Latest cybersecurity analysis has uncovered a regarding pattern the place hackers are exploiting Microsoft Groups to realize distant entry to sufferer programs.
Using subtle social engineering techniques, these malicious actors pose as reliable workers or trusted contacts, leveraging video calls on Microsoft Groups to deceive customers into downloading dangerous software program.
The assault usually begins with an onslaught of phishing emails designed to create confusion or urgency.
As soon as the sufferer is primed, the attacker initiates a Microsoft Groups name, impersonating an worker from a identified firm or a trusted exterior provider.

Throughout this name, the fraudulent consultant instructs the consumer to obtain distant desktop software program, supposedly for troubleshooting functions.
In a notable case, the attacker initially tried to information the sufferer to obtain a Microsoft Distant Assist utility, however after a failed set up, they instructed the usage of AnyDesk as an alternative.
This distant entry device, as soon as put in, grew to become the vector for deploying DarkGate malware, permitting the attacker to grab management over the sufferer’s pc.
2024 MITRE ATT&CK Analysis Outcomes Launched for SMEs & MSPs -> Obtain Free Information
The Function of DarkGate Malware
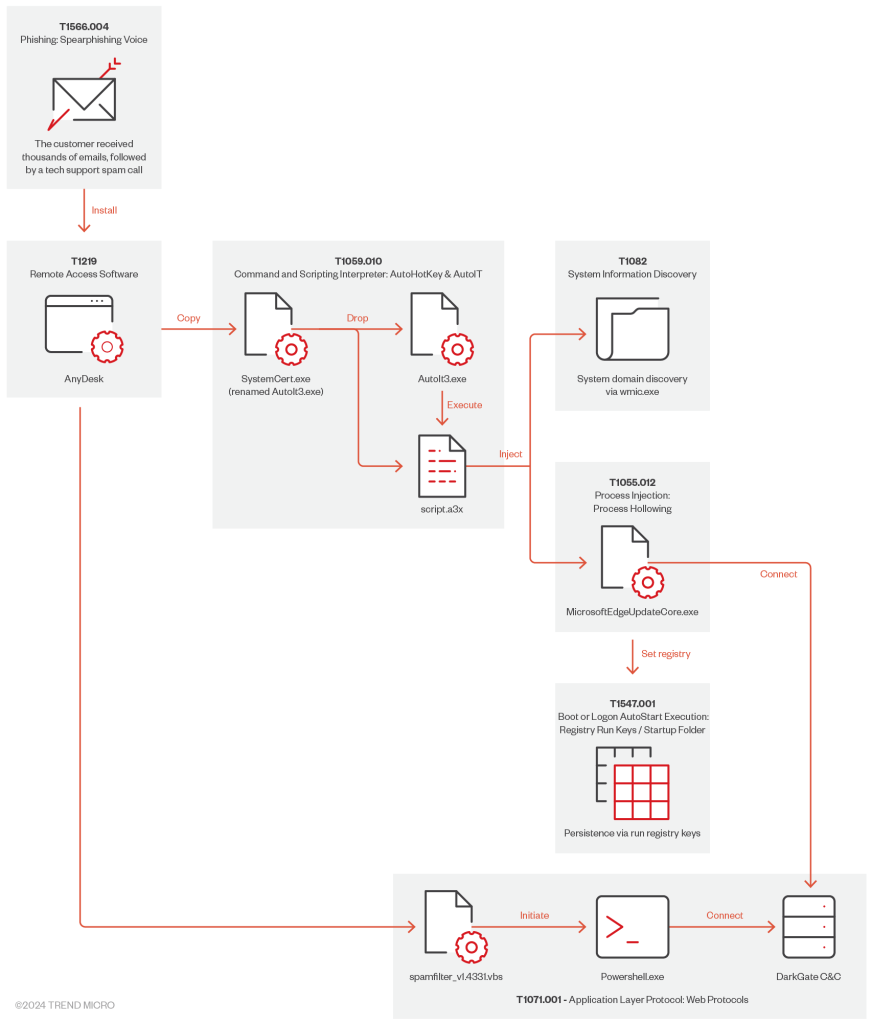
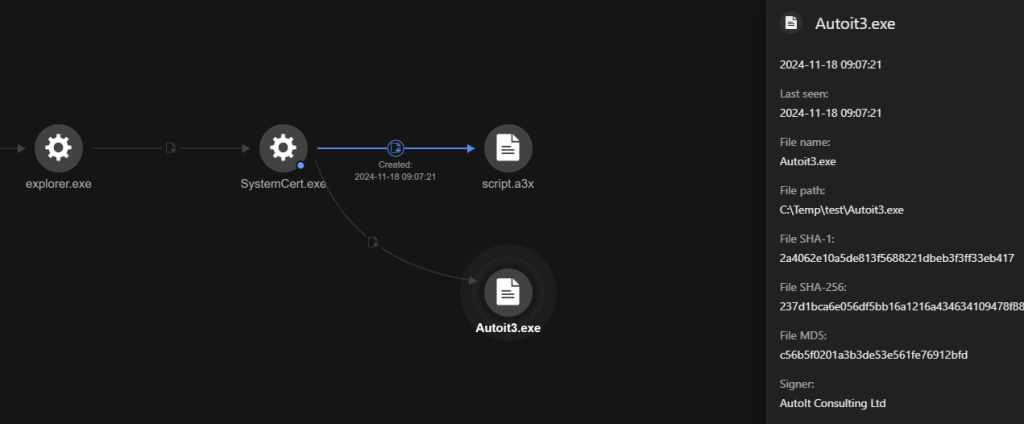
DarkGate malware is a formidable risk distributed through an AutoIt script. Its capabilities embody executing distant instructions, gathering delicate system info, and establishing a reference to a command-and-control server.
The malware is executed seconds after AnyDesk is put in, the place instructions are issued to run it as an area service with elevated privileges.
processCmd: "C:WindowsSystem32cmd.exe"
eventSubId: 2 - TELEMETRY_PROCESS_CREATE
objectFilePath: c:windowssystem32rundll32.exe
objectCmd: rundll32.exe SafeStore.dll,epaas_request_cloneThis entry grants the attacker the power to carry out varied malicious actions, together with injecting further malware into processes and manipulating community configurations.
The subtle execution circulation even permits the malware to load into reliable system processes to obfuscate its presence and exercise.

To defend in opposition to these superior threats, organizations should undertake complete safety methods.
Firstly, worker coaching is essential, specializing in the popularity of phishing makes an attempt and the risks of unsolicited help calls.
A well-informed workforce can considerably cut back the chance of profitable social engineering assaults. Secondly, implementing strict verification protocols for third-party interactions can forestall unauthorized entry.
This contains verifying the identification of any exterior help personnel. Moreover, organizations ought to limit the usage of distant desktop instruments, allowing solely these functions which have been completely vetted and authorized.
The enforcement of multi-factor authentication (MFA) on distant entry instruments gives a further layer of protection, requiring a number of types of verification to entry programs, as per a report by Pattern Micro.
The misuse of Microsoft Groups as a platform for cyberattacks underscores the evolving panorama of cybersecurity threats.
As communication instruments develop into integral to enterprise operations, additionally they current new vulnerabilities for exploitation.
To counter these rising threats, organizations should improve their safety measures, combining worker schooling with superior technological defenses.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Strive for Free


