On my Home windows 11 machine, at 10.204.221.106, I am operating a netcat listener:
ncat.exe -lv 31415
On macOS Sequoia 15.0.1, I can efficiently connect with the Home windows machine with nc like this:
(base) Andrews-Mini-2:MacOS andrewtapia$ nc 10.204.221.106 31415
howdy
there
^C
However I get an error utilizing telnet:
(base) Andrews-Mini-2:MacOS andrewtapia$ telnet 10.204.221.106 31415
Making an attempt 10.204.221.106...
telnet: join to handle 10.204.221.106: No path to host
telnet: Unable to connect with distant host
Telnet is model 303.141.1 of this brew formulation.
Until I run telnet with sudo:
(base) Andrews-Mini-2:MacOS andrewtapia$ sudo telnet 10.204.221.106 31415
Making an attempt 10.204.221.106...
Related to tatl.
Escape character is '^]'.
howdy
there
^]
telnet> Connection closed.
Evidently, this works even when I take advantage of sudo to develop into a non-root consumer, e.g., sudo -u no one telnet 10.204.221.106 31415.
I believed perhaps this was a firewall situation on the Mac facet, however the System Settings declare that the firewall is off. What may very well be inflicting this downside?
Routing tables:
(base) Andrews-Mini-2:~ andrewtapia$ netstat -rnf inet
Routing tables
Web:
Vacation spot Gateway Flags Netif Expire
default 10.204.221.1 UGScg en0
default 10.204.221.1 UGScIg en1
default hyperlink#25 UCSIg bridge100 !
default hyperlink#27 UCSIg bridge101 !
default hyperlink#31 UCSIg bridge102 !
10.204.221/24 hyperlink#8 UCS en0 !
10.204.221/24 hyperlink#11 UCSI en1 !
10.204.221.1/32 hyperlink#8 UCS en0 !
10.204.221.1 a0:36:bc:75:66:18 UHLWIir en0 1180
10.204.221.1 a0:36:bc:75:66:18 UHLWIir en1 1197
10.204.221.1/32 hyperlink#11 UCSI en1 !
10.204.221.43/32 hyperlink#11 UCS en1 !
10.204.221.55/32 hyperlink#8 UCS en0 !
10.204.221.55 f0:18:98:ec:5a:9e UHLWI lo0
10.204.221.95 3c:2a:f4:b9:e1:cd UHLWI en0 814
10.204.221.95 3c:2a:f4:b9:e1:cd UHLWI en1 814
10.204.221.106 f8:fe:5e:ae:c9:1e UHLWI en0 994
10.204.221.243 8a:ef:7a:f7:e3:a6 UHLWI en0 1114
10.204.221.243 8a:ef:7a:f7:e3:a6 UHLWIi en1 1114
10.204.221.255 ff:ff:ff:ff:ff:ff UHLWbI en0 !
127 127.0.0.1 UCS lo0
127.0.0.1 127.0.0.1 UH lo0
169.254 hyperlink#8 UCS en0 !
169.254 hyperlink#11 UCSI en1 !
169.254.145.12 cc:a7:c1:25:d5:48 UHLSW en0 !
169.254.169.254 hyperlink#8 UHLSW en0 !
169.254.223.239 cc:a7:c1:25:d5:48 UHLSW en0 !
172.16.33/24 hyperlink#27 UC bridge101 !
172.16.169/24 hyperlink#25 UC bridge100 !
192.168.14 hyperlink#31 UC bridge102 !
224.0.0/4 hyperlink#8 UmCS en0 !
224.0.0/4 hyperlink#11 UmCSI en1 !
224.0.0.251 1:0:5e:0:0:fb UHmLWI en0
224.0.0.251 1:0:5e:0:0:fb UHmLWI en1
224.0.0.251 1:0:5e:0:0:fb UHmLWIg bridge101
224.0.0.251 1:0:5e:0:0:fb UHmLWIg bridge102
239.255.255.250 1:0:5e:7f:ff:fa UHmLWI en0
239.255.255.250 1:0:5e:7f:ff:fa UHmLWI en1
255.255.255.255/32 hyperlink#8 UCS en0 !
255.255.255.255/32 hyperlink#11 UCSI en1 !
Path to 10.204.221.106:
(base) Andrews-Mini-2:~ andrewtapia$ route -n get 10.204.221.106
path to: 10.204.221.106
vacation spot: 10.204.221.106
interface: en0
flags:
recvpipe sendpipe ssthresh rtt,msec rttvar hopcount mtu expire
0 0 0 0 0 0 1500 920
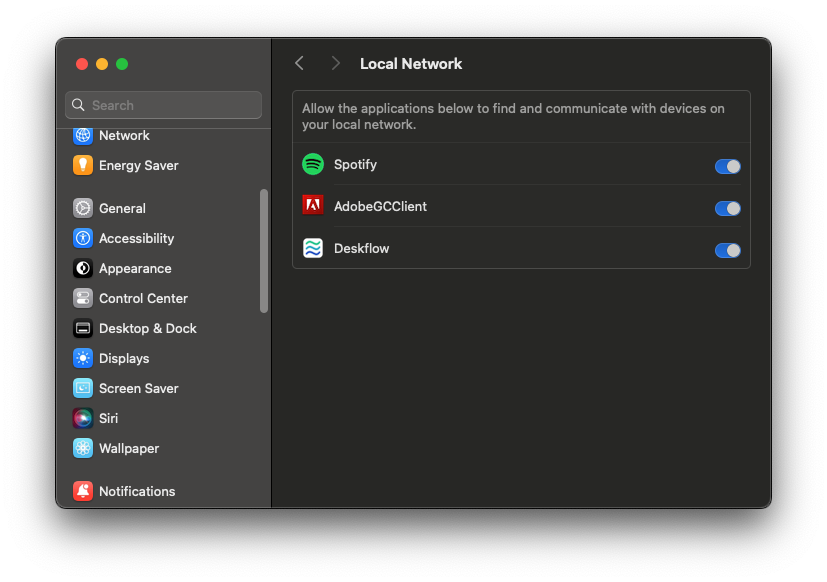
System Settings > Common > Privateness & Safety > Native Community settings:
Outputs of tcpdump -vvv -X -ni en0 -w capX.pcap 'port 31415 or arp' for: