Apple gives security measures in macOS to offer apps entry to information in your native storage and detachable drives. Here is the right way to configure them.
Years in the past, Apple added the flexibility for macOS to limit which apps can entry your information and folders saved on native volumes hooked up to your Mac.
Some apps, resembling Finder, require this entry. However within the case of third-party apps, it’s possible you’ll or might not need them to have entry to your information.
macOS has preferences in System Settings for permitting or denying apps entry to your information.
Some apps can even entry detachable volumes resembling USB thumb drives, or CD/DVD volumes when inserted right into a Mac’s DVD drive.
You can too set which apps have entry to removables in System Settings. Not all apps present this functionality, and in the event that they do, the apps and their settings will present up within the System Settings->Safety & Privateness pane.
Apps should be constructed with entry
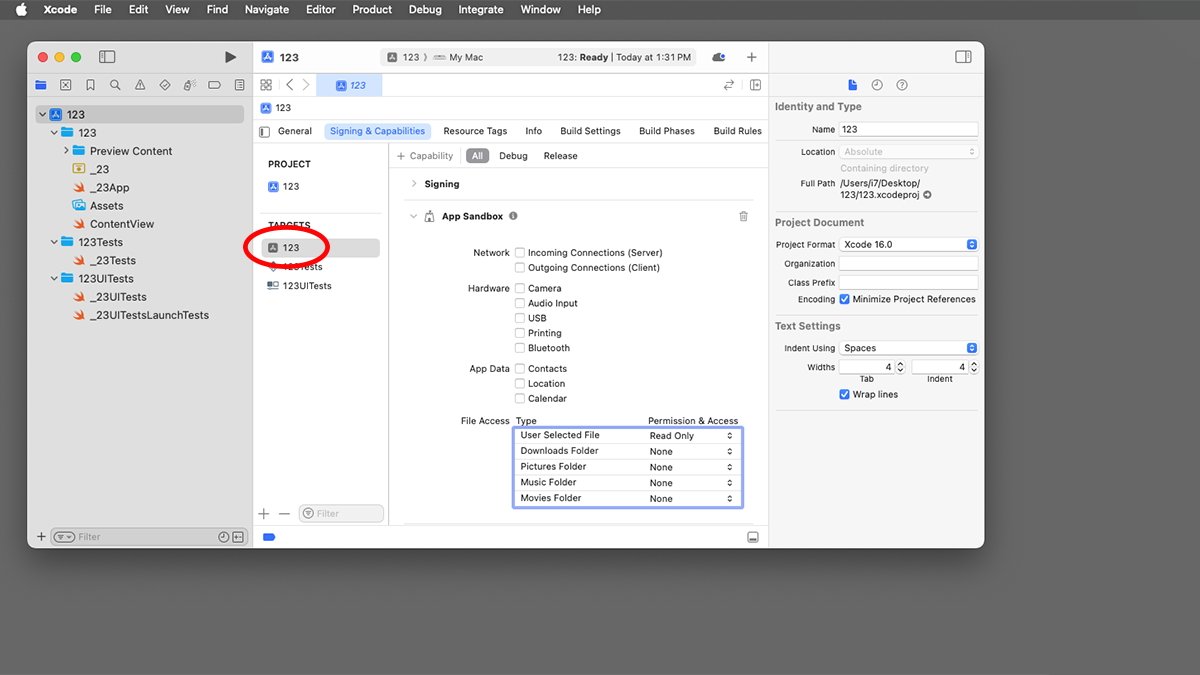
When Mac apps are constructed utilizing Apple’s Xcode developer surroundings, particular safety settings are included in every app’s bundle. These are based mostly on how a developer has configured these settings in Xcode.
Certainly one of these settings is whether or not or to not permit entry to information and folders.
If the app developer has included this setting when an app is constructed, then it is going to present up within the System Settings->Safety & Privateness->Recordsdata and Folders pane. If not, the app will not be listed there.
Particularly, these settings are configured in every construct goal’s Signing & Capabilities->App Sandbox->File Entry settings in Xcode:
The App Sandbox
The App Sandbox is a safety system constructed into macOS which by default partitions apps’ entry off from delicate elements of the system such because the filesystem and community. Apps are solely allowed to entry elements of the system that they’ve been given permission to entry.
These settings in Xcode embrace particular consumer folders resembling Downloads, Photos, Music, and so forth, however there’s additionally a setting for Consumer Chosen File.
It is this setting that permits a third-party app to let customers to pick out information to entry utilizing a regular macOS system Open file selector sheet. Builders can even specify whether or not to permit read-only entry or read-write entry.
The {Hardware}->USB checkbox in Xcode determines whether or not or to not permit apps to entry USB units, together with thumb drives.
How these settings are configured at app construct time determines whether or not they present up in System Settings for file and detachable entry.
Builders can even flip off all file entry totally, denying entry to information at a system safety stage no matter what APIs the app might name. There are additionally Sandbox settings for digital camera, audio, printing, and Bluetooth.
Because of this you might even see a macOS alert, for instance, the primary time you run a VOIP app resembling Skype or some gaming apps that need entry to your pc’s microphone.
Taken collectively, the App Sandbox settings prohibit or permit what sort of entry an app has to your Mac. Apple added these settings to macOS to forestall malware from having the ability to carry out actions resembling sending your complete Startup Disk’s contents to a malicious actor.
With the App Sandbox and different security measures, you do not have to fret as a lot about downloading a Mac app and having it seize all of your native knowledge the moment you run it.
All macOS apps distributed within the Mac App Retailer will need to have the Sandbox enabled in Xcode at construct time, even when all of the settings are turned off.
Altering entry settings
For file and folder entry, you possibly can toggle these settings in two locations within the System Settings app:
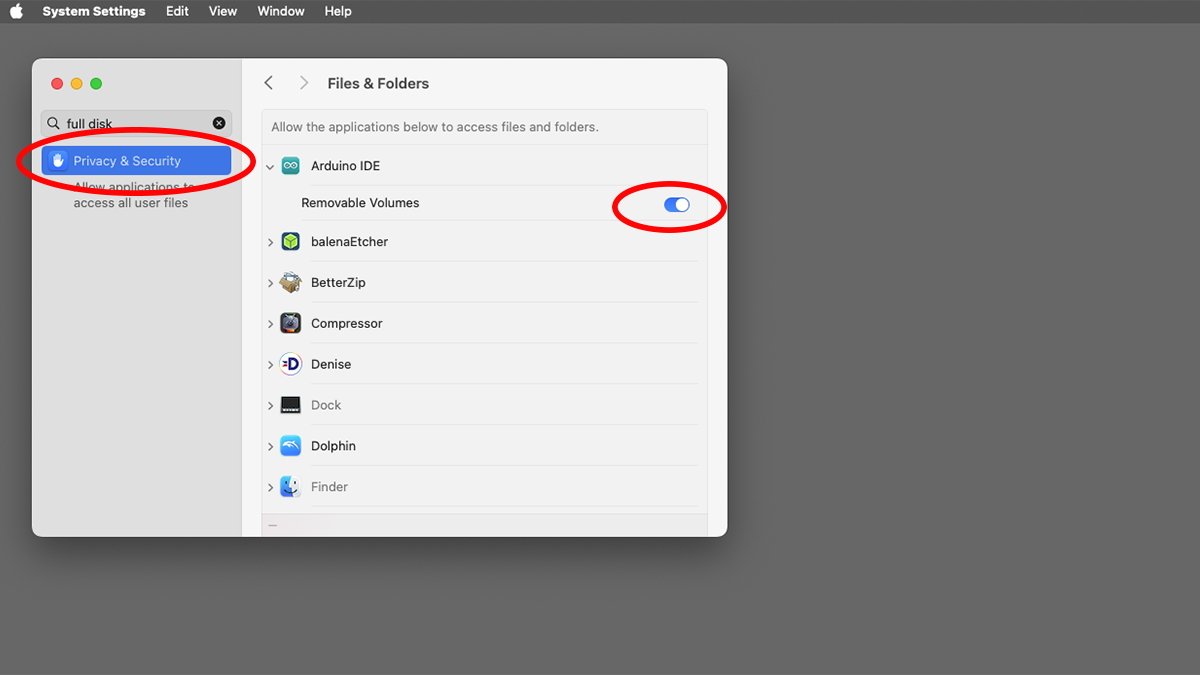
- System Settings->Safety & Privateness->Recordsdata and Folders
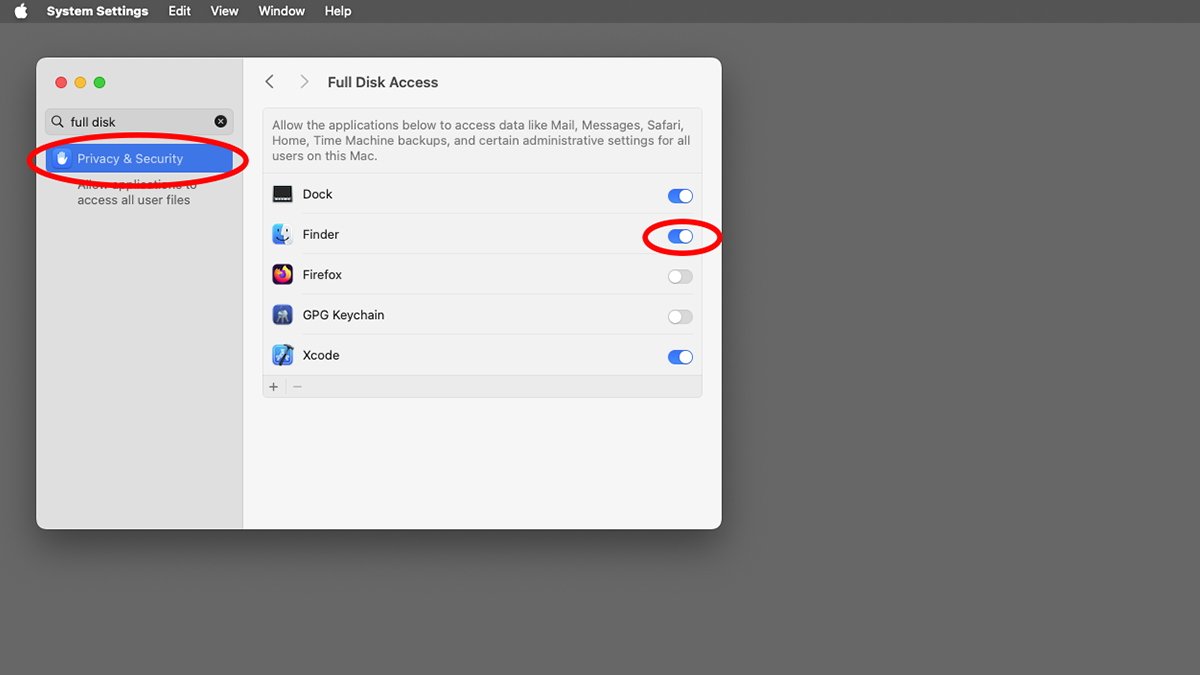
- System Settings->Safety & Privateness->Full Disk Entry
Within the case of Full Disk Entry, there isn’t any setting in Xcode within the App Sandbox. While you allow Full Disk Entry, you are giving an app entry to all of your Startup Disk’s information on the OS stage, not only for particular folders or user-selected information.
Full Disk Entry is a extra normal and critical stage of safety – so it is best to change Full Disk Entry fastidiously, since doing so offers the app in query free reign over your Mac’s Startup Disk.
Within the case of detachable drives, if an app is configured to permit entry to detachable volumes, an extra change will seem for that app within the Recordsdata and Folders pane. Not all apps might help removables.
You might also see extra switches for every of the consumer folders talked about above, and in some circumstances, the Desktop too. If the app requires or has Full Disk Entry turned on that title will seem alongside the app within the Recordsdata & Folders pane, however will probably be greyed out.
Clearly, when you grant an app Full Disk Entry, it does not want the person permission switches within the Recordsdata and Folders pane.
System Settings->Safety & Privateness->Full Disk Entry means that you can set which apps needs to be allowed to have full disk entry.
It’s potential to show off full disk entry for the Finder and the Dock apps. Nonetheless, it is in all probability finest to not since they’re each an integral a part of the Finder – and so they each come from Apple.
The one cause you may wish to flip entry for these apps off is if you’d like your Mac to function like a kiosk, or for instance, if you wish to prohibit file entry by youngsters.
Community-based apps specifically should not be granted full-disk entry since doing so creates a heightened safety danger. One instance is a malicious Java applet or extension downloaded by way of an online browser.
macOS additionally makes use of Gatekeeper and runtime safety to defend the core elements of the working system and its information from third-party apps. This ensures the system cannot be tampered with.
Gatekeeper additionally gives a stage of confidence that an app got here from its precise registered developer and is not faux.
Gatekeeper apps must be digitally signed by Xcode earlier than they are often distributed within the Mac App Retailer. If they’re tampered with the Finder will let you understand while you attempt to launch them.
The Mac App Retailer additionally employs Notarization and encrypted digital receipt verification to make sure downloaded Mac apps have not been compromised.
Total these safety settings assist improve the safety of your Mac and so they imply malware can have a a lot more durable time penetrating your Mac’s defenses. In addition they assist defend your personal information.
You may want to try these settings to make sure all of your apps are configured for max safety. Additionally, make sure you take a look at the Apple Platform Safety information.