
The BadBox Android malware botnet has grown to over 192,000 contaminated units worldwide regardless of a current sinkhole operation that tried to disrupt the operation in Germany.
Researchers from BitSight warn that the malware seems to have expanded its concentrating on scope past no-name Chinese language Android units, now infecting extra well-known and trusted manufacturers like Yandex TVs and Hisense smartphones.
The BadBox malware botnet
BadBox is an Android malware regarded as primarily based on the ‘Triada’ malware household, infecting units made by obscure producers both by way of provide chain assaults on their firmware, shady staff, or by way of injections going down as they enter the product distribution section.
It was first found on a T95 Android TV field bought from Amazon by Canadian safety marketing consultant Daniel Milisic in early 2023. Since then, the malware operation has expanded to different no-name merchandise bought on-line.
The aim of the BadBox marketing campaign is monetary achieve, which is achieved by turning the gadget right into a residential proxy or utilizing it to carry out advert fraud. These residential proxies can then be rented to different customers, in lots of instances cybercriminals, who use your gadget as a proxy to conduct assaults or different fraudulent exercise.
Moreover, the BadBox malware can be utilized to put in extra malicious payloads onto Android units, enabling extra harmful operations.
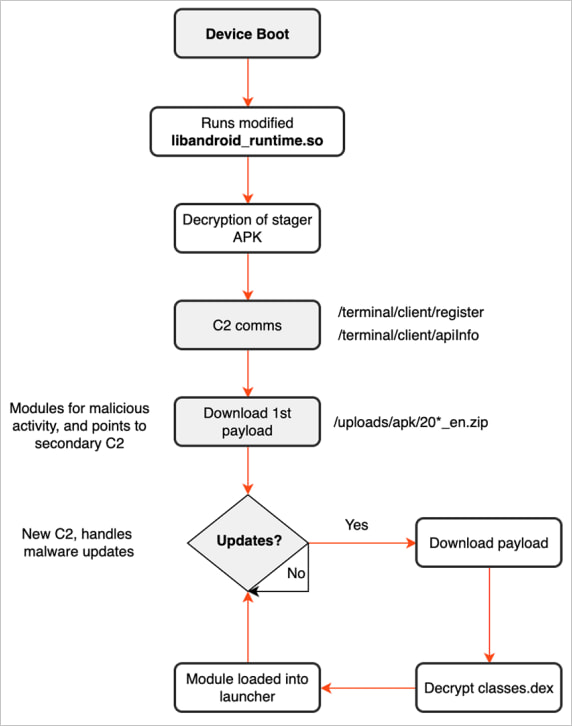
Supply: BitSight
Final week, Germany’s Federal Workplace for Info Safety (BSI) introduced they disrupted the BadBox malware operation within the nation after it sinkholed one of many malware’s command and management servers, slicing off communication for 30,000 Android units.
These units had been primarily Android-based digital image frames and media streaming bins, however BSI warned that it’s extremely possible that BadBox is current in additional product classes.
BadBox continues to develop
The brand new report from BitSight confirms that the BadBox operation has continued to develop regardless of Germany’s police motion, with researchers discovering the Android malware put in on 192,000 TVs and smartphones.
In keeping with BitSight researcher Pedro Falé, the cybersecurity firm was in a position to sinkhole one of many command and management servers utilized by the BadBox malware operation.
Because the researchers now management the area, they’ll see when units try to hook up with it, permitting them to see what number of distinctive IP addresses are impacted.
“The truth is that BADBOX nonetheless appears to be very a lot alive and spreading,” wrote Falé.
“This was evident when Bitsight managed to sinkhole a BADBOX area, registering greater than 160,000 distinctive IPs in a 24 hour interval. A quantity that has been steadily rising.”
The variety of detected units is way larger than what was beforehand thought of the height for this botnet, at round 74,000 compromised units.
Roughly 160,000 of the contaminated units are the Yandex 4K QLED Good TV, which could be very widespread in Russia, and the Hisense T963 smartphone.
“The [impacted] fashions starting from YNDX-00091 to YNDX-000102 are 4K Good TVs from a well known model, not low-cost Android TV bins,” explains BitSight.
“It is the primary time a serious model Good TV is seen immediately speaking at such quantity with a BadBox command and management (C2) area, broadening the scope of affected units past Android TV bins, tablets, and smartphones.”
The units detected by BitSight are primarily situated in Russia, China, India, Belarus, Brazil, and Ukraine.
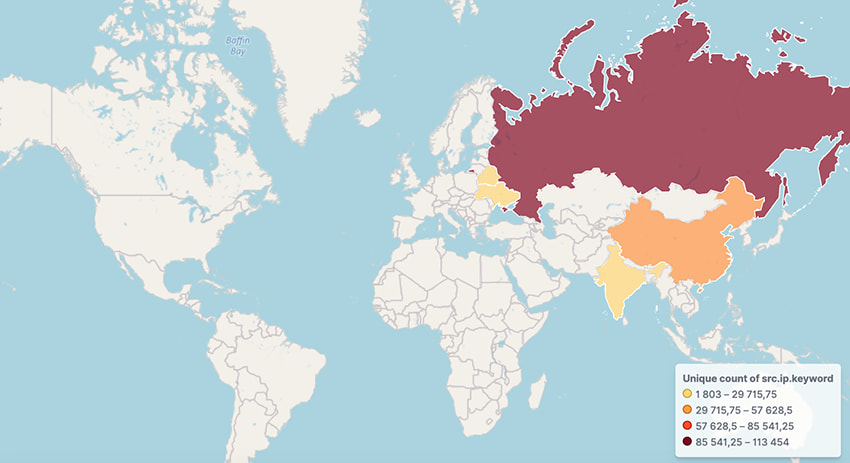
Supply: BitSight
BitSight additionally experiences that BSI’s current operation didn’t influence its telemetry information, because the motion was geographically restricted, permitting the BadBox Android malware operation to proceed unabated.
With BadBox increasing to extra main manufacturers, it is essential for shoppers to use the newest firmware safety updates, isolate their sensible units from extra vital programs, and disconnect them from the web when not in use.
Nonetheless, if no safety or firmware updates can be found in your gadget, you might be strongly suggested to disconnect them out of your community or flip them off altogether.
Indicators of a BadBox botnet an infection embody overheating and efficiency drops from excessive processor utilization, atypical community site visitors, and adjustments within the gadget settings.
