Cybersecurity specialists are sounding the alarm over a brand new pressure of malware dubbed “I2PRAT,” which leverages encrypted peer-to-peer (P2P) communication through the Invisible Web Undertaking (I2P) community to keep away from detection.
The malware, first reported on November 19 by the researcher Gi7w0rm, demonstrates a extremely subtle an infection chain and revolutionary evasion strategies, elevating considerations among the many international cybersecurity neighborhood.
I2PRAT’s standout characteristic is its use of I2P, an encrypted P2P overlay community designed for nameless communication.
Not like conventional command-and-control (C2) communication strategies, I2P obscures the supply and vacation spot of knowledge, making it almost unattainable for safety instruments to intercept or hint the visitors.
The malware makes use of I2PD, an open-source I2P shopper, to ascertain these clandestine C2 channels, permitting it to exfiltrate knowledge and obtain instructions with out detection.
Free Webinar on Greatest Practices for API vulnerability & Penetration Testing: Free Registration
An infection Chain Overview
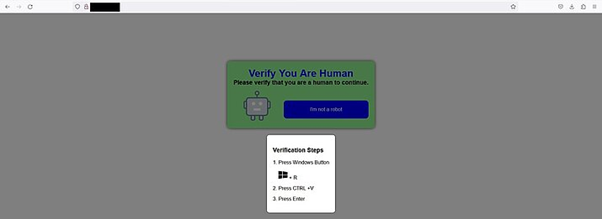
The malware’s an infection chain begins with a focused phishing e-mail. Victims are lured into clicking a malicious hyperlink directing them to a pretend CAPTCHA verification web page.
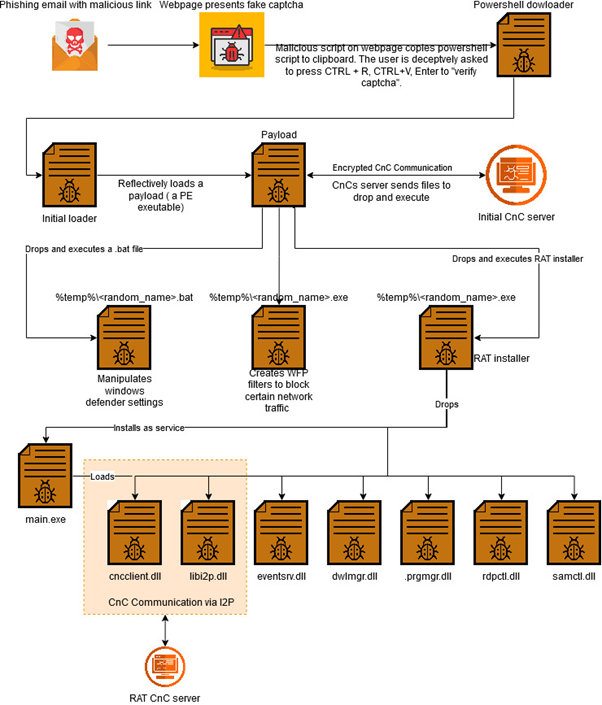

The web page makes use of misleading JavaScript to repeat a malicious PowerShell script to the clipboard, tricking customers into inadvertently executing it.
This script downloads the first-stage malware loader, which disables Home windows Defender and deploys additional malicious payloads.
Key steps within the an infection chain embody:
- Disabling Home windows Defender to bypass antivirus protections.
- Deploying Home windows Filtering Platform (WFP) filters to dam Microsoft safety updates.
- Putting in a Distant Entry Trojan (RAT) as a system service.
- Establishing encrypted C2 communication by way of I2P.
I2PRAT incorporates a number of layers of obfuscation and protection evasion ways. For instance, it deploys batch scripts to disable Microsoft Defender updates and exclude key directories from scans.
Moreover, it leverages WFP filters to dam telemetry knowledge from being despatched to Microsoft’s safety cloud, rendering the contaminated machine susceptible and blind to updates.

The malware additionally employs a intelligent trick by making a hidden listing named to resemble the “My Pc” system shortcut, making its information onerous to find. Permissions inside this listing are restricted utilizing utilities like icacls.exe, additional masking its presence.
Modular RAT and I2P Communication
On the core of I2PRAT is a modular Distant Entry Trojan (RAT) that makes use of plugins to ship numerous malicious functionalities. Communication between the malware and its C2 infrastructure is established by way of I2P, guaranteeing all knowledge exchanges are encrypted and anonymized.
This method permits risk actors to situation instructions, exfiltrate delicate info, and deploy extra payloads whereas evading conventional community monitoring.
I2PRAT showcases the rising development of malware builders adopting encrypted P2P networks like I2P to outmaneuver cybersecurity defenses, as per a report by Gdata Software program.
The usage of anonymized communication channels complicates detection and mitigation, posing a major problem for organizations and researchers alike.
To counter such threats, organizations should undertake superior risk detection programs able to monitoring anomalous community behaviors and implement sturdy e-mail safety protocols to stop phishing assaults.
Finish-user consciousness coaching additionally performs a vital function in decreasing the probability of profitable exploits.
The cybersecurity neighborhood continues to investigate I2PRAT to develop efficient countermeasures, however its use of encrypted P2P communication highlights an alarming evolution in cyber threats.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Strive for Free

