Government Abstract
Establishing persistence on a system permits a risk actor continued entry or course of execution throughout system restarts or different modifications. Because of this, monitoring for and investigating persistence indicators are key elements of any strong cybersecurity platform.
Two widespread persistence methods are utilizing AutoStart Execution of packages throughout system boot or logon (T1547) and abusing scheduled process capabilities (T1053). Nevertheless, official software exercise additionally ceaselessly includes AutoStart Execution and scheduled process capabilities, so defending in opposition to these methods requires not solely detection monitoring but in addition evaluation by a cybersecurity skilled.
Throughout a current incident involving a LevelBlue MDR SOC buyer, an alarm that triggered for a Home windows Autorun registry key for persistence was traced again to a doubtlessly undesirable software (PUA). The PUA purportedly was appearing as a PDF conversion software. A evaluate of the preliminary alarm and related occasions revealed that the appliance had established a double layer of persistence through the use of each Scheduled Process creation and Autorun registry keys to execute JavaScript beneath the guise of a Chrome browser extension. Further open-source intelligence (OSINT) instruments recognized the appliance as both a PUA or a doubtlessly malicious file. An investigation was created for the client with remediation suggestions and in the end it was confirmed that the appliance was neither anticipated nor licensed throughout the buyer’s surroundings, and it was eliminated.
The identical software was later detected in one other buyer’s surroundings, however on this case, the client had added a associated file hash to an exclusion checklist. As a result of the LevelBlue MDR SOC analyst had just lately investigated the appliance and recognized it as doubtlessly malicious, they have been capable of suggest eradicating the hash from the exclusion checklist and as an alternative including it to a blocklist.
Investigation
Preliminary Alarm Assessment
The investigation started with the LevelBlue analyst receiving an alarm {that a} Home windows Autorun registry key named “ChromeBrowserAutoLaunch” had been added on an endpoint within the buyer surroundings. Whereas at first look this gave the impression to be a key set to auto-launch Chrome with a browser extension loaded, evaluation of the supply course of command line revealed a number of objects that warranted additional investigation.
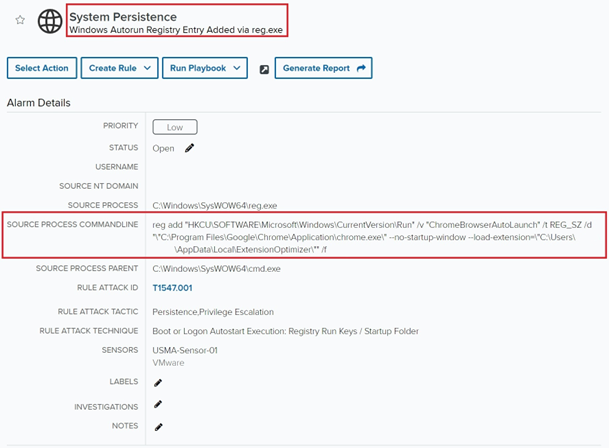
Determine 1: The preliminary alarm for the autorun registry key creation
- The “–no-startup-window” possibility: though that is generally used for official functions, it will possibly additionally point out an try to cover exercise from the top consumer. The pathway of the extension being loaded confirmed it was not an extension that the consumer had put in from the Chrome webstore. The anticipated pathway for extensions from the webstore could be “C:Customers<username>AppDataLocalGoogleChromeUser DataDefaultExtensions”. Whereas a sideloaded extension might nonetheless be official, this gave extra trigger to establish the origin of the registry key and extension.
- No verifiable browser extension with the title “Extension Optimizer” was present in OSINT queries.
- Abuse of browser extensions (T1176) is a recognized approach and malicious extensions have a historical past of getting used for infostealing, adware, and browser hijack or redirect behaviors.
Expanded Investigation
Occasions Search
The analyst carried out an occasion search to establish the origin of the browser extension “ExtensionOptimizer”. This search returned course of creation occasions that exposed the registry key was being added by a node.exe JavaScript course of executing from an AppData folder named “PDFFlex” within the pathway “C:Customers<username>AppDataLocalPDFFlexnode.exe”. A further occasion was logged on the similar time displaying that node.exe was additionally getting used to load the extension manually.
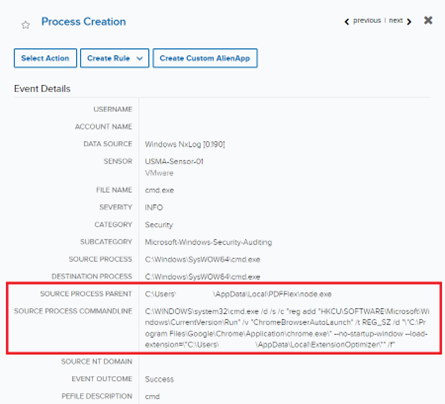
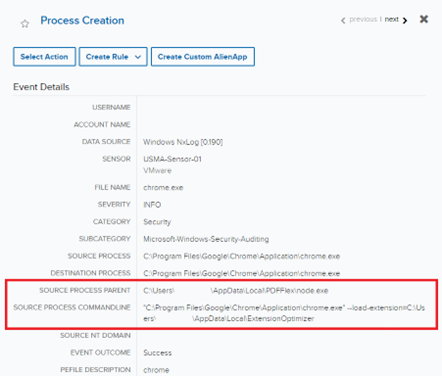
Determine 2: Occasions displaying the registry keys origin and handbook loading of the extension
The analyst looked for “PDFFlex” to grasp if the appliance was widespread within the buyer’s surroundings and to acquire extra artifacts concerning its origin or nature. The search revealed the appliance’s presence was anomalous and in addition uncovered occasions that may very well be used for additional analysis.
The analyst obtained the filename of the appliance’s MSI installer, the model and writer of the appliance, and an occasion that confirmed the creation of a each day scheduled process. This process was configured to execute “node.exe replace.js –check-update” from the identical “PDFFlex” folder pathway seen within the registry creation occasions. Additional evaluation confirmed that this process was accountable for executing the method that was creating the Autorun registry key in an obvious double layer of persistence established on the endpoint.
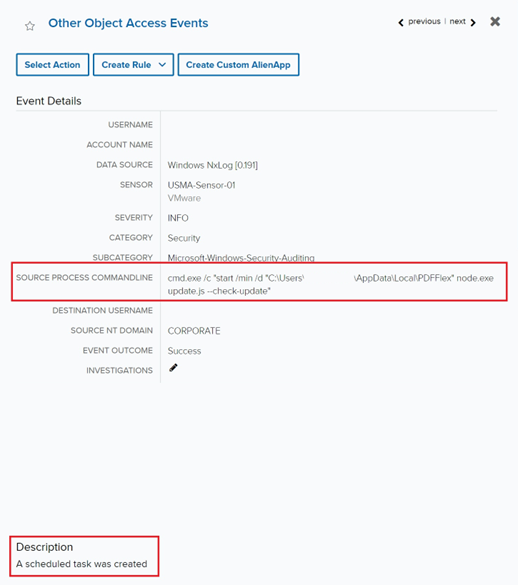
Determine 3: Scheduled process created to persistently add the registry key every day
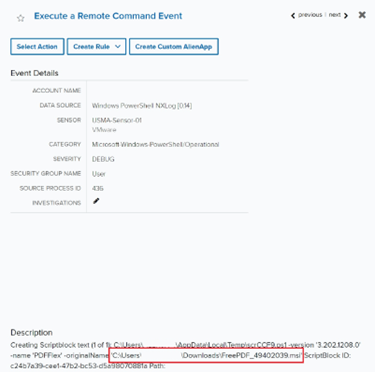
Determine 4: Occasion displaying the title of the appliance’s MSI installer file discovered within the consumer’s downloads folder
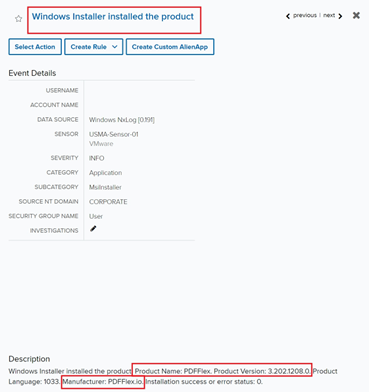
Determine 5: Set up occasion displaying the model and writer of the appliance “PDFFlex”
Occasion Deep-Dive
The analyst then carried out a number of OSINT searches utilizing the data obtained in occasion searches to confirm the use case and potential legitimacy of the appliance.
- No verifiable info was discovered for the MSI file “FreePDF_49402039.msi” or the writer PDFFlex.io.
- The analyst carried out a Whois search of the area “pdfflex.io” and located that it was not registered.
- An online seek for “PDFFlex 3.202.1208.0” returned a verdict of “malicious exercise” from the sandbox instrument ANY.RUN, which supplied a SHA256 file hash of 9c5d756045fd479a742b81241ccf439d02fc668581a3002913811a341278de43.
- A search of the hash on VirusTotal revealed that it had been flagged as doubtlessly malicious by a number of safety distributors, together with Sophos and Fortinet.
- The analyst leveraged SentinelOne Deep Visibility to substantiate that the hash for the MSI file on the client’s endpoint matched the hash within the ANY.RUN report. On the time of the alarm, incidents weren’t being triggered on the hash. The SentinelOne instrument additionally confirmed that the MSI file was signed by “Eclipse Media Inc,” which proved key in a later incident for one more LevelBlue buyer.
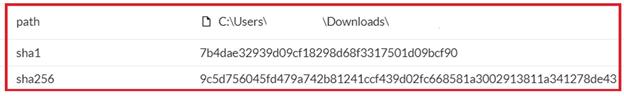
Determine 6:Deep Visibility search in SentinelOne displaying the file hash for the MSI file discovered on the endpoint
Response
Constructing the Investigation
The analyst’s investigation and OSINT analysis returned a number of factors to point that the “PDFFlex” software was seemingly not a desired software within the surroundings:
- The presence of the appliance on the endpoint was anomalous for the surroundings as occasions for it weren’t noticed for different endpoints.
- The applying had established what gave the impression to be a double layer of persistence through the use of a scheduled process and autorun registry key to create and launch an unverified browser extension “ExtensionOptimizer.”
- OSINT reviews for the MSI file indicated doubtlessly malicious habits.
Collectively, these information factors indicated that the appliance was neither desired nor anticipated within the buyer surroundings and may very well be labeled as a PUA/PUP, if not as outright malicious, and thus needs to be faraway from the endpoint.
Buyer Interplay
The analyst created an investigation that detailed the findings concerning the appliance “PDFFlex,” the browser extension “ExtensionOptimizer,” the noticed persistence behaviors, and the findings of the OSINT analysis. They beneficial that the client reimage the endpoint or take away the related AppData folders for “PDFFlex” and “ExtensionOptimizer” the scheduled duties, and the related registry keys. Shortly after the preliminary investigation, the LevelBlue MDR SOC recognized one other endpoint within the buyer’s surroundings that was exhibiting the identical persistence indicators beneath the appliance title “PDFTool.” The shopper confirmed that the functions weren’t licensed and in the end elected to take away the endpoints from service and change them.
Whereas the MSI file initially didn’t set off an alarm, a number of days after the investigation, its hash was added to the SentinelOne Cloud world blocklist and commenced to set off alarms. Throughout evaluate of one in all these for one more buyer, a LevelBlue analyst discovered that the client had added a hash-based exclusion for a equally named pdf-related MSI file with a unique file hash but in addition signed by “Eclipse Media Inc.”
This buyer had beforehand noticed the risk however added the hash to the exclusion checklist in SentinelOne resulting from no damaging reviews noticed whereas researching the file utilizing OSINT instruments. The LevelBlue staff’s information of the signer “Eclipse Media Inc” together with their current evaluation of the appliance allowed them to tell the client in regards to the dangers of the appliance. Based mostly on the analyst’s advice, the exclusion was eliminated and a blocklist motion for the alternate hash was added as an alternative.
Conclusion
This incident highlights not solely the necessity for monitoring and alerting on scheduled process and Autorun registry key creation but in addition the worth of getting professional evaluation of those occasions. On this investigation, the analyst’s use of OSINT and sandboxing instruments corresponding to ANY.RUN supplied the vital context wanted to guard the client’s surroundings from threats. As well as, the analyst’s analysis and prior information of the file signer “Eclipse Media Inc” later proved key in defending one other LevelBlue buyer that had created an exclusion for what was seemingly the identical PUA beneath a unique file hash.
