Authored by Wenfeng Yu and ZePeng Chen
As smartphones have turn out to be an integral a part of our every day lives, malicious apps have grown more and more misleading and complex. Lately, we uncovered a seemingly innocent app referred to as “BMI CalculationVsn” on the Amazon App Retailer, which is secretly stealing the bundle identify of put in apps and incoming SMS messages below the guise of a easy well being instrument. McAfee reported the found app to Amazon, which took immediate motion, and the app is not obtainable on Amazon Appstore.

Determine 1. Utility printed on Amazon Appstore
Superficial Performance: Easy BMI Calculation
On the floor, this app seems to be a primary instrument, offering a single web page the place customers can enter their weight and top to calculate their BMI. Its interface seems to be fully per a regular well being software. Nevertheless, behind this harmless look lies a variety of malicious actions.
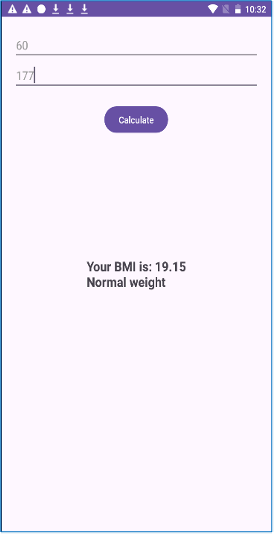
Determine 2. Utility MainActivity
Malicious Actions: Stealing Non-public Knowledge
Upon additional investigation, we found that this app engages within the following dangerous behaviors:
- Display screen Recording: The app begins a background service to document the display screen and when the consumer clicks the “Calculate” button, the Android system will pop up request display screen recording permission message and begin display screen recording. This performance is more likely to seize gesture passwords or delicate knowledge from different apps. Within the evaluation of the newest current samples, it was discovered that the developer was not prepared for this perform. The code didn’t add the recorded mp4 file to the C2 server, and in the beginning of the startRecording() methodology, the developer added a code that straight returns and doesn’t execute observe code.
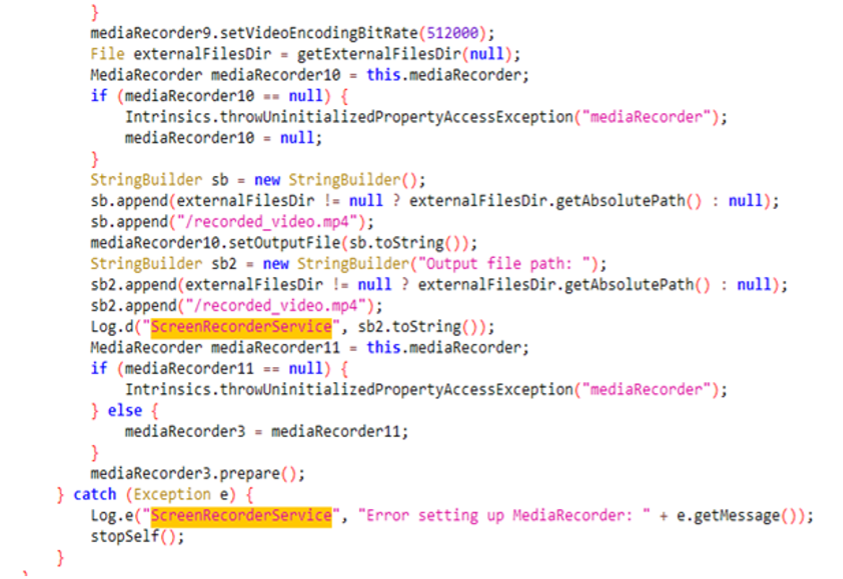
Determine 3. Display screen Recorder Service Code
When the recording begins, the permission request dialog can be displayed.
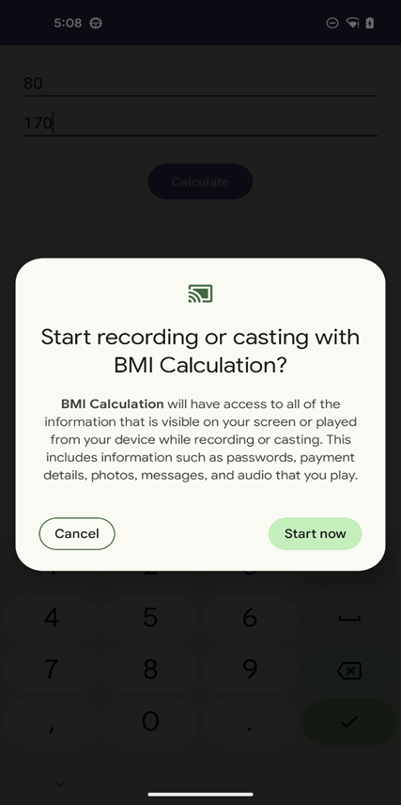
Determine 4. Begin Recording Request.
- Put in App Info: The app scans the system to retrieve a listing of all put in functions. This knowledge might be used to establish goal customers or plan extra superior assaults.
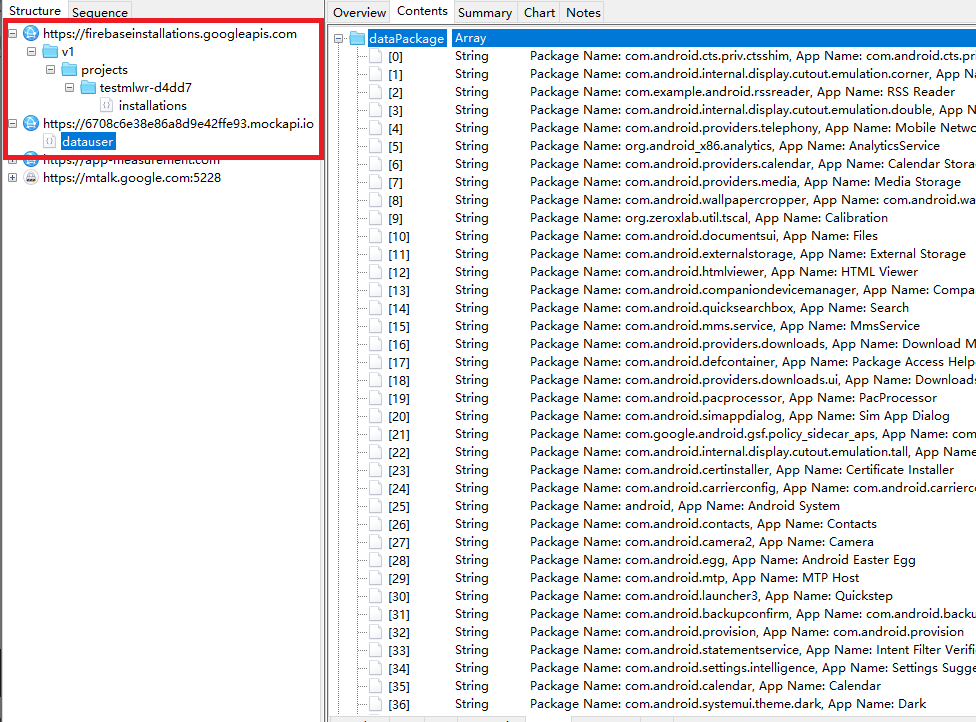
Determine 5. Add Person Knowledge
- SMS Messages: It intercepts and collects all SMS messages obtained on the system, probably to seize one-time password (OTP), verification codes and delicate info. The intercepted textual content messages can be added to Firebase (storage bucket: testmlwr-d4dd7.appspot.com).
Malware below improvement:
In keeping with our evaluation of historic samples, this malicious app remains to be below improvement and testing stage and has not reached a accomplished state. By looking for associated samples on VirusTotal primarily based on the malware’s bundle identify (com.zeeee.recordingappz) revealed its improvement historical past. We are able to see that this malware was first developed in October 2024 and initially developed as a display screen recording app, however halfway via the app’s icon was modified to the BMI calculator, and the payload to steal SMS messages was added within the newest model.
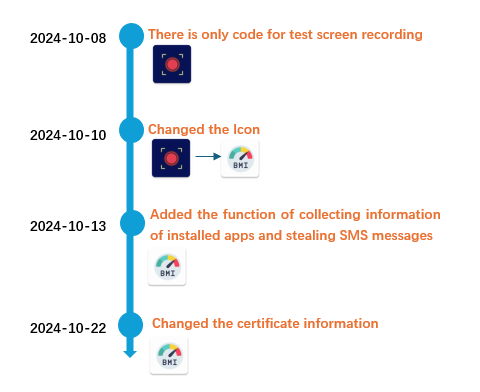
Determine 6. The Timeline of Utility Growth
The tackle of the Firebase Set up API utilized by this app makes use of the character “testmlwr” which signifies that this app remains to be within the testing part.
App Developer Info:
In keeping with the detailed details about this app product on the Amazon web page, the developer’s identify is: “PT. Visionet Knowledge Internasional”. The malware writer tricked customers by abusing the names of an enterprise IT administration service supplier in Indonesia to distribute this malware on Amazon Appstore. This reality means that the malware writer could also be somebody with data of Indonesia.
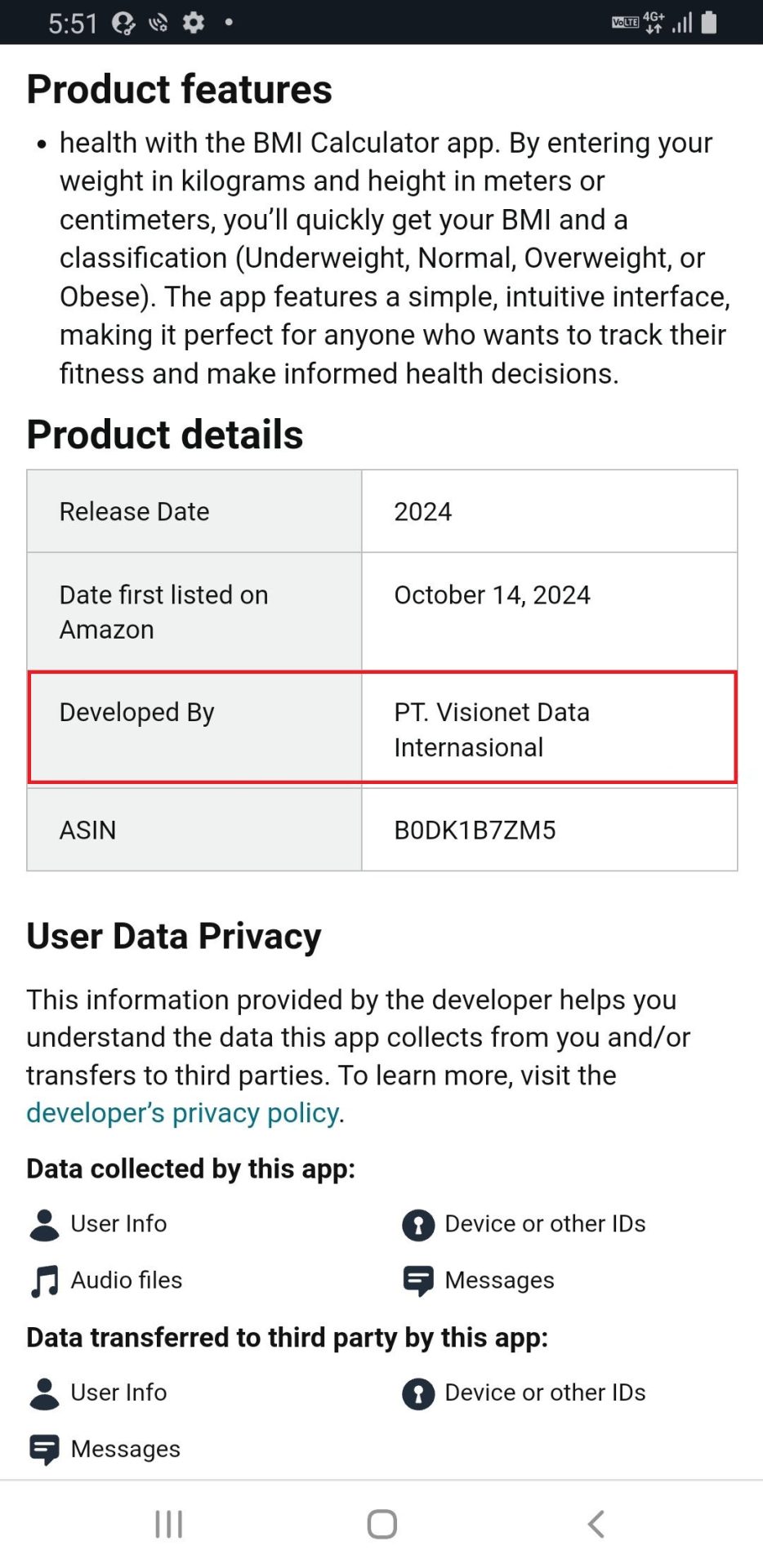
Determine 7. Developer Info
The best way to Defend Your self
To keep away from falling sufferer to such malicious apps, we advocate the next precautions:
- Set up Trusted Antivirus Apps: Use dependable antivirus software program to detect and stop malicious apps earlier than they’ll trigger hurt.
- Assessment Permission Requests: When putting in an app, rigorously study the permissions it requests. Deny any permissions that appear unrelated to its marketed performance. As an illustration, a BMI calculator has no respectable purpose to request entry to SMS or display screen recording.
- Keep Alert: Look ahead to uncommon app conduct, reminiscent of decreased system efficiency, fast battery drain, or a spike in knowledge utilization, which may point out malicious exercise working within the background.
Conclusion
As cybercrime continues to evolve, it’s essential to stay vigilant in defending our digital lives. Apps like “BMI CalculationVsn” function a stark reminder that even the only instruments can harbor hidden threats. By staying alert and adopting strong safety measures, we will safeguard our privateness and knowledge.
IoC
Distribution web site:
- hxxps://www.amazon.com/PT-Visionet-Knowledge-Internasional-CalculationVsn/dp/B0DK1B7ZM5/
C2 servers/Storage buckets:
- hxxps://firebaseinstallations.googleapis.com/v1/initiatives/testmlwr-d4dd7
- hxxps://6708c6e38e86a8d9e42ffe93.mockapi.io/
- testmlwr-d4dd7.appspot.com
Pattern Hash:
- 8477891c4631358c9f3ab57b0e795e1dcf468d94a9c6b6621f8e94a5f91a3b6a

