Sophos MDR has noticed a brand new marketing campaign that makes use of focused phishing to entice the goal to obtain a reliable distant machine administration device to dump credentials. We consider with average confidence that this exercise, which we observe as STAC 1171, is expounded to an Iranian risk actor generally known as MuddyWater or TA450.
The primary tracked incident was earlier in November, when Sophos endpoint behavioral guidelines blocked credential dumping exercise concentrating on a corporation in Israel. In assessing the exercise, we discovered indicator and TTP overlap with reporting by Proofpoint on TA450. The actor gained preliminary entry via a phishing electronic mail directing the person to open a shared doc hosted at hxxps[://]ws[.]onehub[.]com/information/ and obtain a file named ‘New Program ICC LTD.zip’.
The ‘New Program ICC LTD.zip’ archive contained a compressed installer file for reliable distant monitoring and administration (RMM) device Atera. The Atera set up used a trial account registered to an electronic mail handle we consider was compromised. Upon putting in Atera Agent, the risk actors used Atera distant run instructions to execute a PowerShell script (a.ps1) with the objective of dumping credentials and making a backup file of the SYSTEM registry hive. This credential dumping exercise was detected and blocked by Sophos behavioral guidelines:
“cmdline”: “C:WINDOWSsystem32reg.exe” save HKLMSYSTEM SystemBkup.hiv”
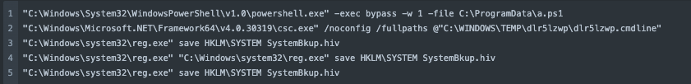
Submit-compromise actions in Atera additionally included:
- A number of area enumeration instructions;
- An SSH tunnel in direction of 51.16.209[.]105;
- An obfuscated PowerShell command used to obtain the Degree RMM device (at hxxps[:]//downloads.stage.io/install_windows.exe).
We have now seen telemetry of one other Sophos non-MDR buyer in america that follows the identical habits. Sophos X-Ops will proceed to observe this exercise and replace with any additional info on this risk cluster.
