
Web safety big Cloudflare introduced that it misplaced 55% of all logs pushed to prospects over a 3.5-hour interval because of a bug within the log assortment service on November 14, 2024.
Cloudflare presents an intensive logging service to prospects that permits them to observe the visitors on their website and filter that visitors primarily based on sure standards.
These logs enable prospects to research visitors to their hosts to observe and examine safety incidents, troubleshooting, DDoS assaults, visitors patterns, or to carry out website optimizations.
For patrons who want to analyze these logs utilizing exterior instruments, Cloudflare presents a “logpush” service that collects logs from its numerous endpoints and pushes them out to exterior storage companies, akin to Amazon S3, Elastic, Microsoft Azure, Splunk, Google Cloud Storage, and so on.
These logs are generated at an enormous scale, as Cloudflare processes over 50 trillion buyer occasion logs each day, of which round 4.5 trillion logs are despatched to prospects.
A cascade of failsafe failures
Cloudflare says a bug within the logpush service precipitated buyer logs to be misplaced for 3.5 hours on November 14.
“On November 14, 2024, Cloudflare skilled an incident which impacted the vast majority of prospects utilizing Cloudflare Logs,” explains Cloudflare.
“Throughout the roughly 3.5 hours that these companies have been impacted, about 55% of the logs we usually ship to prospects weren’t despatched and have been misplaced.”
The incident was attributable to a misconfiguration in Logfwdr, a key part in Cloudflare’s logging pipeline accountable for forwarding occasion logs from the corporate’s community to downstream techniques.
Particularly, a configuration replace launched a bug that issued a ‘clean configuration,’ wrongly telling the system that there have been no prospects whose logs have been configured to be forwarded, and thus the logs have been discarded.
Logfwdr is designed with a failsafe that defaults to forwarding all logs in case of ‘clean’ or invalid configurations to stop knowledge loss.
Nonetheless, this failsafe system precipitated an enormous spike within the quantity of logs being processed because it tried to ahead logs for all prospects.
It overwhelmed Buftee, a distributed buffering system that holds logs briefly when downstream techniques can not course of them in real-time, which was referred to as to deal with 40 occasions extra logs than its provisioned capability.
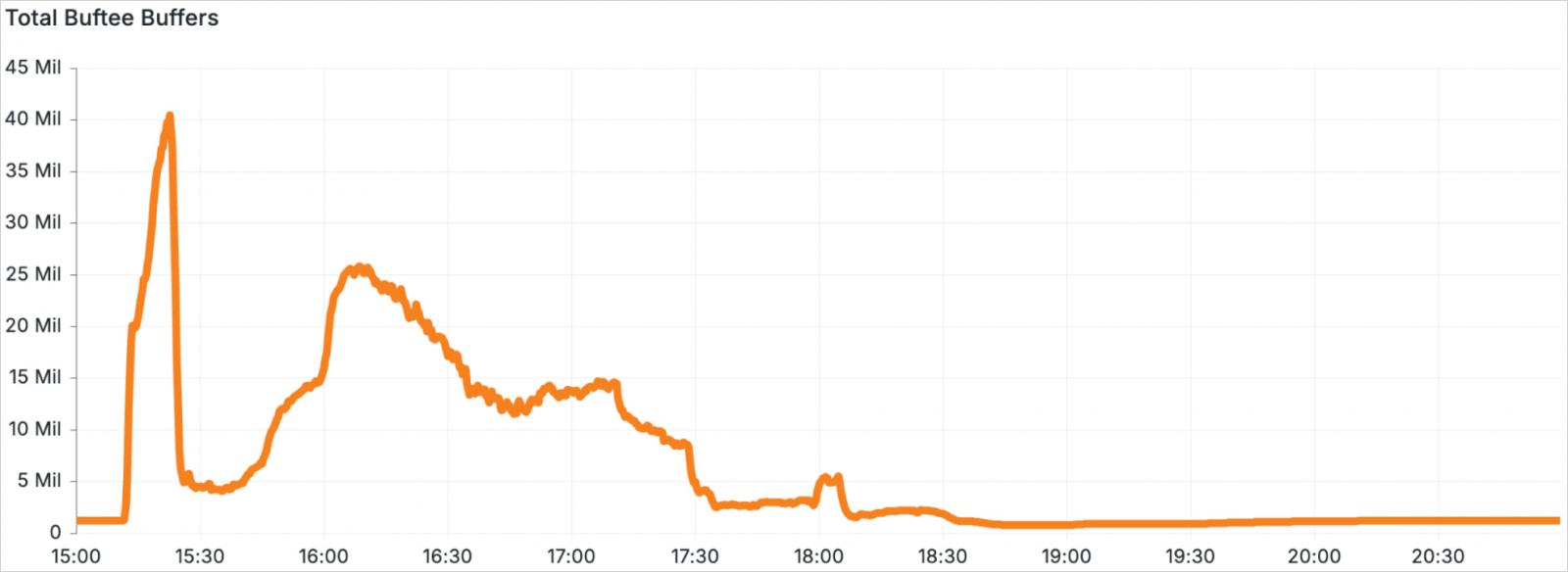
Supply: Cloudflare
Buftee options its personal set of buffer overload safeguards like useful resource caps and throttling, however these failed because of improper configuration and lack of earlier testing.
Consequently, inside simply 5 minutes of the misconfiguration in Logfwdr, Buftee shut down and required an entire restart, additional delaying restoration and ensuing within the lack of much more logs.
Stronger measures
In response to the incident, Cloudflare has carried out a number of measures to stop future occurrences.
This consists of the introduction of a devoted misconfiguration detection and alerting system to inform groups instantly when anomalies in log forwarding configurations are noticed.
Furthermore, Cloudflare says it has now appropriately configured Buftee to stop spikes in log volumes from inflicting full system outages.
Lastly, the corporate plans to routinely conduct overload exams simulating surprising surges in knowledge volumes, guaranteeing that each one steps of the failsafe mechanisms are strong sufficient to deal with these occasions.
