
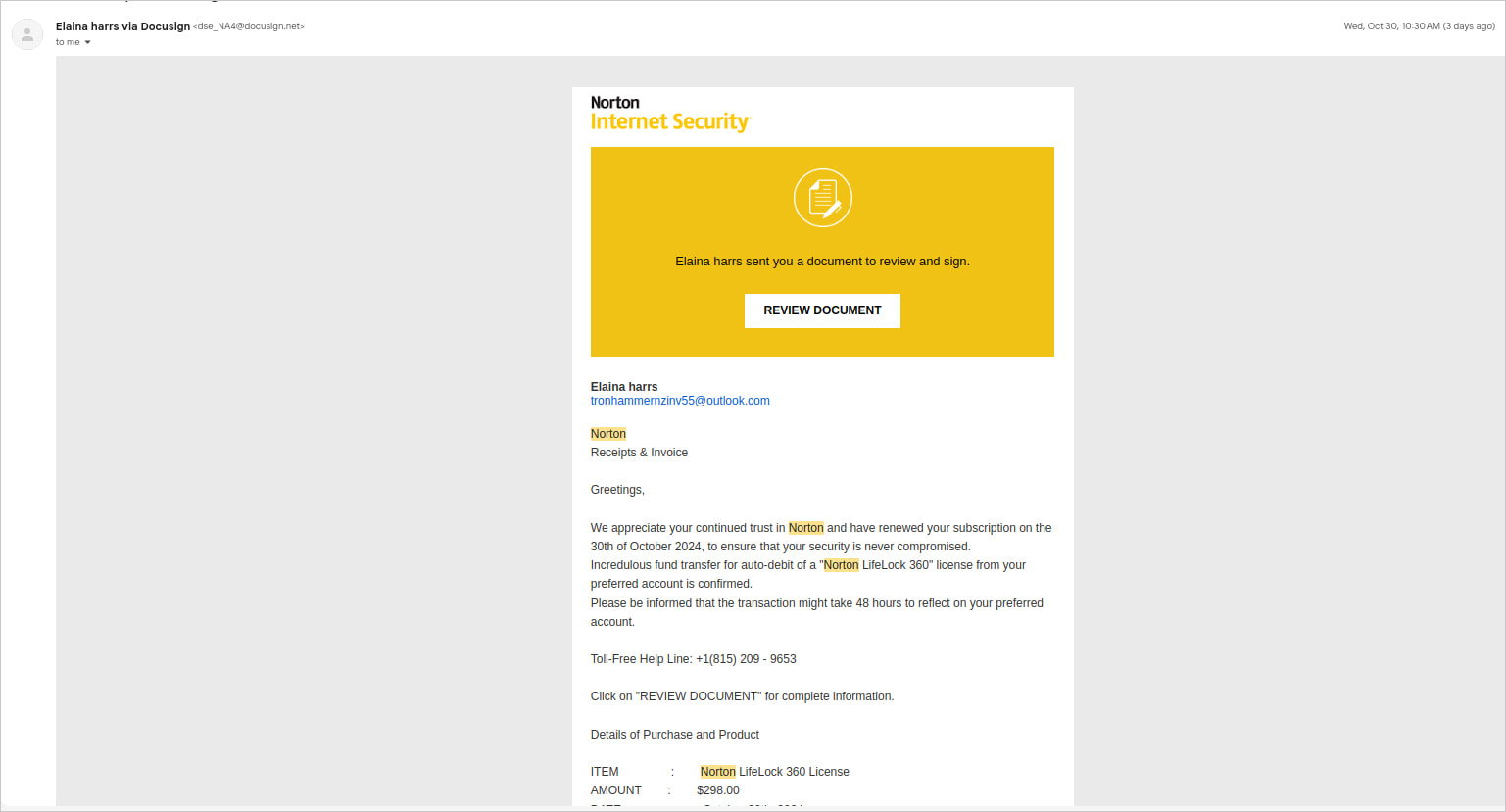
Risk actors are abusing DocuSign’s Envelopes API to create and mass-distribute faux invoices that seem real, impersonating well-known manufacturers like Norton and PayPal.
Utilizing a official service, the attackers bypass e-mail safety protections as they arrive from an precise DocuSign area, docusign.web.
The aim is to have their targets e-sign the paperwork, which they will then use to authorize funds independently from the corporate’s billing departments.
Supply: Wallarm
Sending sensible signature requests
DocuSign is an digital signature platform that permits digitally signing, sending, and managing paperwork.
The Envelopes API is a core element of DocuSign’s eSignature REST API, permitting builders to create, ship, and handle doc containers (envelopes) that outline the signing course of.
The API is supposed to assist prospects automate the sending of paperwork that want signing, monitor their standing, and retrieve them when signed.
Based on Wallarm safety researchers, risk actors utilizing official paid DocuSign accounts ary abusing this API to ship faux invoices that mimic the feel and appear of respected software program corporations.
These customers take pleasure in full entry to the platform’s templates, permitting them to design paperwork that resemble the impersonated entity’s branding and structure.
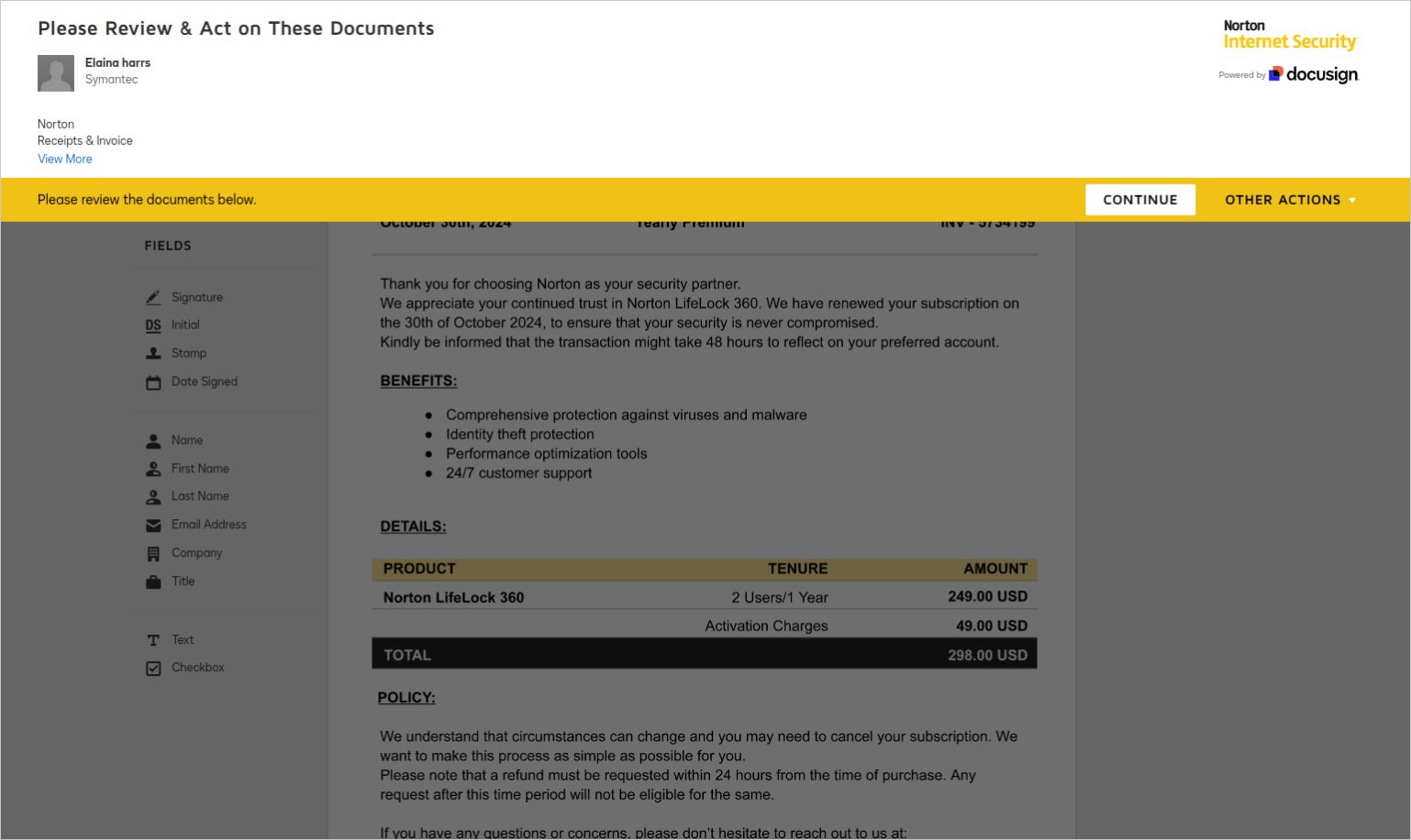
Subsequent, they use ‘Envelopes: create’ API perform to generate and ship a excessive quantity of fraudulent invoices to many potential victims.
Supply: Wallarm
Wallarm says the charges introduced in these invoices are saved to a sensible vary to extend the sense of legitimacy of the signing request.
“If customers e-sign this doc, the attacker can use the signed doc to request fee from the group exterior of DocuSign or ship the signed doc by way of DocuSign to the finance division for fee,” explains Wallarm.
“Different makes an attempt have included totally different invoices with totally different objects, often following the identical sample of getting signatures for invoices that then authorize fee into the attackers financial institution accounts.”
Massive-scale DocuSign abuse
Wallarm notes that this kind of abuse, which it has reported to DocuSign, has been happening for some time now, and prospects have reported the campaigns many instances on the platform’s neighborhood boards.
“I am immediately getting 3-5 phishing emails per week from the docusign.web area and none of the usual reporting e-mail addresses like abuse@ or admin@ work,” a buyer posted to the DocuSign boards.
“They reject my e-mail, and I can’t discover any reporting info on their FAQ web page. I suppose I am left with the selection of blocking the area?”
The assaults seem automated moderately than low-volume handbook makes an attempt, so the abuse happens on a big scale that needs to be onerous for the platform to overlook.
BleepingComputer has contacted DocuSign to ask about their anti-abuse measures and in the event that they plan to boost them towards the reported exercise, however a remark wasn’t instantly out there.
Sadly, API endpoints are onerous to safe when the risk actors create industrial accounts permitting entry to those options.
Some current examples of how hackers have abused APIs prior to now embrace verifying the cellphone numbers of hundreds of thousands of Authy customers, scraping the data of 49 million Dell prospects, and linking e-mail addresses to 15 million Trello accounts.

