
CISA has ordered U.S. federal companies to safe their methods in opposition to a not too long ago patched Home windows MSHTML spoofing zero-day bug exploited by the Void Banshee APT hacking group.
The vulnerability (CVE-2024-43461) was disclosed throughout this month’s Patch Tuesday, and Microsoft initially categorised it as not exploited in assaults. Nonetheless, Microsoft up to date the advisory on Friday to substantiate that it had been exploited in assaults earlier than being fastened.
Microsoft revealed that attackers exploited CVE-2024-43461 earlier than July 2024 as part of an exploit chain with CVE-2024-38112, one other MSHTML spoofing bug.
“We launched a repair for CVE-2024-38112 in our July 2024 safety updates which broke this assault chain,” it mentioned. “Prospects ought to each the July 2024 and September 2024 safety replace to completely defend themselves.”
Peter Girnus, the Pattern Micro Zero Day Initiative (ZDI) risk researcher who reported the safety flaw, instructed BleepingComputer that Void Banshee hackers exploited it in zero-day assaults to put in information-stealing malware.
The vulnerability permits distant attackers to execute arbitrary code on unpatched Home windows methods by tricking the targets into visiting a maliciously crafted webpage or opening a malicious file.
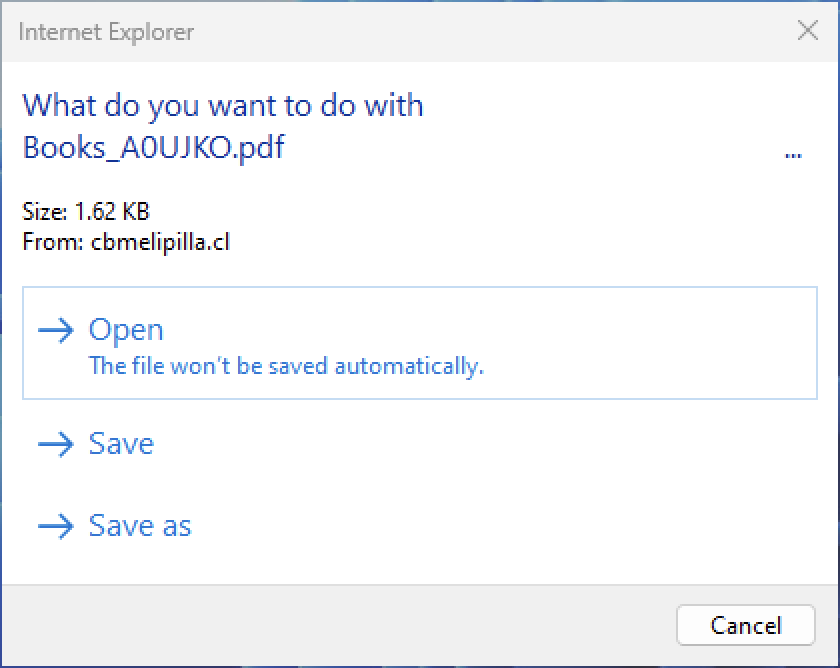
“The particular flaw exists inside the way in which Web Explorer prompts the consumer after a file is downloaded,” the ZDI advisory explains. “A crafted file identify may cause the true file extension to be hidden, deceptive the consumer into believing that the file kind is innocent. An attacker can leverage this vulnerability to execute code within the context of the present consumer.”
They used CVE-2024-43461 exploits to ship malicious HTA information camouflaged as PDF paperwork. To cover the .hta extension, they used 26 encoded braille whitespace characters (%E2percentA0percent80).
As revealed in July by Verify Level Analysis and Pattern Micro, the Atlantida information-stealing malware deployed in these assaults might help steal passwords, authentication cookies, and cryptocurrency wallets from contaminated gadgets.
Void Banshee is an APT hacking group first recognized by Pattern Micro and identified for concentrating on organizations throughout North America, Europe, and Southeast Asia for monetary achieve and to steal information.
Federal companies given three weeks to patch
At present, CISA has added the MSHTML spoofing vulnerability to its Identified Exploited Vulnerabilities catalog, tagging it as actively exploited and ordering federal companies to safe susceptible methods inside three weeks by October 7, as mandated by Binding Operational Directive (BOD) 22-01.
“Most of these vulnerabilities are frequent assault vectors for malicious cyber actors and pose important dangers to the federal enterprise,” the cybersecurity company mentioned.
Though CISA’s KEV catalog primarily focuses on alerting federal companies about safety flaws they need to patch as quickly as potential, non-public organizations worldwide are additionally suggested to prioritize mitigating this vulnerability to dam ongoing assaults.
Microsoft has patched three different actively exploited zero-days within the September 2024 Patch Tuesday. This consists of CVE-2024-38217, a vulnerability exploited in LNK stomping assaults since not less than 2018 to bypass the Good App Management and the Mark of the Net (MotW) safety characteristic.

