
Greater than 60,000 D-Hyperlink network-attached storage gadgets which have reached end-of-life are weak to a command injection vulnerability with a publicly out there exploit.
The flaw, tracked as CVE-2024-10914, has a important 9.2 severity rating and is current within the ‘cgi_user_add’ command the place the title parameter is insufficiently sanitized.
An unauthenticated attacker may exploit it to inject arbitrary shell instructions by sending specifically crafted HTTP GET requests to the gadgets.
The flaw impacts a number of fashions of D-Hyperlink network-attached storage (NAS) gadgets which can be generally utilized by small companies:
- DNS-320 Model 1.00
- DNS-320LW Model 1.01.0914.2012
- DNS-325 Model 1.01, Model 1.02
- DNS-340L Model 1.08
In a technical write-up that gives exploit particulars, safety researcher Netsecfish says that leveraging the vulnerability requires sending “a crafted HTTP GET request to the NAS system with malicious enter within the title parameter.”
curl "http://[Target-IP]/cgi-bin/account_mgr.cgi cmd=cgi_user_add&title=%27;
“This curl request constructs a URL that triggers the cgi_user_add command with a reputation parameter that features an injected shell command,” the researcher explains.
A search that Netsecfish performed on the FOFA platform returned 61,147 outcomes at 41,097 distinctive IP addresses for D-Hyperlink gadgets weak to CVE-2024-10914.
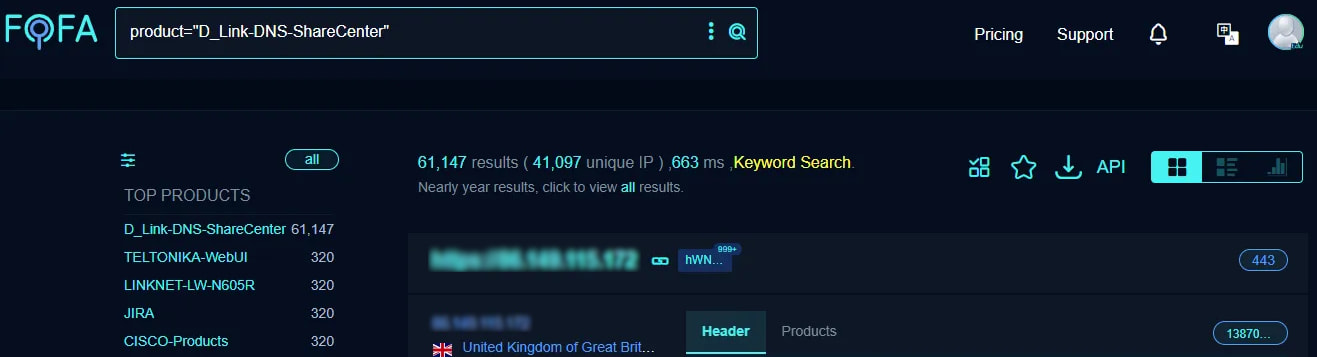
Supply: Netsecfish
In a safety bulletin right this moment, D-Hyperlink has confirmed {that a} repair for CVE-2024-10914 will not be coming and the seller recommends that customers retire weak merchandise.
If that isn’t attainable in the mean time, customers ought to a minimum of isolate them from the general public web or place them beneath stricter entry circumstances.
The identical researcher found in April this 12 months an arbitrary command injection and hardcoded backdoor flaw, tracked as CVE-2024-3273, impacting principally the identical D-Hyperlink NAS fashions as the most recent flaw.
Again then, FOFA web scans returned 92,589 outcomes.
Responding to the scenario on the time, a D-Hyperlink spokesperson informed BleepingComputer that the networking agency not makes NAS gadgets, and the impacted merchandise had reached EoL and won’t be receiving safety updates.
