
Google has left Android customers puzzled after the newest replace to the Google cell app causes hyperlinks shared from the app to now be prepended with a mysterious “search.app” area.
Because the Google app is a well-liked portal for looking out the net for Android customers and delivers a personalised content material information feed known as Google Uncover, it has sparked concern amongst those that seen the brand new hyperlinks.
What are these mysterious search.app hyperlinks?
On November 6, 2024, Google rolled out its an Android model 15.44.27.28.arm64 of its app.
Ever since then, hyperlinks considered in Google’s in-app Chromium browser, when shared externally, are being prepended with a “search.app” area.
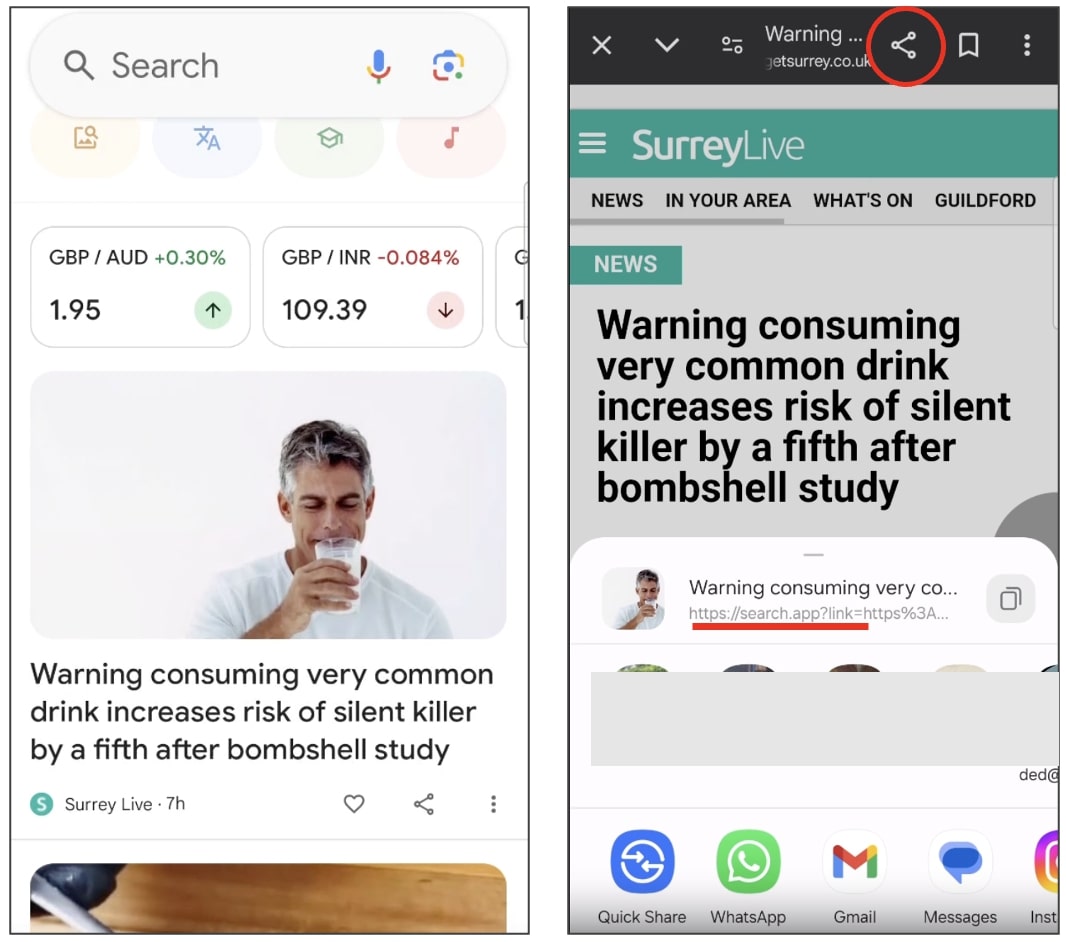
BleepingComputer seen the behaviour shortly after updating our Google app and we admit, the sight of a mysterious area left us alarmed at first. Was our machine compromised by adware?
(BleepingComputer)
Our issues are echoed by different customers on Reddit this week.
“Lately (few days in the past), I seen that every hyperlink shared from the Google in-app net browser makes use of the ‘search.app’ area,” requested Reddit person danilopiazza.
“For instance, making an attempt to share the hyperlink to the Reddit entrance Web page, I get: https://search.app?hyperlink=httpspercent3Apercent2Fpercent2Fwww.reddit.compercent2F&utm_campaign=…&utm_source=…”
“Is that this a brand new function from the Google app?”
A reader responded, “It looks like it. I am getting this too. At first I assumed I used to be in some way contaminated with some sort of malware, or in some way some setting unbeknownst to me received modified.”
Comparable posts have emerged from others.
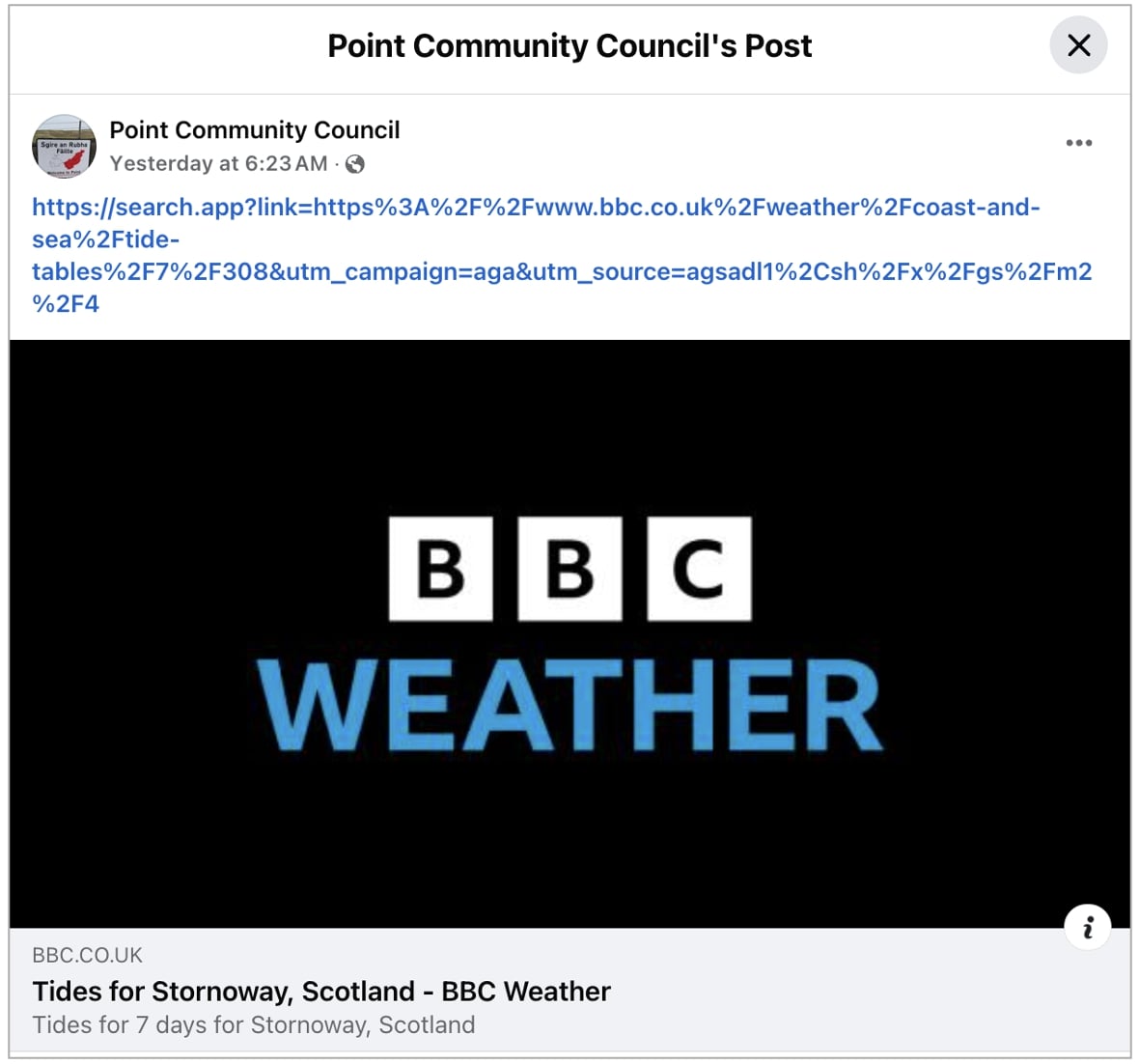
BleepingComputer noticed hyperlinks being shared by way of social media posts on X and Fb by way of Google’s Android app this week are bearing the “search.app” area too:
(BleepingComputer)
Is search.app protected?
Put merely, search.app is a URL redirector area, very like t.co utilized by X (previously Twitter), Google’s g.co, or Meta’s m.me.
Prepending hyperlinks with “https://search.app?hyperlink=” offers Google enhanced visibility into how hyperlinks are being externally shared by the Google app customers and who are clicking on these hyperlinks (i.e. referrers).
Along with accumulating analytics, by inserting itself between customers and exterior hyperlinks by utilizing the “search.app” area, Google now has the flexibility to dam visitors to phishing or hacked domains, ought to a web site go rogue, or within the occasion that customers are mass-sharing questionable content material with one another (reminiscent of a rip-off web site).
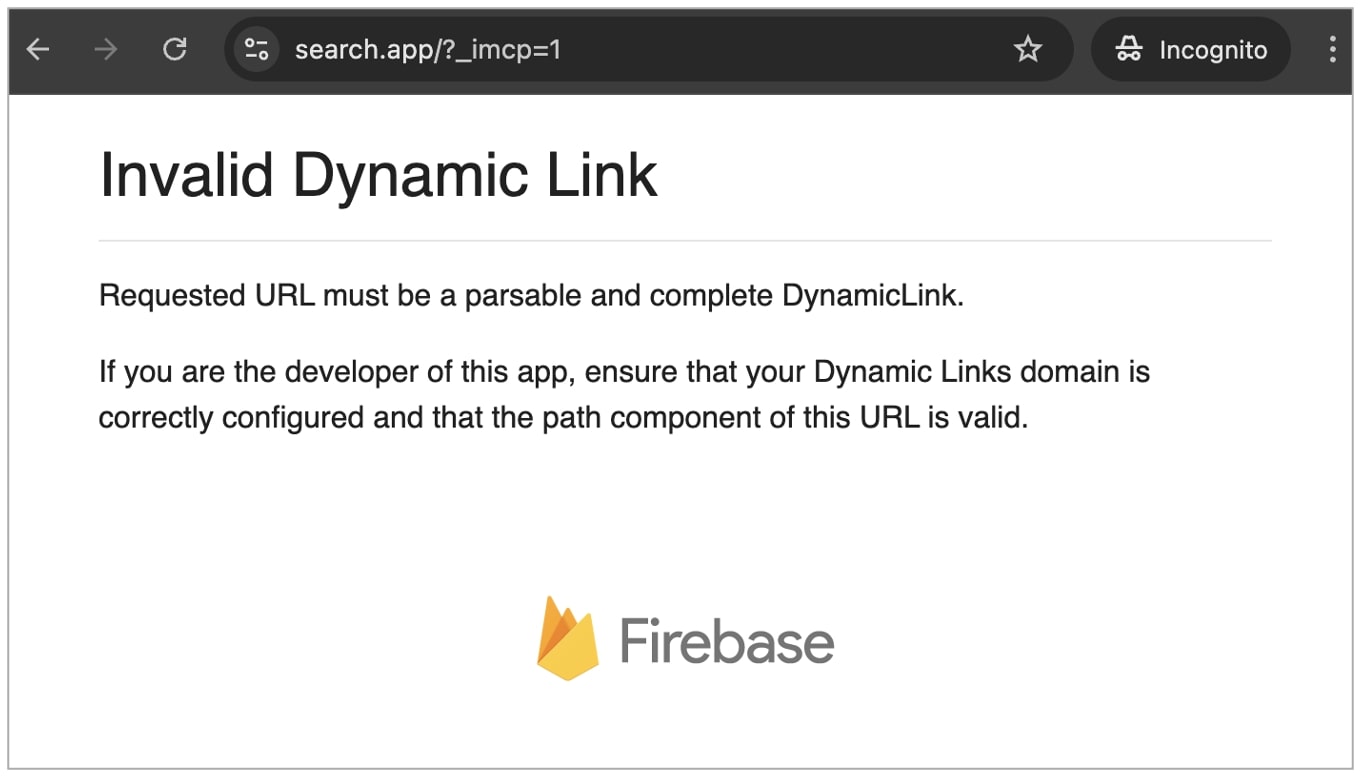
In our assessments, navigating to look.app straight took us to an “Invalid Dynamic Hyperlink” web page with a Firebase emblem.
(BleepingComputer)
Firebase was acquired in 2014 by Google and has since turn into “Google’s cell improvement platform that empowers you to rapidly construct and develop your app.”
We seen an analogous display when navigating to Google’s one other area: https://search.app.goo.gl/
Mockingly, Firebase Dynamic Hyperlinks are deprecated and set to be shut down by August 2025.
WHOIS data for each search.app and goo.gl present Google LLC because the registrant group and MarkMonitor because the registrar.
Shared TLS/SSL certificates and internet hosting
After publishing this piece, a number of BleepingComputer readers have identified an anomaly with SSL certificates issued to the ‘search.app’ area.
So as to add confusion, the SSL certificates issued to ‘search.app’ exhibits the Widespread Title (CN) as fallacni.com.
BleepingComputer additional seen that the identical SSL certificates is in use by greater than 100 domains, proven beneath, that are hosted on the identical Firebase server (IP tackle 199.36.158.100).
It’s potential that this because of using SSL/TLS applied sciences like Server Title Indication (SNI) which make it potential for a number of domains to be served over HTTPS on a shared internet hosting server, however is actually anomalous. For comparability, certificates of Google’s search.app.goo.gl area exhibits a CN set to ‘misc-sni.google.com’ and 216.58.212.206 as its server’s IP tackle.
fallacni.com
vireum.com
meatton.go1pos.com
digitley.co.in
www.mcseat.es
portfos.in
app.eluminate.in
dailypostbeat.com
www.hertzog-psychologue.fr
www.kanau.web page
venits.com
www.weiwhite.com
jzz.me
golden-notes.io
peacedollar.org
ing-v3.sudahdistaging.in
merchantinstall.iomd.data
search.app
www.instructions.healthcare
jellyjam.io
www.oeson.in
www.cutrite.app
api.onflix.app
cmouse.app
www.preaching.app
doc-internal.dalek.rs
honeycome.jp
podium.instruments
www.dreamlin.com
fireacademy.io
mumbai.toobzgaming.com
risingstar.blackmint.io
qanda.hyperlink
editor.agua.app
aariz.me
hyperlink.nibo.com.br
site-result-auctions.farmgateauctions.com.au
beta.inhouseorders.io
typov.app
www.azvn.app
m.fiskal.app
genesix.ai
be part of.getostrich.app
swan-business-bugfix.ingogodev.web
compizza.lupi.supply
bm.fusheng.data
preparhub.ca
go.holler.io
assembly.skylar.ai
easterbay.org
make investments.scoutout.io
www.un-sichtbarespuren.de
cronometro.web
overthemoon.artwork
www.scenid.com
craftbyte.web
coloryourvoice.com
avantagecpo.com
fouronetwo.equiem.mobi
yo-dev.eparatodos.org
federalcafe.5loyalty.com
bstsst.com
b.ejsa.io
souscription.flitter.fr
flyvendas.com.br
flairtime.com
cinemetric.app
flyclub.app
www.endevagames.com
getpayify.app
justpic.app
selfy.ai
omnamo.app
davidvu.co.uk
console.shopezy.app
house.jooni.app
gpso.se
guicerpro.com
demo.pricely.app
speccon.cnfg.app
collctiv.app
productbacklog.dev
app1.posible.in
bookmark.undef.in
jeyhid.com
retro-it.com
rakesfieldandpeach.com
digitalnepalsolution.com
ryandine.com
dranandcardiocare.com
desiderioalmansa.com
vekend.com
strozu.com
hausasteri.com
bishoyriad.com
harshalplus.com
deliveryhub.app
eplise.com
ultrasiteservices.co.uk
reciproitsolutions.com
Whereas up to now, the search.app redirector URLs seems to be protected and formally operated by Google, the sheer lack of documentation surrounding the area is odd, as is the lack of its point out in public changelogs of Google’s open supply tasks, reminiscent of Android or Chromium.
The rollout of the search app replace is sure to alarm much more customers within the coming days who could surprise if their machine is behaving erratically or has been compromised by malware.
Is that is Google’s try at imitating Apple Information which prepends hyperlinks to exterior tales with https://apple.information?
Previously, Google Chrome’s use of unusual GVT1.com domains has drawn the scrutiny of even essentially the most expert researchers as a result of lack of public documentation surrounding these domains.
BleepingComputer approached Google for remark prematurely of publishing and we’re awaiting a response.
Replace, 8 November 2024 10:35 AM ET: Added part on ambigious SSL certificates offered by search.app.
