
Virtually each week we add one other workflow to our automation library. Our platform and copilot are serving to folks automate in any other case tedious duties in safety operations. Integrations between platforms historically concerned safety engineers writing customized code utilizing software programming interfaces (APIs).
For instance, if you happen to wished to scan all of your S3 buckets for public entry, on the lookout for READ and WRITE permissions, and ship a notification to an incident response Slack channel, you would want Python or Bash code with many API calls.
Nevertheless, with safety automation platforms like Blink Ops, this has drastically modified. You’ll be able to combine automation into your setting by writing a easy immediate, and the copilot will construct the workflow it thinks you want. It is then a matter of getting into a couple of parameters and including authentication credentials. This will save folks in safety operations lots of of hours a 12 months.
Listed under are 5 incident response/safety operations workflows you possibly can automate with Blink Ops. These examples offer you an thought of how Blink Ops automations can pace up your work.
1. Monitoring for Subdomain Takeover with AWS and Wiz
Subdomain takeover happens when a DNS entry factors to a nonexistent or inactive useful resource, permitting attackers to hijack the area. Making an attempt to forestall this manually entails frequent checks to make sure all DNS configurations are right.
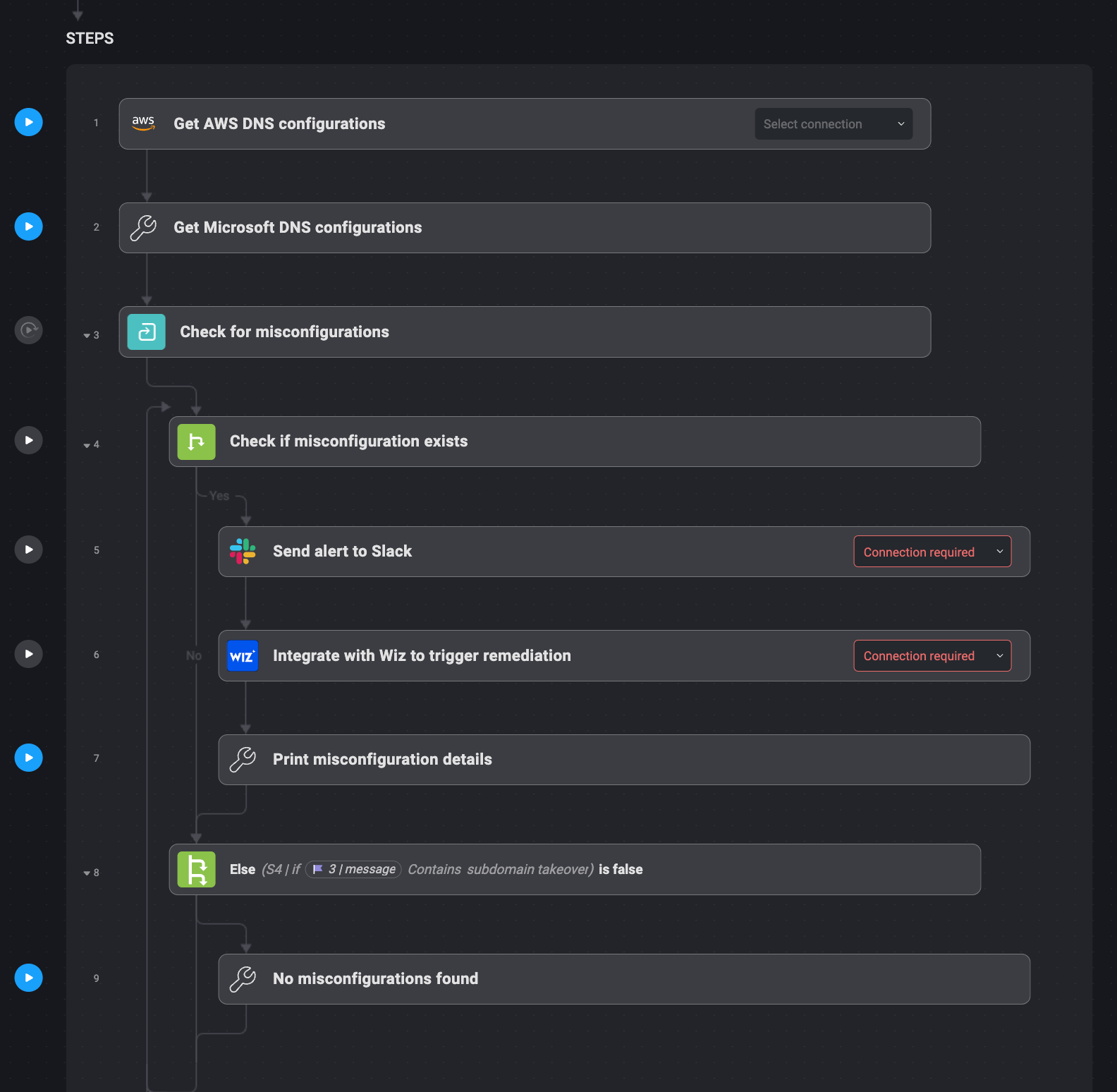
This course of is totally automated utilizing Blink Ops. Along side AWS Route 53, Blink Ops scans for orphaned/dangling CNAME data pointing to sources that now not exist utilizing Wiz. Upon detection of points, Blink Ops sends a right away alert to a delegated Slack channel describing the misconfigured DNS entry.
Wiz then quarantines the report or takes remediation steps. When no points are discovered, a notification is shipped that all the things is safe. This automation simplifies detection and mitigation of subdomain takeover dangers.
Bullet-Level Steps:
1. For DNS configurations, Blink Ops connects to AWS Route 53.
2. Wiz checks DNS entries for dangling orphaned CNAME data.
3. When a susceptible report is discovered, Blink Ops sends an alert to Slack.
4. Wiz both quarantines the report or applies the repair.
5. If no issues are discovered, a affirmation e-mail is shipped confirming this.
2. Monitoring for Uncovered S3 Buckets with Slack Alerts
Uncovered S3 buckets are a big safety threat for any group, and monitoring them manually each day will be tedious. You may handle this by enabling every day computerized scans of S3 buckets with public READ permissions.
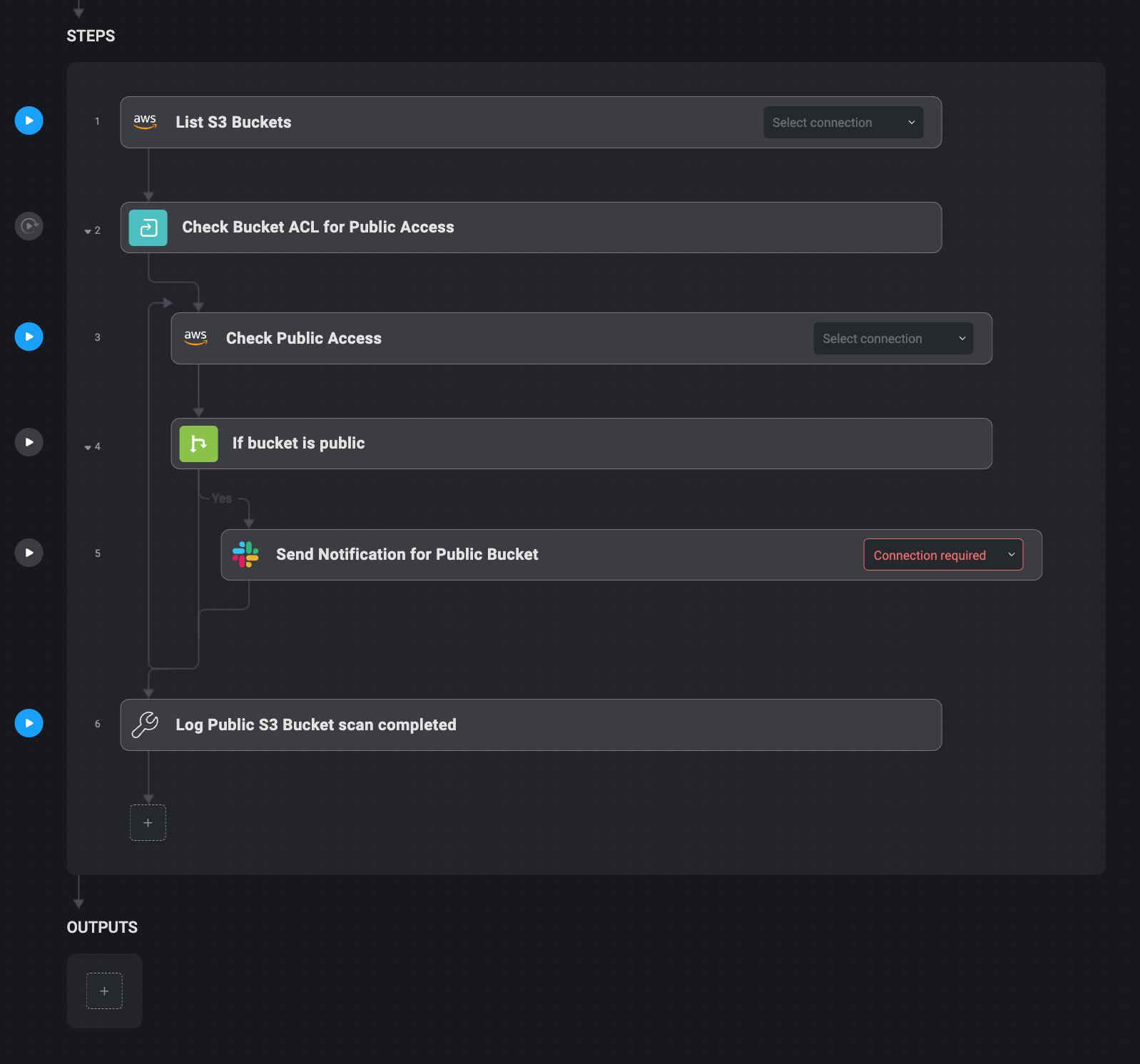
This workflow integrates with AWS S3, and Blink Ops can scan every bucket marked for public entry. Detecting a bucket with public READ entry triggers a Slack alert from Blink Ops, giving the safety workforce details about the bucket — together with its title and permissions.
A follow-up motion by Blink Ops also can take away the general public permission for the bucket. This workflow identifies uncovered buckets shortly and appropriately in order that delicate information just isn’t uncovered to unauthorized customers.
Bullet-Level Steps:
1. Day by day, Blink Ops checks AWS S3 buckets for public learn permissions.
2. Any bucket discovered with public READ entry triggers a Slack alert.
3. Blink Ops can optionally revoke READ permissions (notice – not included above).
4. The bucket is secured, and the safety workforce is notified.
3. Responding to Failed EC2 Logins and Privilege Escalation
Failed login makes an attempt and unauthorized privilege escalation detection and response on EC2 cases are vital to safety. Blink Ops can automate this in order that threats are detected in real-time and responded to.
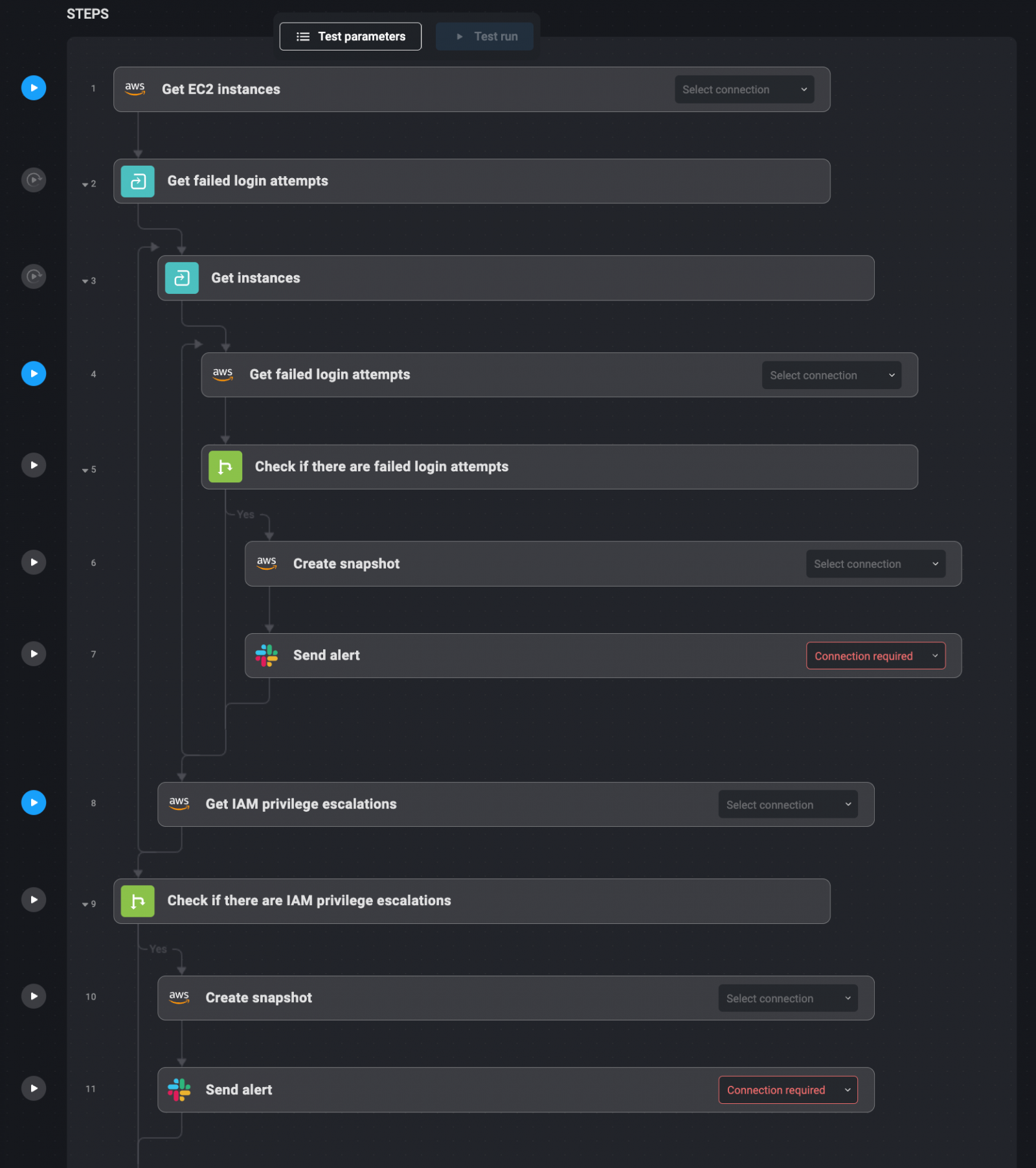
You’ll be able to monitor EC2 cases to disclose repeated failed SSH or RDP login makes an attempt—5 or extra failed makes an attempt in a 15-minute window—by way of Slack. You may also monitor privilege escalation by monitoring IAM function modifications, like when an EC2 occasion is granted further privileges like AdminAccess.
When this occurs, Blink Ops takes a snapshot of the affected EC2 occasion for forensic evaluation and sends an alert to the safety workforce describing what occurred. This automation relieves safety groups of handbook log monitoring throughout login failures or privilege abuse.
Bullet-Level Steps:
1. Failed SSH and RDP login makes an attempt on EC2 cases are tracked by Blink Ops.
2. If > 5 failed logins happen inside quarter-hour, Blink Ops points a Slack alert.
3. IAM function modifications similar to privilege escalation are additionally tracked by Blink Ops.
4. When privilege escalation happens, Blink Ops takes a snapshot.
5. Safety groups obtain alerts with all related particulars concerning the occasion.
4. Vulnerability Detection and Alerting with AWS Inspector
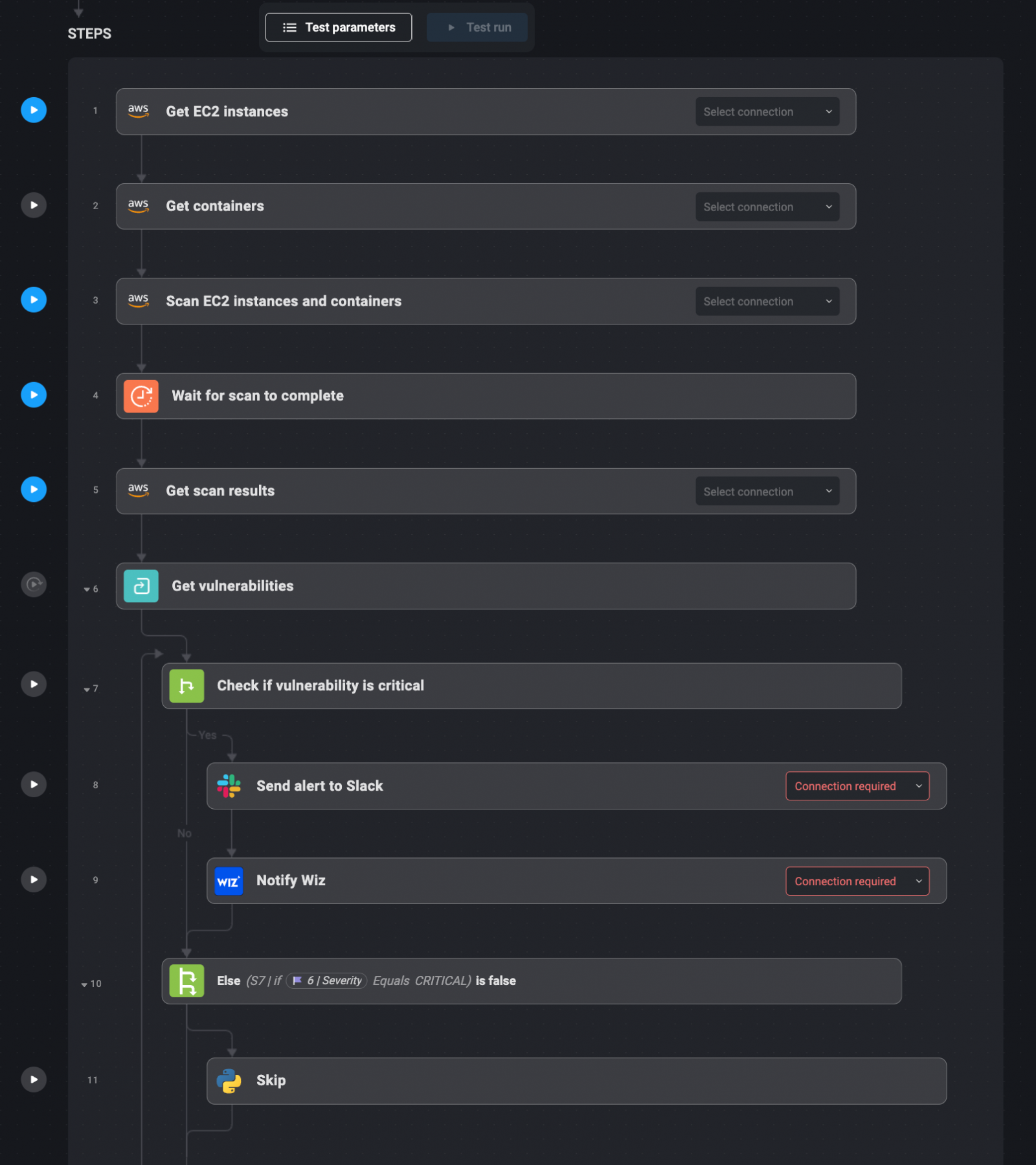
Vulnerability administration is important for conserving cloud environments safe. Blink Ops simplifies the method by integrating with AWS Inspector to routinely scan EC2 cases and containers for vital vulnerabilities.
As a part of Blink Ops, AWS Inspector can verify for high-severity vulnerabilities similar to CVSS scores higher than 7. As soon as a vital vulnerability is detected, Blink Ops notifies the designated Slack channel of the susceptible occasion/container. The alert additionally hyperlinks to a remediation information or playbook for handbook intervention.
For vulnerabilities that can’t be routinely patched, Blink Ops logs the main points and permits for handbook remediation by a safety engineer. As soon as the remediation is full, Wiz verifies that the vulnerability has been mounted, making certain that the cloud setting is safe.
Bullet-Level Steps:
1. AWS Inspector scans EC2 cases and containers for vulnerabilities.
2. Upon discovery of a vulnerability (CVSS >7), Blink Ops sends an alert to Slack.
3. Wiz confirms that the vulnerability was mounted after handbook remediation.
4. Safety groups are notified of the repair and verification course of completion.
5. Automating S3 Encryption Enforcement with AWS and Wiz
Securing delicate information in S3 buckets is finest apply. That is solved by automating S3 bucket monitoring for encryption compliance with Blink Ops.
Monitoring of sensitive-data tagged S3 buckets by way of Blink Ops is built-in with AWS Config. It verifies that such buckets are encrypted with AES-256. Upon detection of an unencrypted bucket, Blink Ops applies AES-256 encryption utilizing AWS’s PutBucketEncryption API.
After encryption has been utilized, Blink Ops sends a Slack affirmation of the replace, and Wiz is triggered to confirm that encryption was utilized. Such an automatic workflow protects all delicate information with none human intervention and permits safety groups to implement encryption insurance policies throughout the cloud setting.
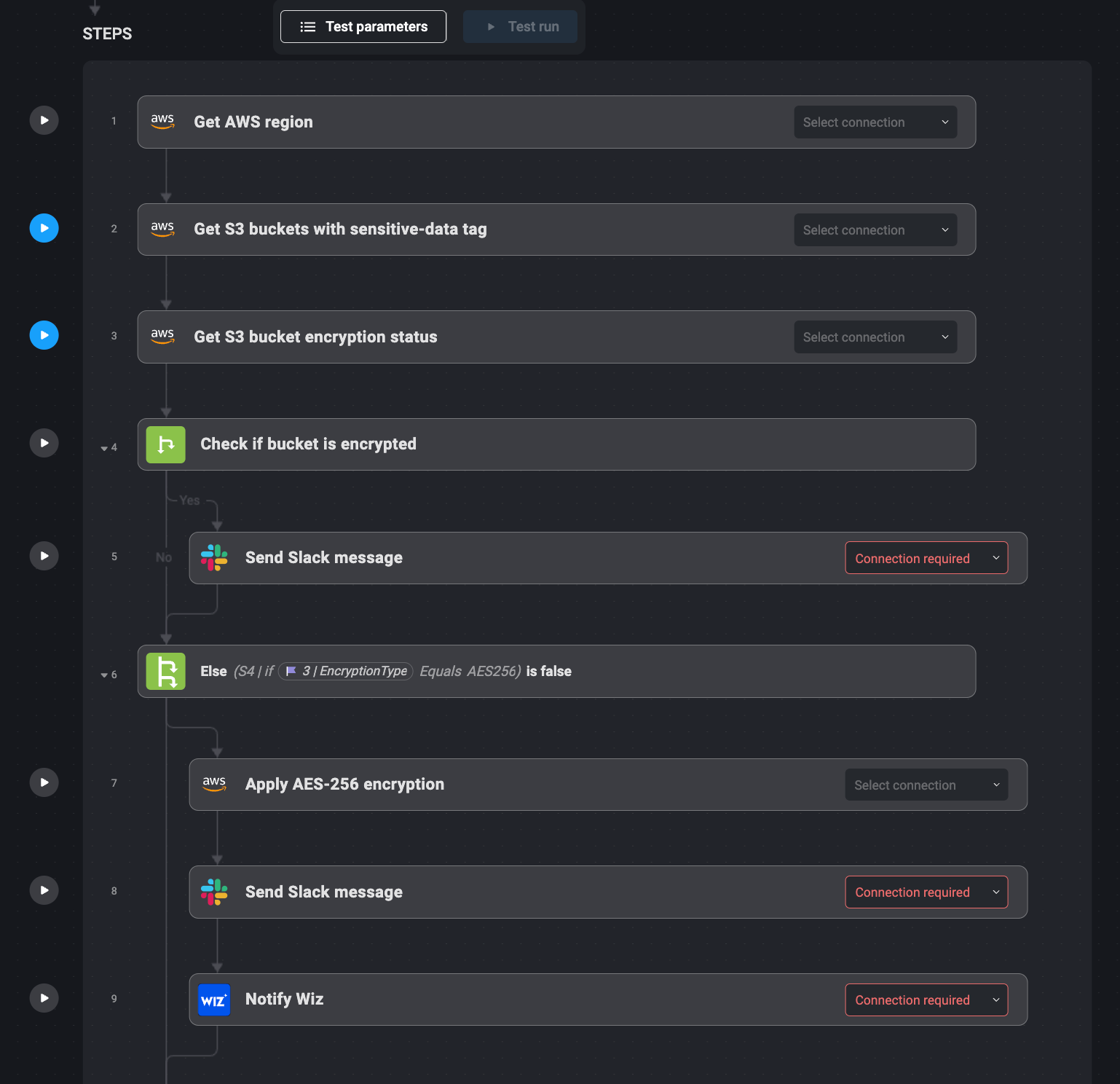
Bullet-Level Steps:
1. AWS Config tracks sensitive-data tagged S3 buckets monitored by Blink Ops.
2. If unencrypted, Blink Ops triggers AWS to use encryption.
3. When encryption is utilized, Slack notification is shipped.
4. Wiz confirms the encryption has been utilized accurately.
5. Safety groups now know the bucket is secured.
Take Your Subsequent Steps With Blink Ops
The use instances above are simply among the many potentialities that Blink Ops can automate for you. Blink Ops can be utilized with platforms like AWS and Wiz to automate processes that used to require customized code and handbook labor. This implies safety groups can save hours, reply quicker to threats, and scale back human error threat.
Automate time-consuming duties so your workforce can deal with higher-value safety initiatives—utilizing Blink Ops. Whether or not you should monitor for subdomain takeover, detect failed EC2 logins, or automate vulnerability scans, Blink Ops permits you to optimize and scale your safety operations.
Get began with Blink Ops at the moment to automate repetitive duties.
Sponsored and written by Blink Ops.
