
Hackers are more and more focusing on Home windows customers with the malicious Winos4.0 framework, distributed through seemingly benign game-related apps.
The toolkit is the equal of Sliver and Cobalt Strike post-exploitation frameworks and it was documented by Pattern Micro this summer season in a report on assaults in opposition to Chinese language customers.
On the time, a risk actor tracked as Void Arachne/Silver Fox lured victims with provides of varied software program (VPNs, Google Chrome browser) modified for the Chinese language market that bundled the malicious part.
A report right now from cybersecurity firm Fortinet signifies an evolution within the exercise, with hackers now counting on video games and game-related recordsdata of their continued focusing on of Chinese language customers.

Supply: Fortinet
When the seemingly legit installers are executed, they obtain a DLL file from “ad59t82g[.]com” to provoke a multi-step an infection course of.
Within the first stage, a DLL file (you.dll) downloads further recordsdata, units up the execution setting, and establishes persistence by including entries within the Home windows Registry.
Within the second stage, injected shellcode hundreds APIs, retrieves configuration knowledge, and establishes a connection to the command-and-control (C2) server.
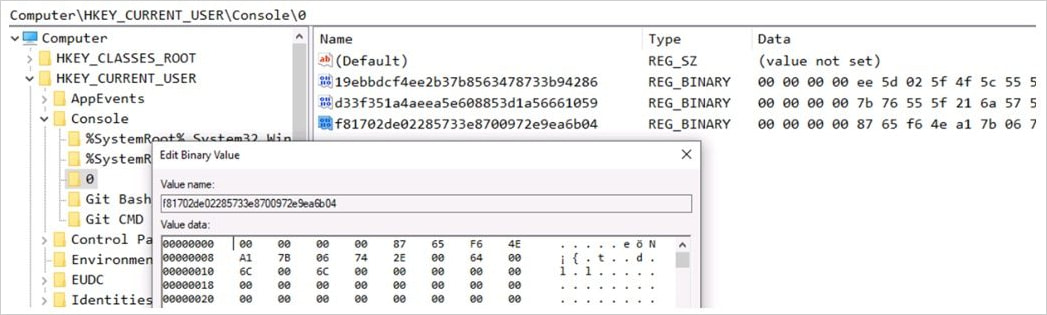
Within the third section, one other DLL (上线模块.dll) retrieves further encoded knowledge from the C2 server, shops it within the registry at “HKEY_CURRENT_USERConsole” and updates the C2 addresses.
Supply: Fortinet
Within the final stage of the assault chain, the login module (登录模块.dll) is loaded, which performs the first malicious actions:
- Collects system and setting info (e.g., IP handle, OS particulars, CPU).
- Checks for anti-virus and monitoring software program working on the host.
- Gathers knowledge on particular cryptocurrency pockets extensions utilized by the sufferer.
- Maintains a persistent backdoor connection to the C2 server, permitting the attacker to subject instructions and retrieve further knowledge.
- Exfiltrates knowledge after taking screenshots, monitoring for clipboard adjustments, and stealing paperwork.
.jpeg)
Supply: Fortinet
Winos4.0 checks for a wide range of safety instruments on the system, together with Kaspersky, Avast, Avira, Symantec, Bitdefender, Dr.Internet, Malwarebytes, McAfee, AhnLab, ESET, Panda Safety, and the now discontinued Microsoft Safety Necessities.
By figuring out these processes, the malware determines whether it is working in a monitored setting and adjusts its conduct accordingly, or halts execution.
Hackers have continued utilizing the Winos4.0 framework for a number of months now, and seeing new campaigns rising is a sign that its position in malicious operations seems to have solidified.
Fortinet describes the framework as a strong one which can be utilized to manage compromised programs, with performance much like Cobalt Strike and Sliver. Indicators of compromise (IoCs) can be found within the studies from Fortinet and Pattern Micro.

