ESET researchers have found new Rust-based tooling resulting in the deployment of Embargo ransomware. Embargo is a comparatively new participant within the ransomware scene, first noticed by ESET in June 2024. The brand new toolkit consists of a loader and an EDR killer, named MDeployer and MS4Killer respectively by ESET. MS4Killer is especially noteworthy as it’s customized compiled for every sufferer’s setting, focusing on solely chosen safety options. Each instruments are written in Rust, the Embargo group’s language of selection for growing its ransomware.
Key factors of this blogpost:
- Embargo is growing and testing new Rust-based tooling.
- Variations in deployed variations, bugs, and leftover artifacts recommend that these instruments are underneath lively growth.
- The risk actor abuses Secure Mode to disable safety options.
- Embargo tailors its instruments to every sufferer.
Overview
In July 2024, we noticed ransomware incidents focusing on US corporations, the place the risk actor utilized its new tooling. The variations of MDeployer and MS4Killer noticed in every intrusion differ barely, suggesting that the instruments are actively developed. Curiously, we noticed two completely different variations of MDeployer in a single intrusion, in all probability tweaked after a primary, failed try.
This blogpost focuses on the evaluation of MDeployer and MS4Killer and exercise previous the execution of the Embargo ransomware. MDeployer is a malicious loader used for deployment of MS4Killer and Embargo ransomware. MS4Killer is an EDR killer that abuses a weak driver to disable the safety merchandise operating on the sufferer’s machine.
Embargo
Embargo, noticed for the primary time in ESET telemetry in June 2024, made its public look in Might 2024. Aside from efficiently breaching high-profile targets, the group attracted consideration due to its selection of programming language for ransomware payload. Embargo selected Rust, a cross-platform programming language, permitting growth of extra versatile ransomware focusing on each Home windows and Linux. Coming after BlackCat and Hive, Embargo is yet one more group growing ransomware payloads in Rust.
Primarily based on its modus operandi, Embargo appears to be a well-resourced group. It units up its personal infrastructure to speak with victims (Determine 1), but additionally permits for communication by way of Tox. The group pressures victims into paying through the use of double extortion and publishes the stolen information on its leak web site. In an interview with an alleged group member, the group consultant mentions a fundamental payout scheme for associates, suggesting that the group is offering RaaS (ransomware as a service). Current legislation enforcement disruptions, affecting infamous teams like BlackCat and LockBit, triggered some reorganization within the RaaS area. These adjustments in world RaaS setting help the emergence of a classy new actor. Given the group’s sophistication, the existence of a typical leak web site, and the group’s claims, we assume that Embargo certainly operates as RaaS supplier.
Embargo ransomware payloads that we noticed through the July 2024 incidents share these attributes:
- Embargo ransomware drops its ransom word (Determine 2) named HOW_TO_RECOVER_FILES.txt in every encrypted listing.
- Encrypted recordsdata get hold of a random six-letter extension consisting of hexadecimal characters, e.g., .b58eeb or .3d828a.
- Payloads create the mutex IntoTheFloodAgainSameOldTrip.
In a earlier evaluation from Cyble researchers, payloads created the mutex LoadUpOnGunsBringYourFriends. Noticeably, each mutex names are based mostly on the lyrics of fashionable rock songs. Our evaluation is in keeping with that discovered within the Cyble article.
MDeployer
MDeployer is the primary malicious loader Embargo tries to deploy onto machines within the compromised community – it facilitates the remainder of the assault, leading to ransomware execution and file encryption.
Primarily based on the title discipline within the IMAGE_EXPORT_DIRECTORY part of its PE header, we are able to inform that Embargo calls this instrument Deployer. Thus, we determined to consult with it as MDeployer – EMbargo Deployer.
Its foremost objective is to decrypt two encrypted recordsdata a.cache and b.cache (dropped by an unknown earlier stage) and execute two payloads: MS4Killer and Embargo ransomware.
- It first makes an attempt to decrypt the MS4Killer payload from the file b.cache, drops the decrypted file into praxisbackup.exe, and executes it.
- Subsequent, it does the identical for the ransomware payload, which is decrypted from a.cache, saved as pay.exe, and executed.
- When the ransomware finishes encrypting the system, MDeployer terminates the MS4Killer course of, deletes the decrypted payloads and a driver file dropped by MS4Killer, and at last reboots the system.
MS4Killer is predicted to run indefinitely, and MDeployer verifies this by calling the API operate WaitForSingleObject, anticipating the return worth WAIT_TIMEOUT. If it’s not operating correctly, MDeployer logs the message sysmon exited early and exits with out executing the second payload. We talk about logging later on this blogpost.
In all MDeployer variations we’ve seen, each payloads had been decrypted utilizing the identical hardcoded RC4 key – wlQYLoPCil3niI7x8CvR9EtNtL/aeaHrZ23LP3fAsJogVTIzdnZ5Pi09ZVeHFkiB.
Throughout its execution, MDeployer interacts with a number of recordsdata. To ease understanding, Determine 3 demonstrates the connection between the recordsdata.
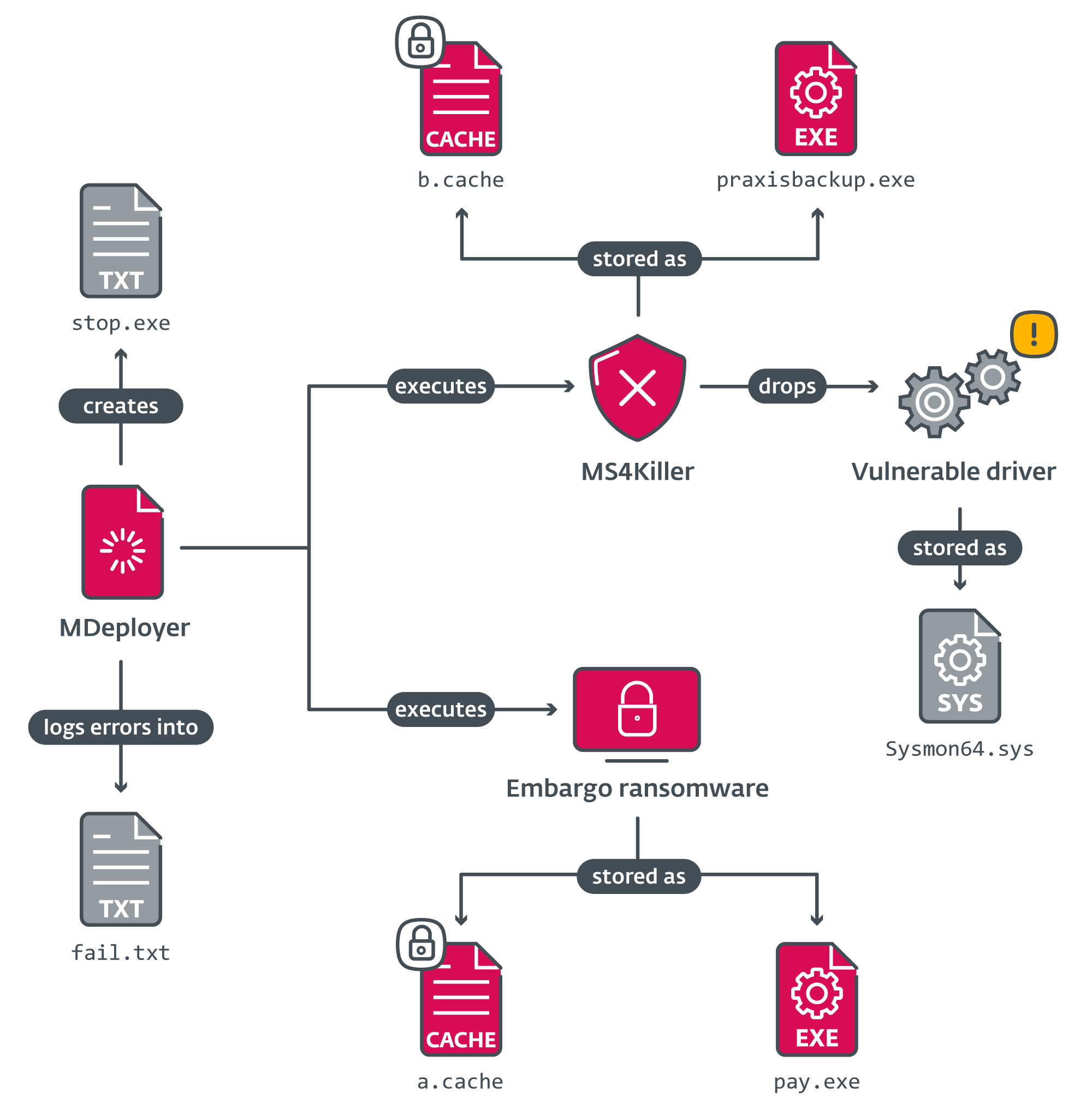
Desk 1 lists their functions.
Desk 1. Recordsdata manipulated by MDeployer
| Path | Description |
| C:WindowsDebugb.cache |
RC4-encrypted MS4Killer. |
| C:WindowsDebuga.cache |
RC4-encrypted Embargo ransomware. |
| C:Windowspraxisbackup.exe |
Decrypted MS4Killer. |
| C:WindowsDebugpay.exe |
Decrypted Embargo ransomware. |
| C:WindowsDebugfail.txt |
Log file. |
| C:WindowsDebugstop.exe |
Dummy file used for management movement. |
| C:WindowsSysmon64.sys |
Respectable weak driver dropped by MS4Killer. |
Secure Mode abuse
With just one exception among the many incidents we investigated, the place we noticed it deployed as a DLL, MDeployer was compiled as an EXE file. The DLL variant comprises the extra functionality to disable safety options.
For an outline of the DLL execution movement, consult with Determine 4.
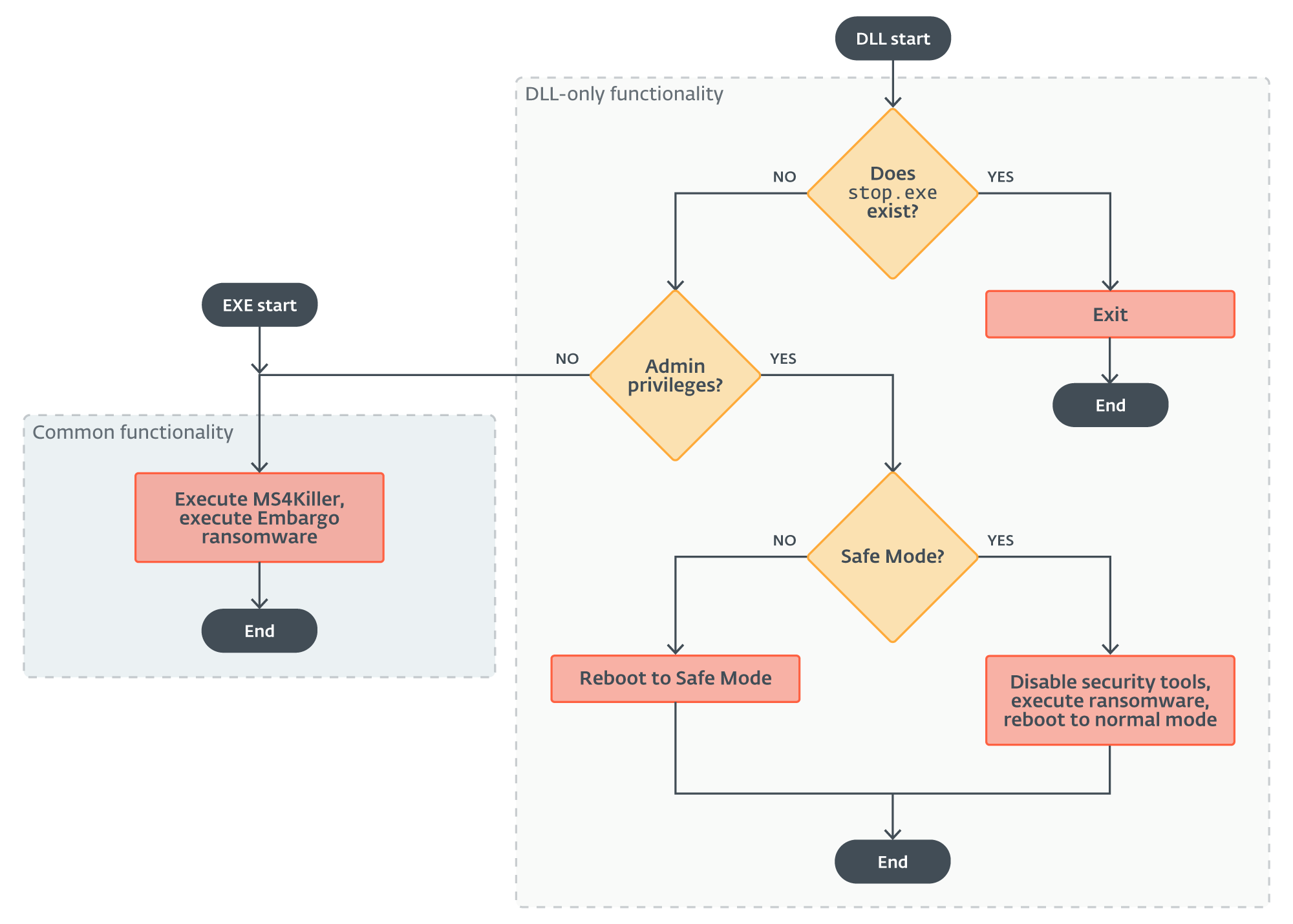
The primary distinction occurs proper firstly of the DLL execution – this model truly checks whether or not the file cease.exe exists. The existence of this file implies that MDeployer was already executed prior to now and both it efficiently deployed the ransomware payload or it exited with an error. So, if the file is discovered, the loader solely does its cleanup routine and exits. Notice that the EXE variations create the cease.exe file, however by no means test for its existence.
The following factor the DLL model of MDeployer does is to test whether or not it was executed with admin privileges. If it wasn’t, it goes on precisely just like the EXE model. Actually, the EXE variations had been probably compiled utilizing the supply code of this single execution department.
Nonetheless, if it was executed with admin privileges, the loader makes an attempt to reboot the sufferer’s system into Secure Mode so as to disable chosen safety options.
Secure Mode, a diagnostic mode of the Home windows OS, runs the system with solely minimal performance. Due to this, most cybersecurity measures and protections will not be in impact in Secure Mode, which supplies a possibility for risk actors to use it to keep away from detection. This system is thought amongst mature ransomware teams and has been abused prior to now, as reported by Forbes in 2022.
The safety-disabling performance occurs in two steps.
Step 1
The aim of step one is to reboot the system into Secure Mode. The loader achieves this utilizing a mix of Home windows command line instruments bcdedit, sc, and reg to:
- set Secure Mode because the default boot mode,
- disable Home windows Defender in Secure Mode,
- create a service, irnagentd, that executes the loader after the system is rebooted into Secure Mode, and
- restart the system.
Confer with the Instructions utilized by MDeployer part for the total checklist of instructions executed by the loader.
Step 2
As soon as in Secure Mode, the loader disables chosen safety instruments by renaming their set up directories, then executes the Embargo ransomware payload.
After that, it does a “Secure Mode cleanup” – it deletes the decrypted ransomware file pay.exe, creates the management movement file cease.exe to forestall double encryption, deletes the persistence service irnagentd, and reboots the system again into regular mode.
BAT disabler
In one of many incidents, we additionally noticed the additional performance of the DLL loader carried out as a BAT script. This script targets a single safety answer – a theme you’ll encounter once more, later on this article. It used the identical strategy of rebooting into Secure Mode with the assistance of a persistence service, irnagentd, after which renaming the put in safety software program’s set up listing. It even used the identical cease.exe file for management movement and logged error messages into fail.exe (fail.txt in MDeployer).
This once more reveals that Embargo modifies its instruments to go well with every sufferer’s setting.
Logging
In case MDeployer encounters any errors, it logs error messages into the file fail.txt after which creates the file cease.exe.
There are 4 levels that the attacker distinguishes of their log messages – they use a distinct prefix for logging errors in every of them:
- [dec] – payload decryption,
- [exec] – ransomware execution,
- [execk] – MS4Killer execution, and
- [kler] – MS4Killer run (this prefix is used when MS4Killer exits unexpectedly).
Within the DLL model there are extra log message prefixes in comparison with the EXE variations:
- [sc], [sc delete] – creating or deleting the service irnagentd,
- [reg], [reg-del] – modifying Home windows registry, and
- [setsb] – utilizing the bcdedit.exe command line instrument to set Secure Mode on subsequent restart.
Cleanup
MDeployer has a number of variants of a cleanup routine launched at completely different events. This occurs after the loader efficiently executes the ransomware payload, and likewise if any errors are encountered throughout loader execution.
Throughout cleanup, the loader terminates the MS4Killer course of, deletes the decrypted payloads and the weak driver dropped by MS4Killer, and creates the movement management file cease.exe.
In case the cleanup routine was prompted by the existence of cease.exe, MDeployer additionally deletes its personal PE file.
Lastly, it reboots the system by calling shutdown -r -f -t 00.
Execution
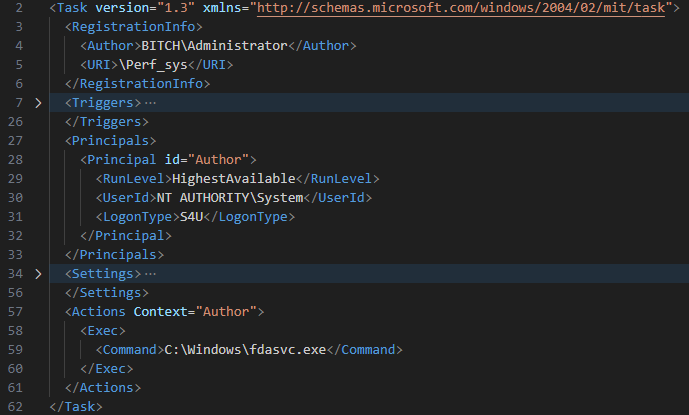
In all the noticed circumstances, the persistence of the loader was achieved by a scheduled activity, Perf_sys (Determine 5), created by an already elevated system consumer BITCHAdministrator.
In one of many circumstances, we additionally collected a PowerShell script resulting in the execution of MDeployer. The script was notably much like the one utilized by WinRM-fs, so we assume with medium confidence that Embargo used that or an analogous instrument to ship the loader from an unprotected machine.
Lively growth
There are a number of inconsistencies and examples of “messy management movement” within the loader samples we’ve seen thus far that recommend the group’s instruments are nonetheless in lively growth and never “manufacturing prepared”.
The truth that MDeployer deletes the weak driver dropped by MS4Killer is especially attention-grabbing as a result of it reveals that the 2 instruments are being developed collectively. And but there’s a partial overlap in performance – each MS4Killer and the DLL model of MDeployer try and disable safety options.
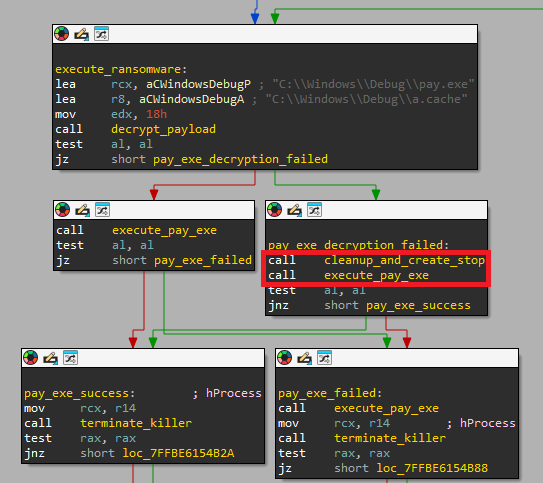
It’s not unusual to see the loader delete the payload recordsdata solely to aim to execute one among them instantly after. See Determine 6, the place MDeployer calls the cleanup operate, throughout which pay.exe is deleted, however then tries to execute that exact same file.
Actually, the DLL model of the loader we’ve seen comprises a number of bugs that stop it from working altogether. This might clarify why we’ve seen a number of variations of the loader being utilized in a single incident – the risk actor probably finds out about these issues as they go after which has to adapt on the fly.
MS4Killer
MS4Killer is a typical protection evasion instrument that terminates safety product processes utilizing the method often called Convey Your Personal Susceptible Driver (BYOVD). It’s written, much like the loader, in Rust. We consider that MS4Killer was closely impressed by s4killer, a proof of idea (POC) printed on GitHub, conveniently additionally written in Rust. Because of the resemblance with this current POC, we consult with this instrument as MS4Killer – brief for EMbargo s4killer.
Extending the performance
s4killer is designed to pick a operating course of and terminate it from the kernel. It does so by putting in and abusing a weak driver that’s saved in a world variable (.rdata part within the compiled code). The PID of the method to terminate is handed to s4killer as a program argument. The termination is carried out by way of FilterConnectCommunicationPort and FilterSendMessage from the minifilter API.
Embargo prolonged the POC performance with the next options:
- MS4Killer runs in an infinite loop, continuously scanning for operating processes.
- The checklist of course of names to kill is hardcoded within the binary.
- The embedded driver blob is encrypted utilizing RC4.
- Binary strings are encrypted utilizing easy XOR, specifically log messages, course of names, and the RC4 key used for driver decryption.
- Throughout the course of termination part, MS4Killer spawns itself as a toddler course of, passing the PID of the method to kill as an argument.
- Course of scanning and course of termination are cut up into a number of threads by using Rayon, an information parallelism library for Rust.
BYOVD
Convey your individual weak driver is a well-known method the place a risk actor abuses signed, weak kernel drivers to achieve kernel-level code execution. Ransomware associates typically incorporate BYOVD tooling of their compromise chain to tamper with safety options defending the infrastructure being attacked. After disabling the safety tooling, associates can run the ransomware payload with out worrying whether or not their payload will get detected.
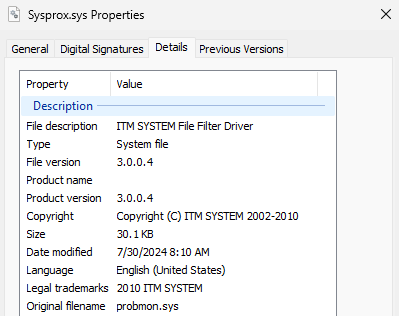
On this specific case, MS4Killer abuses an older, weak minifilter driver: probmon.sys, model 3.0.0.4 (Determine 7), signed by an already revoked certificates from ITM System Co.,LTD. The driving force is embedded within the MS4Killer binary as an RC4-encrypted blob. We reported the ITW misuse of this driver to Microsoft.
String decryption
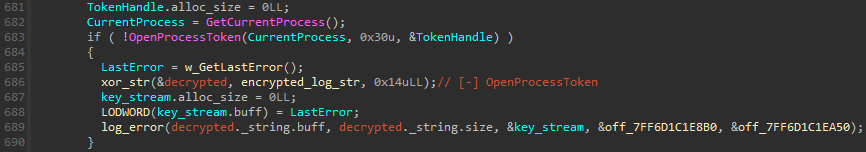
MS4Killer makes use of encryption to cover embedded strings within the binary from plain sight: particularly, it XORs log message strings, the RC4 key used to decrypt the embedded driver, and the checklist of course of names to terminate. Determine 8 reveals an instance of log message decryption, the place the Home windows OpenProcessToken API is known as. If the operate fails, a user-defined operate (renamed to xor_str in Determine 8) decrypts the XORed string and shops the outcome, [-] OpenProcessToken, into its first argument handed by reference. The decrypted string, appended with error info, is then written to plain out.
Loading probmon.sys
As talked about beforehand, the official weak driver is embedded as an RC4-encrypted blob (utilizing the important thing FGFOUDa87c21Vg+cxrr71boU6EG+QC1mwViTciNaTUBuW4gQbcKboN9THK4K35sL), which can be XOR encrypted, within the MS4Killer binary. We’ve noticed two completely different file paths the place MS4Killer drops the weak driver:
- C:WindowsSystem32driversSysprox.sys (Determine 9)
- C:WindowsSysmon64.sys
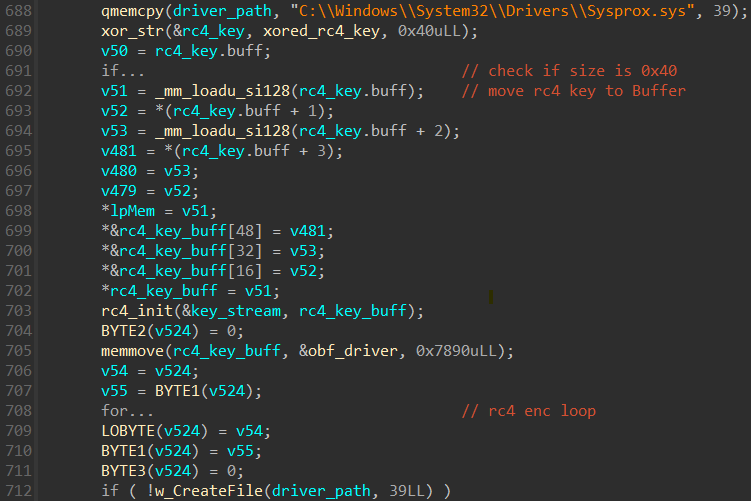
Driver loading is in keeping with s4killer:
- enabling the SeLoadDriverPrivilege needed for loading and unloading system drivers,
- making a service by way of CreateServiceW,
- creating extra registry keys, required for filter loading, in HKLMSYSTEMControlSet001services
, and - loading a minifilter driver into the system by way of FilterLoad.
We’ve noticed MS4Killer use three completely different service names thus far: Sysprox, Proxmon, and Sysmon64.
Hidden course of checklist
MS4Killer continuously compares operating processes towards an embedded checklist of safety software program course of names, that are additionally XOR-encrypted. Proper after the motive force hundreds, MS4Killer decrypts the checklist of course of names (Determine 10).
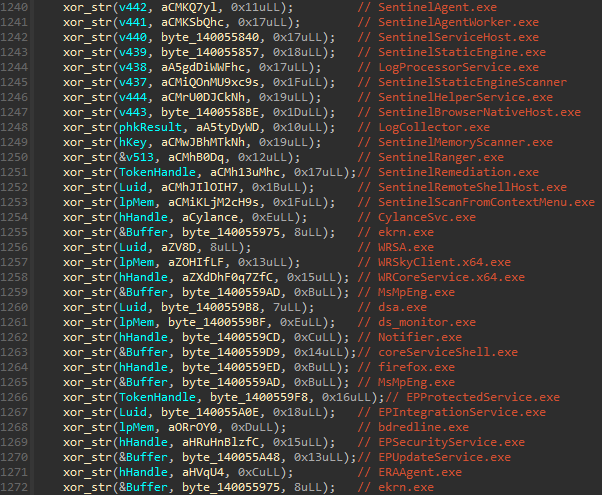
These course of names reference processes from a number of safety merchandise (see additionally Appendix: Instance of MS4Killer termination course of checklist). The code snippet in Determine 10 reveals that there are duplicates within the course of names (like ekrn.exe), among the strings are decrypted to the identical location (see the variables hHandle, Luid, and lpMem) and there’s one dummy course of title: firefox.exe. Moreover, following the cross-references of decrypted string variables results in comparability logic, the place solely a subset of course of names is utilized. Determine 11 reveals a code snippet, the place, in that specific case, solely course of names ERAAgent.exe and ekrn.exe, that are from ESET merchandise, are in contrast towards the operating processes. Shut inspection of a number of MS4Killer samples reveals that, in every intrusion, solely processes of a specific safety answer are monitored, regardless of the embedded course of checklist all the time containing course of names from a number of safety merchandise.
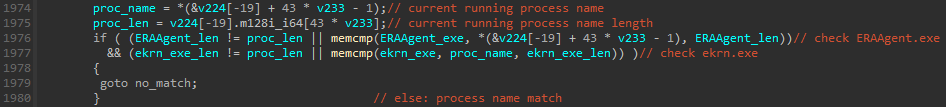
We noticed proof suggesting that MS4Killer samples had been compiled shortly earlier than the precise assaults and focused solely the safety answer defending the sufferer’s machine.
Conclusion
On this blogpost, we’ve supplied an evaluation of recent Rust instruments that we named MDeployer and MS4Killer, that are actively utilized by the brand new ransomware group – Embargo. Embargo is a brand new participant within the ransomware area, with the ambition to rise to the extent of the seasoned gangs. We’ve supplied arguments for why we consider that the Embargo group provides RaaS.
The principle objective of the Embargo toolkit is to safe profitable deployment of the ransomware payload by disabling the safety answer within the sufferer’s infrastructure. Embargo places a number of effort into that, replicating the identical performance at completely different levels of the assault (BAT script, MDeployer, and MS4Killer all include security-solution-disabling performance). We’ve additionally noticed the attackers’ capability to regulate their instruments on the fly, throughout an lively intrusion, for a specific safety answer.
Each MDeployer and MS4Killer are written in Rust. The identical is true for the ransomware payload, suggesting Rust is the go-to language for the group’s builders. We’ve noticed deployment of two completely different variations of MDeployer throughout one incident. The deployed loader additionally contained logical bugs that disrupted the correct performance of the instrument. Primarily based on the best way the instruments are tweaked throughout intrusions and the closeness of the compilation timestamps to the instances of intrusions, we assume that the attacker deploying the instruments has the flexibility to rapidly modify the supply code and recompile their instruments throughout an intrusion.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides personal APT intelligence studies and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
Recordsdata
| SHA-1 | Filename | Detection | Description |
| A1B98B1FBF69AF79E5A3 |
dtest.dll | Win64/Agent.ECY | MDeployer – loader deploying MS4Killer and Embargo ransomware. |
| F0A25529B0D0AABCE9D7 |
fxc.exe | Win64/Agent.ECY | MDeployer – loader deploying MS4Killer and Embargo ransomware. |
| 2BA9BF8DD320990119F4 |
fdasvc.exe | Win64/Agent.ECY | MDeployer – loader deploying MS4Killer and Embargo ransomware. |
| 888F27DD2269119CF952 |
praxisbackup.exe | Win64/Agent.ECW | MS4Killer – Embargo EDR Killer. |
| BA14C43031411240A083 |
praxisbackup.exe | Win64/Agent.ECW | MS4Killer – Embargo EDR Killer. |
| 8A85C1399A0E404C8285 |
pay.exe | Win32/Filecoder.Embargo.A | Embargo ransomware. |
| 612EC1D41B2AA2518363 |
win32.exe | Win32/Filecoder.Embargo.A | Embargo ransomware. |
| 7310D6399683BA3EB2F6 |
Sysmon64.sys | Win64/ITMSystem.A | Respectable weak driver, probmon.sys, dropped and utilized by MS4Killer. |
| 7310D6399683BA3EB2F6 |
Sysprox.sys | Win64/ITMSystem.A | Respectable weak driver, probmon.sys, dropped and utilized by MS4Killer. |
Certificates
| Serial quantity | 010000000001306DE166BE |
| Thumbprint | A88758892ED21DD1704E5528AD2D8036FEE4102C |
| Topic CN | ITM System Co.,LTD |
| Topic O | ITM System Co.,LTD |
| Topic L | Guro-gu |
| Topic S | N/A |
| Topic C | KR |
| Legitimate from | 2011-06-08 06:01:39 |
| Legitimate to | 2014-06-07 08:32:23 |
Extra MDeployer file paths
- C:WindowsDebugb.cache
- C:WindowsDebuga.cache
- C:WindowsDebugfail.txt
- C:WindowsDebugstop.exe
Instructions utilized by MDeployer
- reg delete HKLMSYSTEMCurrentControlSetControlSafebootNetworkWinDefend /f
- C:WindowsSystem32cmd.exe /c takeown /R /A /F “C:ProgramData[redacted]” /D Y
- C:WindowsSystem32cmd.exe /c takeown /R /A /F “C:Program Recordsdata[redacted]” /D Y
- sc create irnagentd binpath=”C:WindowsSystem32cmd.exe /c begin /B rundll32.exe C:WindowsDebugdtest.dll,Open” begin=auto
- sc delete irnagentd
- reg add HKLMSYSTEMCurrentControlSetControlSafebootNetworkirnagentd /t REG_SZ /d Service /f
- C:WindowsSystem32cmd.exe /c bcdedit /set {default} safeboot Minimal
- C:WindowsSystem32cmd.exe /c bcdedit /deletevalue {default} safeboot
- reg delete HKLMSYSTEMCurrentControlSetControlSafebootNetworkWinDefend /f
- C:WindowsSystem32cmd.exe /c ping localhost -n 5 > nul & del C:WindowsDebugdtest.dll
- shutdown -r -f -t 00
- C:Windowspraxisbackup.exe
- C:WindowsDebugpay.exe
MITRE ATT&CK methods
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Useful resource Growth | T1587.001 | Develop Capabilities: Malware | Embargo group develops its customized toolkit – MDeployer, MS4Killer, and Embargo ransomware. |
| Execution | T1059.003 | Command-Line Interface: Home windows Command Shell | Embargo group executes a BAT script that disables safety options. |
| T1059.001 | Command-Line Interface: PowerShell | Embargo group makes use of PowerShell to switch MDeployer to victims’ machines. | |
| T1053.005 | Scheduled Activity/Job: Scheduled Activity | Embargo group makes use of scheduled duties to run MDeployer on compromised endpoints. | |
| T1569.002 | System Companies: Service Execution | Embargo group makes use of a Home windows service to execute MDeployer in Secure Mode. | |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Embargo group modifies the Home windows registry to start out a customized service in Secure Mode. |
| T1136.002 | Create Account: Area Account | Embargo group creates its personal area accounts. | |
| Protection Evasion | T1562.001 | Impair Defenses: Disable or Modify Instruments | MDeployer, MS4Killer, and a BAT script disable safety options. |
| T1562.009 | Impair Defenses: Secure Mode Boot | MDeployer and a BAT script reboot into Secure Mode. | |
| T1070.004 | Indicator Removing: File Deletion | MDeployer deletes dropped recordsdata throughout cleanup. | |
| T1112 | Modify Registry | MS4Killer modifies the registry to load a official weak driver. | |
| T1027.013 | Obfuscated Recordsdata or Data: Encrypted/Encoded File | Payloads loaded by MDeployer are RC4 encrypted. | |
| Discovery | T1135 | Community Share Discovery | Embargo ransomware performs community share discovery. |
| T1083 | File and Listing Discovery | Embargo ransomware performs file and listing discovery. | |
| Affect | T1490 | Inhibit System Restoration | Embargo ransomware disables computerized Home windows restoration. |
| T1486 | Knowledge Encrypted for Affect | Embargo ransomware encrypts recordsdata on compromised machines. |
Appendix: Instance of MS4Killer termination course of checklist (in alphabetical order)
| SentinelAgent.exe SentinelAgentWorker.exe SentinelServiceHost.exe SentinelStaticEngine.exe LogProcessorService.exe SentinelStaticEngineScanner.exe SentinelHelperService.exe SentinelBrowserNativeHost.exe LogCollector.exe SentinelMemoryScanner.exe SentinelRanger.exe SentinelRemediation.exe SentinelRemoteShellHost.exe SentinelScanFromContextMenu.exe CylanceSvc.exe ekrn.exe WRSA.exe |
WRSkyClient.x64.exe WRCoreService.x64.exe MsMpEng.exe dsa.exe ds_monitor.exe Notifier.exe coreServiceShell.exe firefox.exe MsMpEng.exe EPProtectedService.exe EPIntegrationService.exe bdredline.exe EPSecurityService.exe EPUpdateService.exe ERAAgent.exe ekrn.exe |


