
The Clop ransomware gang began to extort victims of its Cleo information theft assaults and introduced on its darkish net portal that 66 firms have 48 hours to reply to the calls for.
The cybercriminals introduced that they’re contacting these firms straight to supply hyperlinks to a safe chat channel for conducting ransom cost negotiations. Additionally they offered e-mail addresses the place victims can attain out themselves.
Within the notification on their leak website, Clop lists 66 partial names of firms that didn’t have interaction the hackers for negotiations. If these firms proceed to disregard, Clop threatens to reveal their full title in 48 hours.
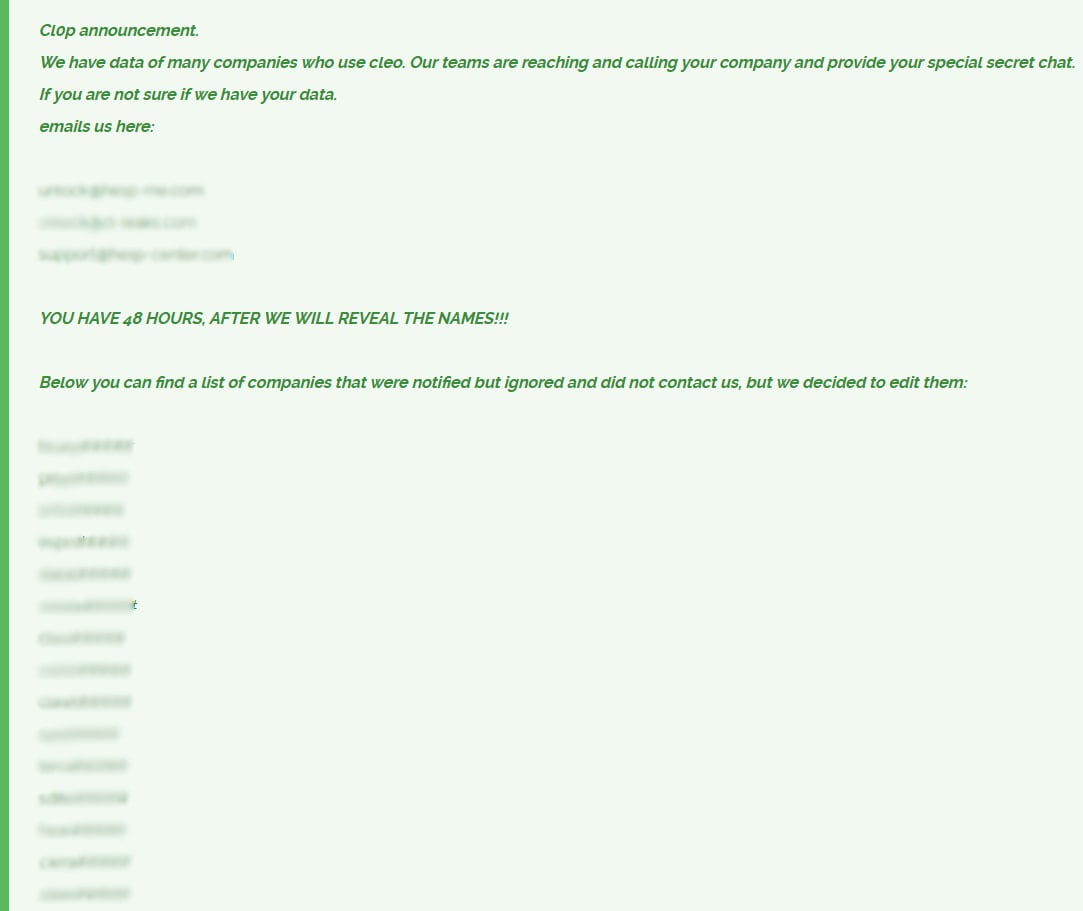
The hackers be aware that the checklist represents solely victims which have been contacted however didn’t reply to the message, suggesting that the checklist of affected firms could also be bigger.
Clop achieves one other main breach
The Cleo information theft assault represents one other main success for Clop, who leveraged leveraging a zero-day vulnerability in Cleo LexiCom, VLTransfer, and Concord merchandise to steal information from the networks of breached firms.
Previously, Clop ransomware accessed firm networks by exploiting zero-day vulnerabilities in Accellion FTA safe file switch platform, GoAnywhere MFT platform, and MOVEit Switch platform.
The gang can be chargeable for one other hacking spree concentrating on firms working the SolarWinds Serv-U FTP software program.
The zero-day flaw exploited this time is now tracked as CVE-2024-50623 and it permits a distant attacker to carry out unrestricted file uploads and downloads, resulting in distant code execution.
A repair is out there for Cleo Concord, VLTrader, and LexiCom model 5.8.0.21 and the seller warned in a non-public advisory that hackers have been exploiting it to open reverse shells on compromised networks.
Earlier this month, Huntress publicly disclosed that the vulnerability was actively exploited and sounded the alarm that the seller’s repair may very well be bypassed. The researchers additionally offered a proof-of-concept (PoC) exploit to reveal their findings.
Just a few days later, Clop ransomware confirmed to BleepingComputer that it was chargeable for exploiting CVE-2024-50623.
The notorious ransomware group declared that information from earlier assaults will now be deleted from its platform because it focuses on the brand new extortion spherical.
In an e-mail to BleepingComputer, Macnica researcher Yutaka Sejiyama mentioned that even with the unfinished firm names that Clop revealed on its information leak website, it’s attainable to determine a few of the victims by merely cross checking the hacker’s hints with homeowners of Cleo servers uncovered on the general public net.
At the moment, it’s unknown what number of firms have been compromised by Clop’s newest assault wave, however Cleo claims that its software program is utilized by greater than 4,000 organizations worldwide.

