A current marketing campaign dubbed FLUX#CONSOLE has come to mild, leveraging Microsoft Widespread Console Doc (.MSC) recordsdata to infiltrate methods with backdoor malware.
The marketing campaign showcases the rising sophistication of phishing methods and the exploitation of lesser-known Home windows options.
The FLUX#CONSOLE Marketing campaign
The FLUX#CONSOLE marketing campaign has been recognized as a multi-stage assault with sinister targets.
By utilizing MSC recordsdata, menace actors bypass many conventional antivirus (AV) methods and ship extremely obfuscated backdoor payloads.
This technique seems to be a shift from the abuse of LNK recordsdata, which have been a trademark of phishing campaigns for years. Key features of this marketing campaign embrace:
- Tax-Themed Phishing Lures: Emails trick customers into opening benign tax-related paperwork.
- Superior Obfuscation: From JavaScript to hid DLLs, the attackers make use of a number of obfuscation layers to hinder detection.
- DLL Sideloading: The usage of reputable Home windows purposes like Dism.exe to execute malicious code.
- Persistence Mechanisms: Scheduled duties make sure the malware stays lively even after the system reboots.
These methods collectively reveal the lengths cybercriminals go to evade detection and set up persistent entry.
2024 MITRE ATT&CK Analysis Outcomes Launched for SMEs & MSPs -> Obtain Free Information
How the Assault Works
Step 1: Phishing Lure
In response to the Securonix report, the assault begins with a phishing electronic mail containing both a direct malicious attachment or a hyperlink. The attachment masquerades as a reputable file, similar to a tax doc.
On this case, filenames like “Revenue-Tax-Deduction-and-Rebates202441712.pdf” are used.The misleading .MSC file seems as a PDF, utilizing a Home windows function the place file extensions are hidden by default, additional tricking customers.
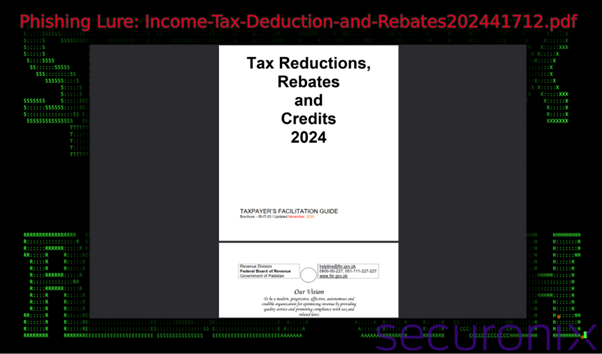

Step 2: Execution of the MSC File
Microsoft Widespread Console Doc (.MSC) recordsdata are reputable Home windows instruments used to configure administrative settings. Nevertheless, on this marketing campaign, attackers exploit their skill to execute embedded scripts or instructions.
- When customers double-click the .MSC file, malicious JavaScript or VBScript is executed below the guise of the reputable mmc.exe course of.
- The file additionally hides its exercise by minimizing home windows and using superior obfuscation.
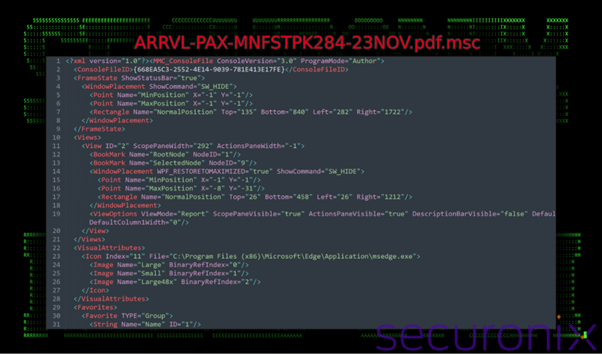

Step 3: Payload Supply
The .MSC file acts as each a loader and dropper. It initiates certainly one of two supply mechanisms:
- Embedded throughout the .MSC file itself.
- Downloaded from a distant server.
In each circumstances, it delivers a malicious payload within the type of a DLL file named DismCore.dll, which is sideloaded by way of the reputable Dism.exe course of.
Step 4: Persistence
As soon as the malware is lively, it establishes persistence by creating scheduled duties. For instance, a process named “CoreEdgeUpdateServicesTelemetryFallBack” is created to execute the malicious Dism.exe each 5 minutes, guaranteeing the malware continues operating.
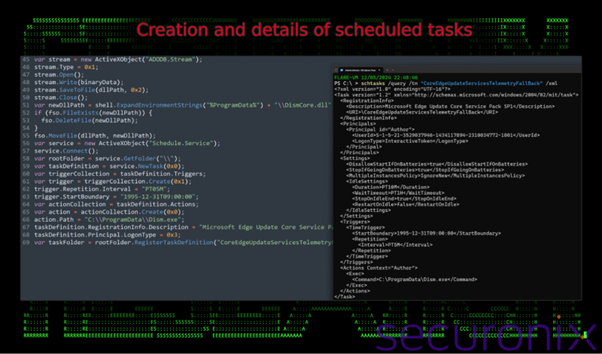

Microsoft Administration Console (MMC) snap-in recordsdata (.MSC) are sometimes utilized by IT directors and aren’t usually perceived as malicious. Attackers exploit this belief issue. When opening an .MSC file:
- The reputable mmc.exe course of is triggered.
- The embedded malicious code runs inconspicuously below the guise of an administrative device.
Moreover, as a result of .MSC recordsdata can host scripts like JavaScript or VBScript, they provide a versatile but highly effective medium for executing malicious payloads.
Obfuscation Strategies
The FLUX#CONSOLE marketing campaign employs cutting-edge obfuscation strategies:
- JavaScript Layers: The preliminary script is obfuscated, usually hiding malware execution instructions. A number of decryption steps are required to investigate its conduct.
- Base64 and Hex Encoding: Payloads are encoded to keep away from static detection.
- DLL Obfuscation: Even the ultimate DismCore.dll payload consists of numerous junk code routines to confuse analysts.
These ways make it difficult for conventional safety instruments to detect and block the malware.
As soon as contained in the system, the backdoor:
- Communicates with a distant Command-and-Management (C2) server, sending encrypted requests and responses.
- Can exfiltrate delicate knowledge.
- Supplies attackers with potential for lateral motion, enabling additional compromise of company networks.
Though researchers disrupted the assault inside 24 hours, the severity of the breach highlights the vulnerabilities in fashionable endpoint defenses.
The FLUX#CONSOLE marketing campaign serves as a wake-up name for the cybersecurity group. By exploiting trusted instruments like .MSC recordsdata and leveraging superior obfuscation methods, attackers proceed to evade conventional defenses.
As such campaigns evolve, strong safety options and proactive menace intelligence are important to remain forward of cybercriminals.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free

