A harmful potato: After researchers revealed the preliminary particulars of the Sinkclose safety challenge, AMD introduced {that a} firmware replace could be coming for a few of its desktop, cellular, and server CPUs. Nevertheless, in a stunning transfer, AMD has now determined to launch a brand new microcode replace for older Ryzen processors as effectively, although the precise motive for this resolution stays unclear.
Sinkclose is a probably severe safety vulnerability found by IOActive analysts in AMD’s x86 CPU know-how. This low-level bug impacts all processors launched by the Santa Clara-based company since 2006. Whereas AMD acknowledged IOActive’s analysis, the corporate initially determined to launch a microcode-based repair just for a few of its most up-to-date CPUs.
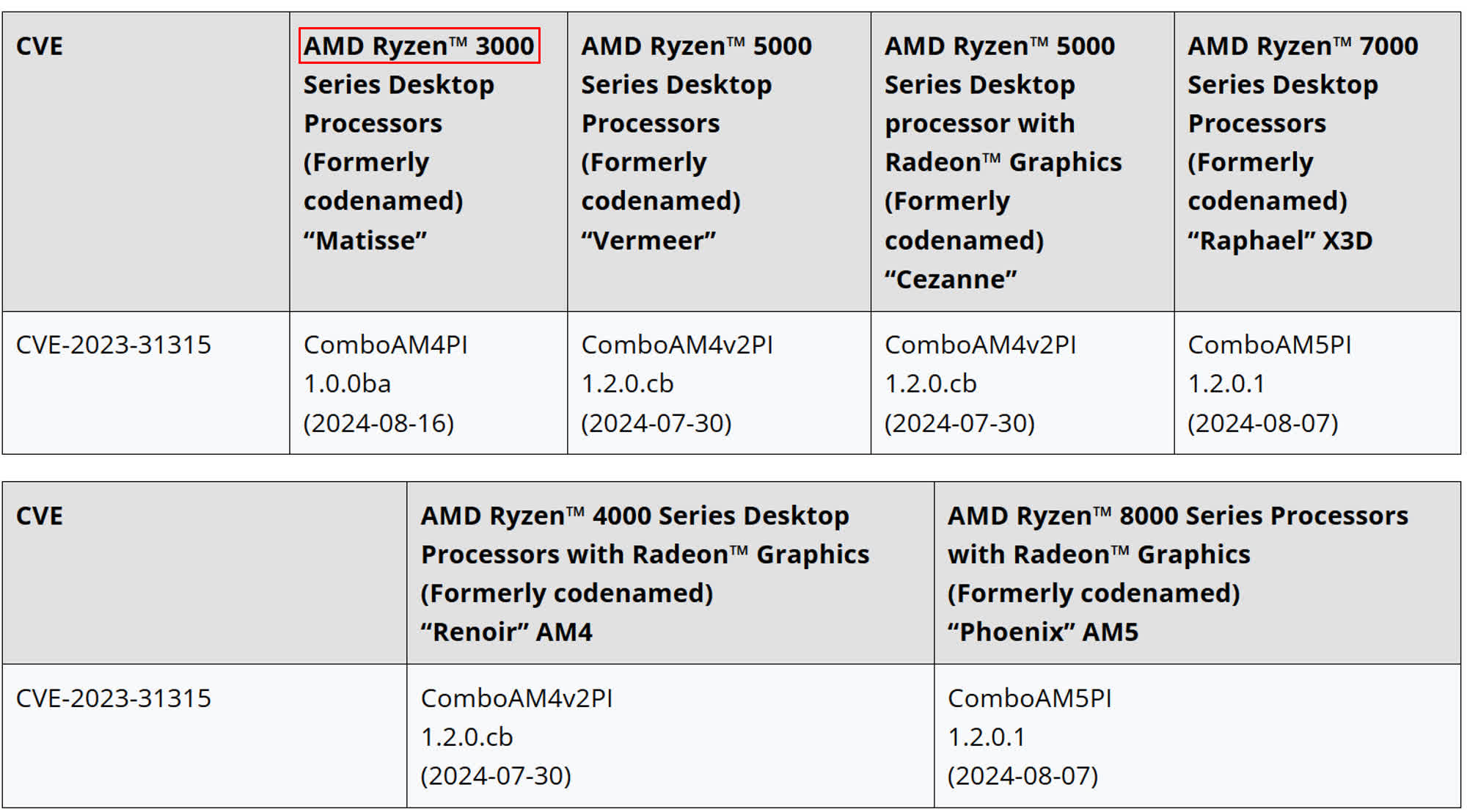
This resolution sparked vital controversy, as extensively used processors, some simply 5 years outdated, had been being left unprotected. In response to the backlash, AMD finally determined to handle the Sinkclose vulnerability in older Ryzen CPUs as effectively. The corporate just lately up to date its safety bulletin relating to the SMM Lock Bypass (CVE-2023-31315) challenge, which is the formal definition of the safety flaw informally often known as Sinkclose.
On August 14, AMD up to date its bulletin to supply a brand new “mitigation standing” for Ryzen 3000 desktop processors primarily based on the Matisse (Zen 2) microarchitecture. Though the corporate anticipated releasing a repair by August 20, the mitigation was really delivered on August 19. Homeowners of PCs utilizing Ryzen 3000 desktop CPUs ought to now search for the ComboAM4PI 1.0.0ba replace, which is being distributed by OEM motherboard producers by means of new firmware variations.
AMD describes CVE-2023-31315 as a “excessive” severity vulnerability that would result in arbitrary code execution throughout the System Administration Mode (SMM) surroundings, some of the privileged working modes in x86 CPUs. SMM know-how was first launched by Intel with the 386SL 32-bit processor as an influence administration function, whereas AMD carried out its model of SMM within the Am386 processors launched in 1991.
When the CPU is in SMM, regular code execution is suspended, and the working system is successfully paused. A malicious actor with ring 0 entry (Home windows kernel-level entry) may infect the PC’s firmware to execute code in SMM (ring -2) throughout boot, AMD confirms. This situation may successfully flip a bootkit into an invisible “ghost” throughout the system, making it extraordinarily troublesome – if not unattainable – to take away with out invasive {hardware} modifications.
AMD first launched its third-generation Ryzen processors in November 2019, providing PC customers a 15 % improve in IPC (directions per cycle) efficiency whereas decreasing vitality consumption. These CPUs retained compatibility with the AM4 socket utilized in earlier fashions and launched assist for PCI Categorical 4.0 connectivity.