LockBit disrupted
On February 19, authorities took down LockBit’s infrastructure, which included 34 servers internet hosting the info leak web site and its mirrors, information stolen from the victims, cryptocurrency addresses, decryption keys, and the affiliate panel.
This disruption was a part of a global legislation enforcement operation known as Operation Cronos.
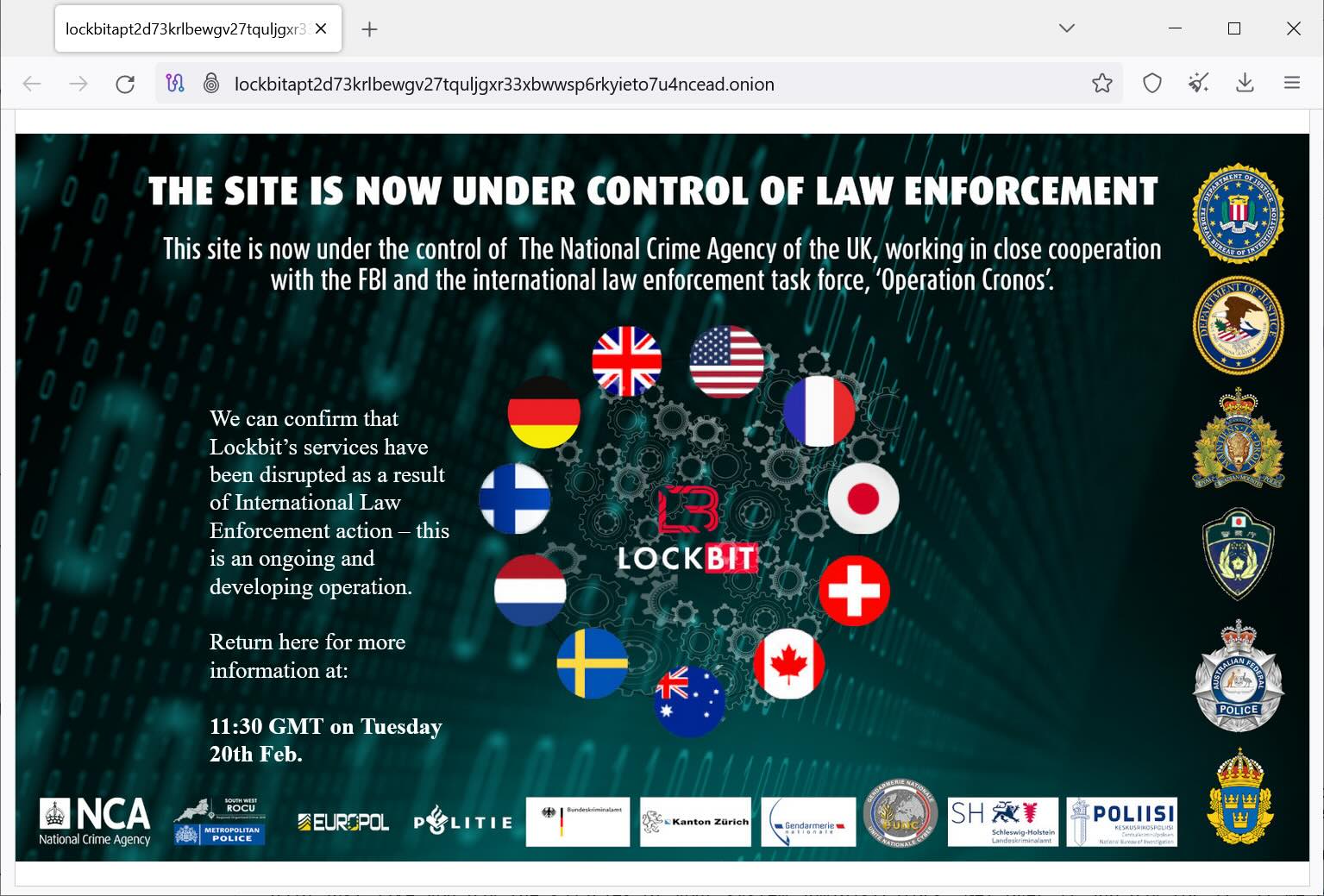
Supply: BleepingComputer
5 days later, LockBit relaunched with new infrastructure and threatened to focus extra of its assaults on the federal government sector.
Nonetheless, the ransomware gang was by no means capable of return to its earlier prominence, with its associates shifting to different ransomware operations.
Over the previous 12 months, legislation enforcement has continued to focus on LockBit, figuring out and charging seven LockBit ransomware members.
Amongst these charged, is the first operator of the ransomware operation, who the Division of Justice claims is a Russian nationwide named Dmitry Yuryevich Khoroshev, aka ‘LockBitSupp’ and ‘putinkrab’.
LockBit just lately started testing a brand new encryptor known as LockBit 4, which doesn’t seem like a lot completely different than its earlier model.
3. Home windows 11 Recall: A privateness nightmare?
Microsoft’s new AI-powered Home windows 11 Recall function has sparked numerous concern among the many cybersecurity neighborhood, with many considering that it’s a huge privateness threat and a brand new assault vector that risk actors can exploit to steal information.
After receiving large backlash, Microsoft delayed the discharge of the software program to extend its safety by requiring customers to opt-in to allow Recall on their computer systems and that they will have to verify they’re in entrance of their PC by way of Home windows Hiya to have the ability to use it.
Microsoft continued to delay its launch whereas including further options, akin to robotically filtering delicate content material, permitting customers to exclude particular apps, web sites, or in-private searching classes, and it may be eliminated if wanted.
Nonetheless, after releasing the software program to Home windows Insiders for testing, it was found that Home windows 11 Recall didn’t correctly filter delicate data, like bank cards.
Microsoft mentioned they proceed refining the product as new points are found.
2. The 2024 Telecom assaults
A Chinese language state-sponsored hacking group generally known as “Salt Hurricane” is linked to a collection of cyberattacks concentrating on telecommunications corporations globally.
These breaches compromised at the very least 9 main telecom suppliers, together with AT&T, Verizon, and T-Cellular.
The group reportedly centered on infiltrating telecom infrastructure to steal textual content messages, telephone name data, and voicemails from focused folks. The risk actors additionally focused the wiretapping platforms utilized by the US authorities, elevating severe nationwide safety considerations.
A White Home briefing revealed that Salt Hurricane’s operations additionally impacted telecommunications suppliers in dozens of nations.
Within the US, these assaults prompted considerations about weaknesses in telecom infrastructure and the safety of presidency surveillance platforms.
US lawmakers, together with Senator Ron Wyden, have proposed laws to handle vulnerabilities within the nation’s telecom infrastructure. The proposed invoice goals to ascertain stricter cybersecurity requirements and oversight for telecom suppliers to stop comparable assaults sooner or later.
The US authorities reportedly plans to ban China Telecom’s final lively US operations in response to the telecom hacks.
1. The rise of Infostealers
Info-stealing malware campaigns are operating rampant this 12 months, utilized in many various campaigns to steal contaminated customers’ browser data, cookies, saved credentials, bank cards, and cryptocurrency wallets.
Whereas infostealers have been round for a few years, they’ve been notably distinguished with risk actors utilizing them in a variety of campaigns.
These stolen credentials are then used to breach company networks, financial institution accounts, cryptocurrency exchanges, and e mail accounts.
The variety of tales surrounding infostealers is just too lengthy to summarize, so as an alternative, listed here are a number of of the methods infostealers have been used this 12 months:
Sadly, for individuals who grow to be contaminated with an infostealer, it may result in devastating monetary losses as risk actors steal cryptocurrency and entry victims’ financial institution accounts.
One of the simplest ways to stop all these assaults is to allow two-factor authentication with an authenticator app on all accounts that supply the safety. With 2FA enabled, even when a risk actor has your credentials, they will not be capable to log in with out the code generated by your authenticator.
