
North Korean IT professionals who trick Western firms into hiring them are stealing information from the group’s community and asking for a ransom to not leak it.
Dispatching IT staff to hunt employment at firms in wealthier nations is a tactic that North Korea has been utilizing for years as a method to acquire privileged entry for cyberattacks or to generate income for the nation’s weapons packages.
Researchers at cybersecurity firm Secureworks uncovered the extortion element throughout a number of investigations of such fraudulent schemes.
After the employment of a North Korean nationwide with entry to proprietary information (as a part of their contractor position) terminated, the corporate would obtain the primary extortion electronic mail, the researchers clarify.
To acquire the job and keep away from elevating suspicions afterwards, the fraudulent IT staff used a false or stolen id and relied on laptop computer farms to route site visitors between their actual location and the corporate by way of a U.S.-based level.
In addition they prevented video throughout calls or resorted to numerous methods whereas on the job to cover their face throughout video conferences, comparable to utilizing synthetic intelligence instruments.
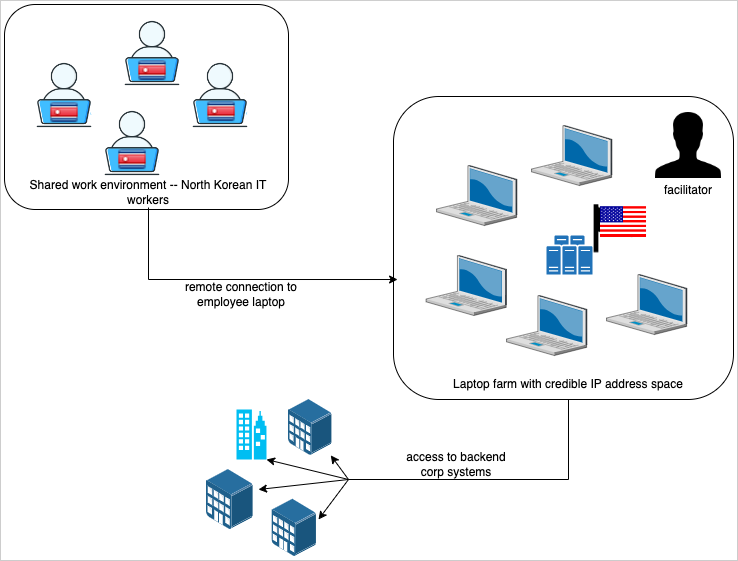
Supply: Secureworks
In July, American cybersecurity firm KnowBe4 revealed that they have been among the many a whole bunch of victimized firms, and of their case, the risk actor tried to put in an infostealer on the corporate’s laptop.
Secureworks tracks the group organizing and coordinating North Korea’s IT employee military as “Nickel Tapestry,” whereas Mandiant makes use of the UNC5267 title.
One instance of a Nickel Tapestry marketing campaign in mid-2024 that Secureworks investigated is that of an organization that had proprietary information stolen virtually instantly after using an exterior contractor
The information was transferred to a private Google Drive cloud storage utilizing the corporate’s digital desktop infrastructure (VDI).
After terminating the employment as a consequence of poor efficiency, the corporate started receiving extortion emails from exterior Outlook and Gmail addresses containing samples of the stolen information in ZIP archives.
The risk actors demanded a six-figure ransom to be paid in cryptocurrency in change to not leaking the information publicly.
Secureworks’ investigation revealed that Nickel Tapestry had used Astrill VPN and residential proxies to masks their actual IP handle in the course of the malicious actions, whereas AnyDesk was used for distant accessing the methods.
The researchers warn that North Korean IT staff typically coordinate to refer each other to firms.
Organizations ought to be cautious when hiring distant staff or freelancers, and search for indicators of fraud like adjustments in fee accounts and laptop computer cargo addresses, submission of generic-looking resumes, atypical correspondence hours, and unwillingness to allow digital camera throughout interviews.
